Flaws in the employment of Microsoft Exchange’s Autodiscover feature have leaked around 100,000 login details for Windows domains across the world. A recent report by a security analyst indicates how the false implementation of the Autodiscover protocol, rather than a flaw in Microsoft Exchange, is causing Windows passwords to be forwarded to third-party unauthenticated websites.
Before discussing the issue, it is very essential to take a quick look at Microsoft Exchange’s Autodiscover protocol and how it is implemented.
What is Microsoft Exchange Autodiscover?
Microsoft Exchange utilizes an Autodiscover feature to automatically configure a user’s mail client, including Microsoft Outlook, with their organization’s predefined mail settings. When an Exchange user enters their email credentials into their email client, like Microsoft Outlook, the mail client then tries to authenticate to different Exchange Autodicover URLs.
While this authentication process, the credentials are transmitted automatically to the Autodiscover URL.
The Autodiscover URLs that will be connected have arrived from the email address configured in the client.
Such as, when our security researcher tested the Autodiscover feature using the email ‘[email protected],’ he found that the mail client tried to authenticate to the following Autodiscover URLs:
- https://Autodiscover.example.com/Autodiscover/Autodiscover.xml
- http://Autodiscover.example.com/Autodiscover/Autodiscover.xml
- https://example.com/Autodiscover/Autodiscover.xml
- http://example.com/Autodiscover/Autodiscover.xml
The mail client would try to each URL until it was successfully authenticated to the Microsoft Exchange server and configuration information was sent back to the client.
Hijacking Credentials to External Domains
If the client could not authenticate to the above URLs, security researchers found that some of the mail clients, including Microsoft Outlook, would perform a “back-off” procedure. This procedure tries to generate additional URLs to authenticate to, like the autodiscover .tld domain, where the TLD is derived from the user’s email address. In this case, the URL generated is http://Autodiscover.com/Autodiscover/Autodiscover.xml.
This incorrect implementation of the Autodiscover protocol is causing mail clients to authenticate to untrusted domains, such as autodiscover.com, which is where the trouble begins. As the email user’s organization does not own this domain, and credentials are automatically sent to the URL, it would allow the domain owner to collect any credentials sent to them.
To test this, Guardicore registered the following domains and set up web servers on each to see how many credentials would be leaked by the Microsoft Exchange Autodiscover feature.
- Autodiscover.com.br – Brazil
- Autodiscover.com.cn – China
- Autodiscover.com.co – Columbia
- Autodiscover.es – Spain
- Autodiscover.fr – France
- Autodiscover.in – India
- Autodiscover.it – Italy
- Autodiscover.sg – Singapore
- Autodiscover.uk – United Kingdom
- Autodiscover.xyz
- Autodiscover.online
After these domains were registered and used, Serper found that email clients, including Microsoft Outlook, sent many account credentials using Basic authentications, making them easily viewable.
