Bail attacks are on the rise, and it comes that the actors who disrupted this special kind of phishing emails prefer to use Gmail accounts to conduct their attacks. As per the report by one security researcher, who surveyed 10,500 organizations, 35% of them received at least one bait attack email in September 2021 alone.
What is a Baiting Attack?
A “bait attack” is a sub-class of phishing where the attacker tries to collect basic data about a specific target and utilize it for more targeted and effective attacks in the future. It is a previous reconnaissance step that hardly comes with payloads or embedded links on the email body.
Although some of these emails contain a basic question or something that has bigger chances of receiving a revert, many don’t include any text at all.
While it may be strange to send an almost empty email, the attacker is using them with the following intentions.
- Confirm that the recipient’s email address is valid
- Confirm that the email address is actively used
- Confirm targets’ susceptibility to unsolicited emails
- Test the effectiveness of automated spam-detection solutions
Since these emails don’t include any links to phishing sites and don’t carry any attachments, they usually pass through phishing defense systems as they are not seen as malicious.
Why only Gmail?
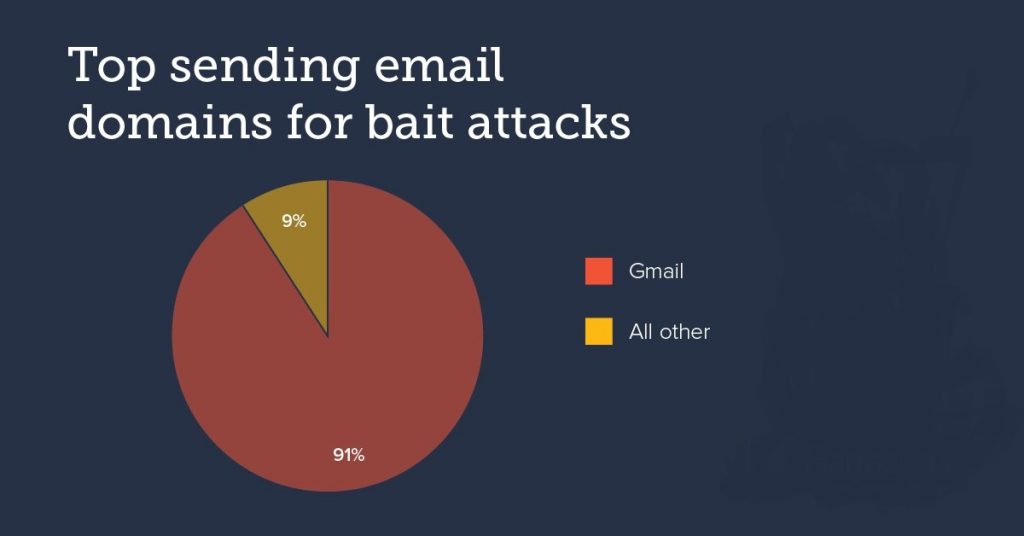
Our researchers also state that 91% of all these bait emails are sent from advance-created Gmail accounts, while all the other email platforms account for just 9%. This preference is because Gmail is a very well-known service that people associate with legitimacy and trustworthiness.
The same applies to email security solutions that treat Google’s email service as a highly reputable one. Moreover, Gmail is a platform that allows the quick and easy creation of pseudonymous accounts without much confusion.
Finally, Gmail supports “read receipt” functionality, which tells the actors that the recipient opened the message even if they never replied. This stealthily fulfills the purpose of the baiting attack, which is to confirm that the mailbox is valid and actively used.
What happens if the Bait is taken?
Our experts have decided to experiment by replying to these baiting emails, which aren’t supposed to initiate the phishing process. Within 48 hours, the security firm employee received a targeted phishing attack used after a false Norton LifeLock purchase claim.
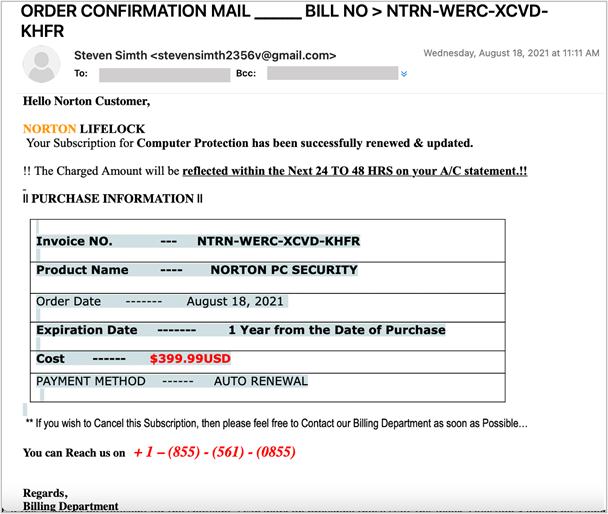
This quick response demonstrates the readiness of the actors and the tight connection between these innocuous-looking empty emails and fully-fledged phishing attacks.
Remember, one doesn’t even have to reply to these emails to confirm that they are available for potential exploitation, so if you see one, delete it without opening it. However, replying puts the victim in a higher priority category for the actors, as users who respond to bait emails are typically more susceptible and easier to exploit.



