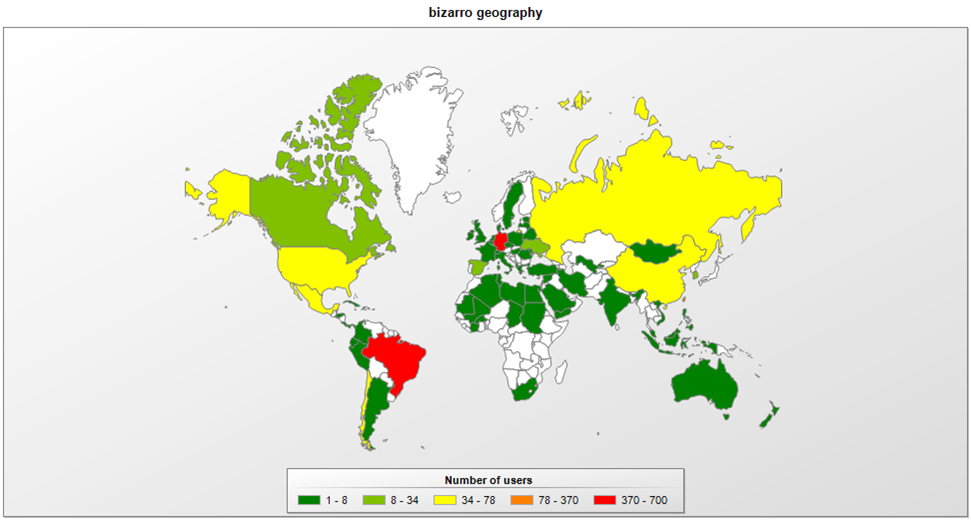
Bizarro i.e. A banking Trojan that arrives from Brazil has crossed the limits and started to target customers of 70 banks in Europe and South America.
While coming on a Windows system, the malware can pressure customers to fill in their banking details and to steal the two-factor authentication code they use for social engineering.
The Extension
However, Bizarro is under regular advancement as its creator broadens the list of supporting banks and they customize it to improve anti-analysis securities.
Figures from various cybersecurity companies show that the new targets of Bizarro are the customers of banks in Europe (Spin, Portugal, Germany, France, Italy) and South America (Chile, Argentina, Brazil).
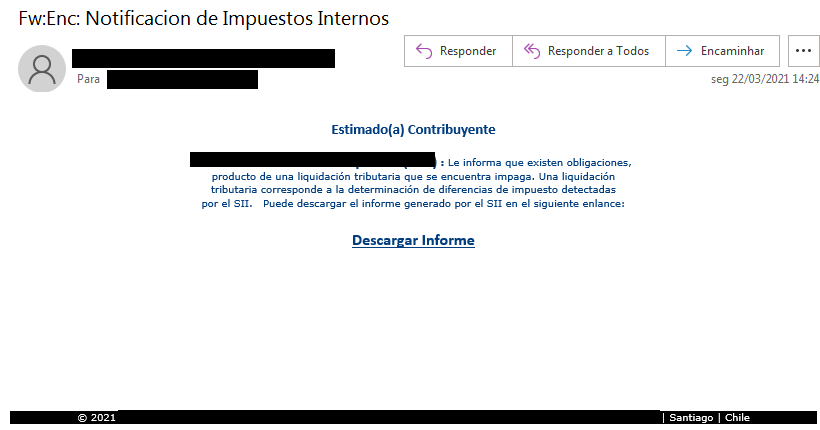
The Trojan transmit phishing emails that are mostly changed as official tax-related mails briefing of important obligations.
Clicking on the downloading link presents in the message redirects Bizarro as an MSI Package. After being clicked, the trojan downloads from the hacked WordPress, Amazon, and Azure servers a ZIP archive with virus elements needed for the attack.
