On 17th March 2021, the security researcher identified a method that was used to hide unwanted data in form of MP3, ZIP file, PNG image, and other data up to 3 MB inside a Twitter image.
After the investigation, the security researcher executes the method and showed how MP3 audio and ZIP file is hidden in between the PNG image the was hosted in Twitter.
However, the art of hiding the data in the images is also named steganography but it is not a novel action, because the images used are hosted on the popular sites Twitter and there is the risk that the image may contain malicious data.
What Happened Exactly?
The researcher shared an example of the attached images and data that images contain in form of the ZIP file or MP3 format hidden in the image.
Whereas the image hosted displays a valid file when previewed before downloading, this may confuse the victims and they are not able to make a difference between the pirated image and the genuine one.
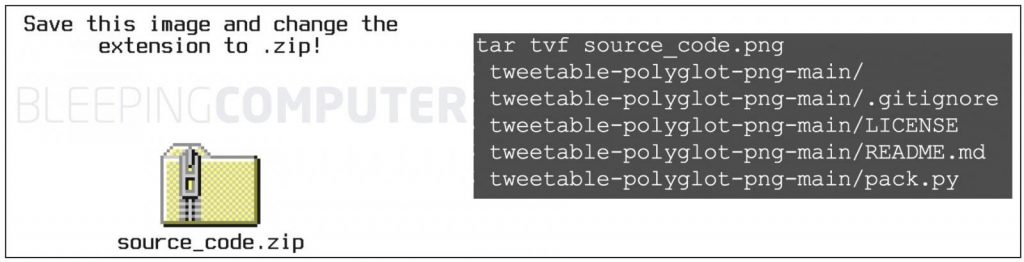
The experts also said that they attached a 6KB ZIP file and that the ZIP file contains Buchana’s source code that executes the unwanted malware into the user’s system. The researcher also shared that the source code that was using while creating this png image or also named as tweetable-polyglot-png files on GitHub.
Another researcher uploaded an image that is capable to sing, for this you have to download the image and rename it to .mp3 then open the file into any media player. Now you were able to listen to a song that was compressed in the image by the creator.
However, Twitter does compress the images every time, but in some cases, it doesn’t. While maintaining the security and privacy of the user Twitter also strip the other non-essential metadata that exists on polyglot file to reduce the attack.
This is the new trick that was identified by the research that DEFLATE the data and overlaps the Twitter strip feature and hides the malicious file within the image.
Effects of this Attack!
The technique named Stenography is also offering multiple attacks by hiding the malicious content using different commands, payloads, and other ordinary files. These attacks are rapidly increasing because Twitter may not be strip all images, just in the case of Buchanan, this will open the doors for the attackers to steal or infect user data.
Whereas, the network administrator is capable to block the Twitter image domain listed as pbs.twimg.com that is responsible for hosting these images on Twitter.
The experts also believed that the PNG image used had a proof-of-concept technique and this may no be similar to the steganography technique. They also added that this technique is not used by the attackers because it is very easy to use and identified.
Attackers also implant small malware into the victim’s system using these techniques and also execute command-and-control server activities.
Summering Up
Users got easily trapped by this attack because Twitter is considered to be safe and it may be used secured host by network monitoring and malware distribution using the image files that bypassing the security logs.
The experts also said that Twitter may not be aware of this bug, But they reported this trick under their bug bounty programs and it is not a security bug, therefore experts didn’t report it further.
Whereas, multiple attackers are misusing the services which also include Imgur that hosted the images and which were later used while calculating the malicious Cobal Strike payload and other problems.