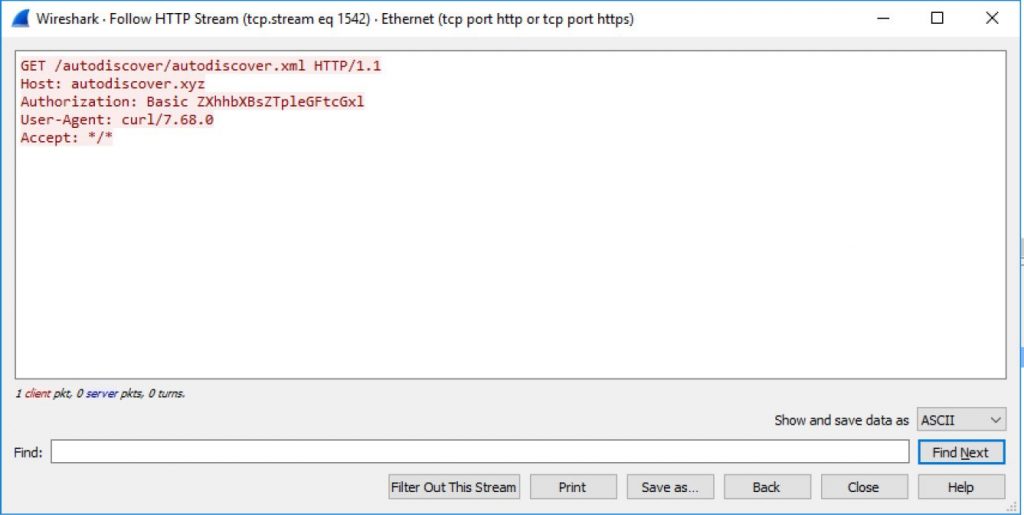
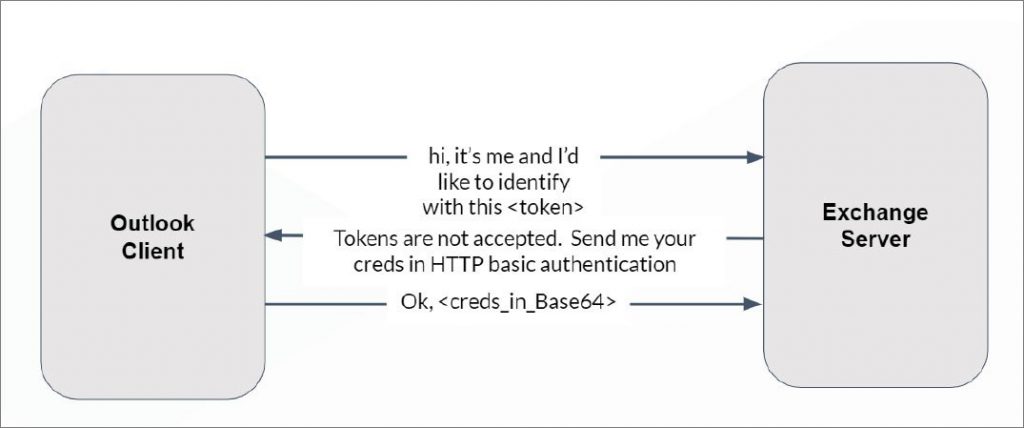
For Microsoft Outlook clients that transmit credentials using NTML and Oauth, the researcher created an attack known as “The ol” switcheroo” that would force to downgrade the request to a Basic authentication request.
This would again permit the investigator to access the cleartext credentials for the users.
While conducting these tests between 20th April and 25th August 2021, Guardicore servers received a:
- 648,976 HTTP requests targeting their Autodiscover domains.
- 372,072 Basic authentication requests.
- 96,671 unique pre-authenticated requests.
Guardicore states the domains that transmitted their credentials include:
- Publicly traded companies in the Chinese market
- Food manufacturers
- Investment banks
- Power plants
- Power delivery
- Real estate
- Shipping and logistics
- Fashion and Jewelry
Alleviating the Microsoft Exchange Autodiscover Leaks
The researcher has provided a few recommendations that a company and developer can use to alleviate these Microsoft Exchange Autodiscover leaks.
For companies using Microsoft Exchange, one should block all Autodiscover.tld domains at your firewall or DNS server so that the devices cannot connect to them. Guardicore has generated a text file including all Autodiscover domains that can be utilized to generate access rules.
Companies are also suggested to disable Basic authentication, as it importantly transmits credentials in cleartext. For software developers, the researcher recommends users prevent their mail clients from failing upwards when constructing Autodiscover URLs so that they never connect to Autodiscover.tld domains.
Why developers, including Microsoft, are falling behind to unauthenticated autodiscover.tld domains remain a secret, as Microsoft’s documentation on the Autodiscover protocol makes no mention of these domains. “Many developers are just using third party libraries that all have the same problem. I’m willing to bet that the vast majority of developers aren’t even aware of it,” the researcher told our experts.