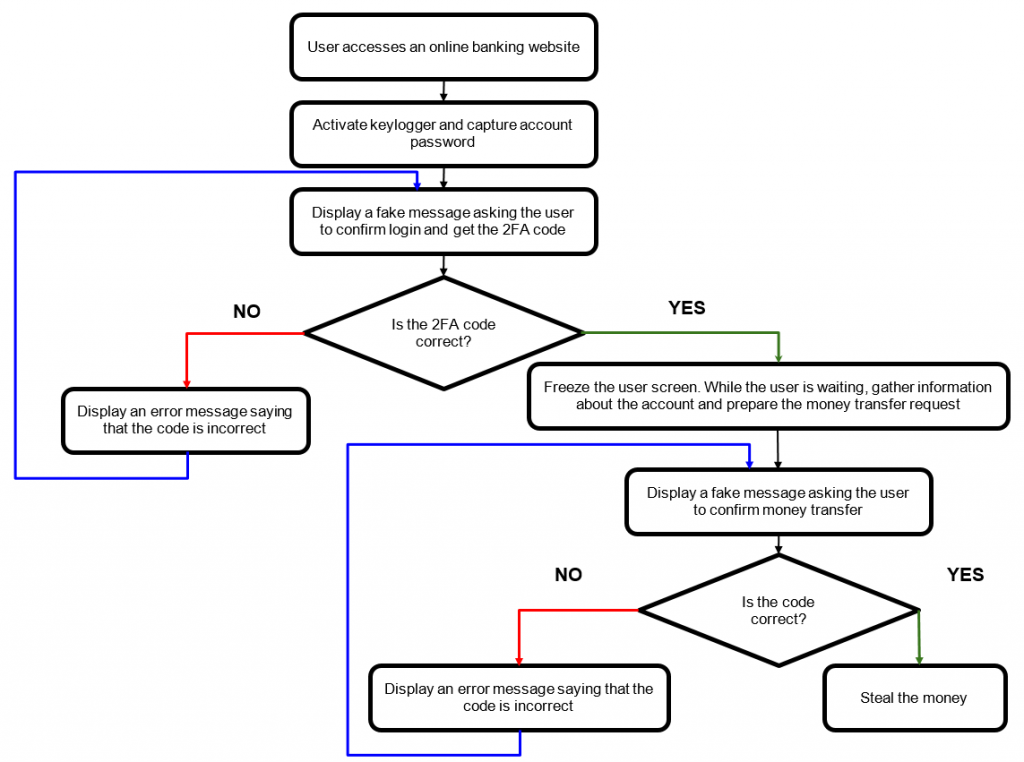
Working of Bizarro Malware
After initiating, Bizarro will abort any ongoing sessions with online banking services by terminating all the browser processes. This pressurizes the user to re-enter the banking details, permitting the Trojan to collect them.
They can also disable the auto-complete function in the browser to collect the login details when the user enters them manually.
The experts also conclude that Bizarro’s main factor is its backdoor feature, which enables over 100 commands, most of them used to display the fake pop-up notification to the customers.
The feature becomes active only after the trojan itemizes all windows to check for a connection to one of the available bank sites.
Following are the commands which Bizarro receives from its command and control server:
- Fetch information about the customers and manage the connection data
- Permits the control of the files on the hard disk
- Permits the control of mouse and keyboards
- Shut down, restart or damage the operating system and reduce the functionality of Windows
- Enable the commands to facilitate social engineering attacks
- Log keystrokes
The Elements of Social Engineering
Bizarro’s operators can mislead users into grant the bank account credentials by notifying them with message boxes or windows asking for the login information or two-factor authentication codes.
By executing several commands for the backdoor element. Bizarro’s operator can mislead the user into providing their crucial information by showing them custom pop-ups or windows.
The pop-ups generally vary from fake notifications requesting the credentials again or asking to fill the confirmation code to fraudulent bugs informing that to complete security-related operations you need to restart your computer. One more social engineering trick in Bizarro’s hat is displaying an image of JPEG format which contains a target bank’s logo and the guidance for the victim.
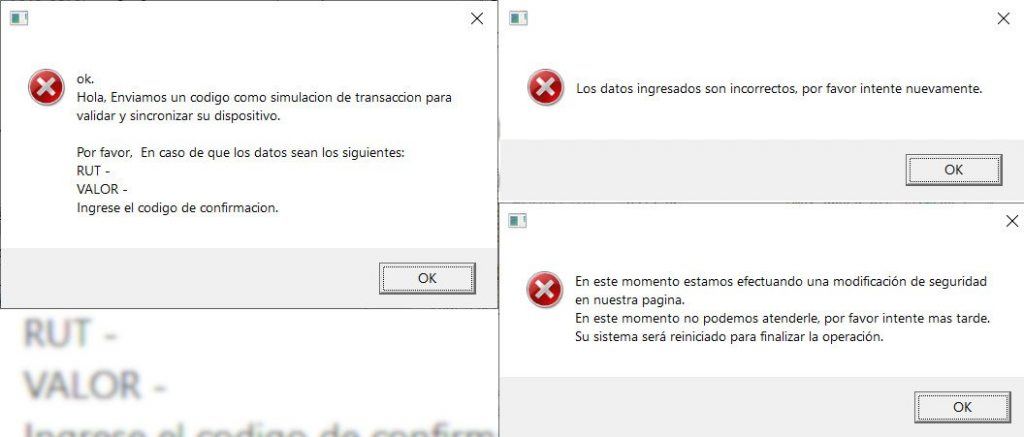
Sometimes the messages may block access to the entire screen and for making it more difficult to start Task Manager it hides the taskbar. Almost all of the messages try to assure the user that their system is negotiated or immediately needs an update, or you need to immediately install the performance components for the web browsers.
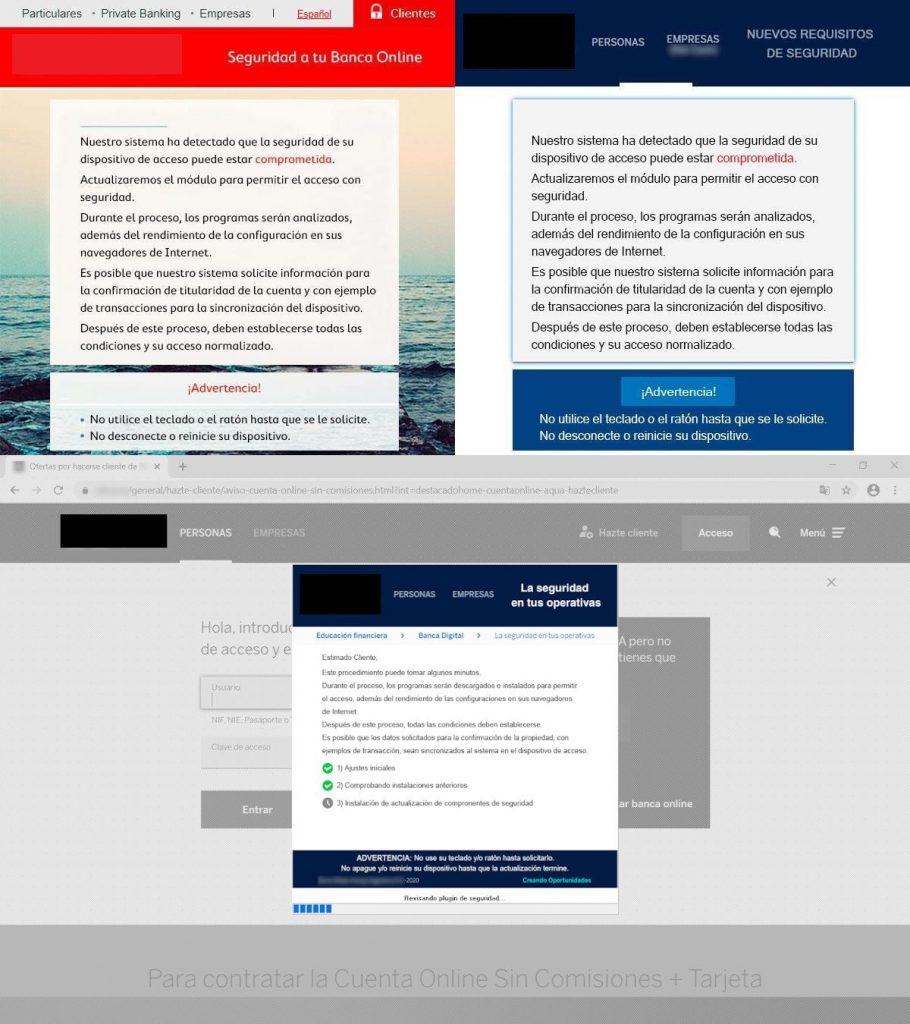
Even the social engineering component broaden to trick the user into installing on their mobile phones a bogus banking app, which permits the capturing of credentials and sensitive codes from mobile devices. From the commands of malware, an attack seen on a negotiated system initiates with the victim running banking sites.
The malware captures the account password and then fake messages are shown to collect the two-factor authentication code by the keylogging feature. By displaying the fake alerts from the banks that block the user’s access to the entire screen cybercriminals get some time to prepare a fraudulent transaction.
Cybersecurity associations say that Bizarro is not only the banking malware that expands to South America to Europe. Some other Trojan has followed the same way as Bizarro. All of them were also developed, created, and transmit in Brazil and have extended outside Latin America.



