All the four security vulnerabilities have been revealed in the Sage X3 enterprise resource planning (ERP) product, during recent proactive testing of the systems, in which two could be attached as part of an attack serial to allow adversaries to run malicious commands and grant access to a vulnerable system.
Sage X3 is now targeted at mid-sized companies – particularly manufacturers and distributors – that are seeking all-in-one ERP functionality. The system handles sales, inventory, purchasing, customer relationship management, and production in one combined ERP software solution.
These flaws were uncovered by investigators from Rapid7, who disclose Sage Group of their searches on the 3rd of February. The dealer has since rolled out fixes in current releases for Sage X3 Version 9 (Syracuse 9.22.7.2), Sage X3 HR & Payroll release Version 9 (Syracuse 9.24.1.3), Sage X3 Version 11 (Syracuse 11.25.2.6), and Sage X3 Version 12 (Syracuse 12.10.2.8) that were shipped in March.
Below is the List of Vulnerabilities
- CVE-2020-7388 (CVSS score: 10.0) – Sage X3 Unauthenticated Remote Command Execution (RCE) as SYSTEM in AdxDSrv.exe component
- CVE-2020-7389 (CVSS score” 5.5) – System “CHAINE” Variable Script Command Injection (No fix planned)
- CVE-2020-7387 (CVSS score: 5.3) – Sage X3 Installation Pathname Disclosure
- CVE-2020-7390 (CVSS score: 4.6) – Stored XSS Vulnerability on ‘Edit’ Page of User Profile
“On mixing CVE-2020-7387 and CVE-2020-7388, a threat actor can first learn the installation path of the affected software, the go through the information to give commands to host system to be run in SYSTEM context,” the investigator said. “This can permit a threat actor to execute arbitrary operating system commands to create Administrator level users, install malicious software, and otherwise grant complete access of the system for any purpose.”
Critical Authentication – Avoid Security Vulnerability
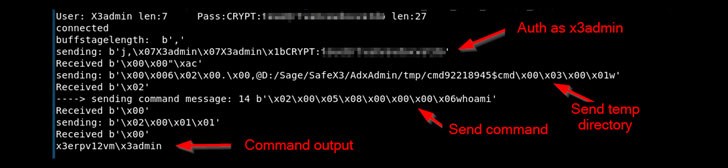
One of the most serious flaws is CVE-2020-7388, which takes advantage of an administrative service that’s accessible over the internet to expertise malicious requests to execute arbitrary commands on the serves as the “NT AUTHORITY/SYSTEM” user. The service in question is used for remote management of the Sage ERP solution through the Sage X3 Console.
Moreover, the ‘Edit’ page correlated with user profiles in the Sage X3 Syracuse web server element is vulnerable to a preserved XSS attack (CVE-2020-7390), allowing the execution of arbitrary JavaScript code during the ‘mouseOver’ function in the ‘First name’, ‘Last name’, and ‘Email’ fields.
“In case it is successful, however, this vulnerability could permit a regular user of Sage X3 to run privileged events as currently logged-in administrator or capture administrator session cookies for later impersonation as currently-logged-in administrator” The investigator mentioned.
Successful accomplishment of CVE-2020-7387, on the other side, outcomes in the disclosure of Sage X3 installations paths to an unauthorized user, while CVE-2020-7389 concerns a missing authentication in Syracuse development environments that could be used to gain code run using command insertion.
“Usually talking, Sage X3 installation should not be revealed directly to the internet, and should instead be making available via a protected VPN connection where needed,” the investigator noted in the disclosure. “Following this operation advice efficiently prevents all four vulnerabilities, though customers are still supported to update according to their usual patch cycle schedules.”
Sage has acted quickly to deal with these four vulnerabilities. The process of responsible disclosure has not only worked, but it has also provided Sage time to develop and set up patches. It has also permitted Sage to spend time talking to customers and partners to ensure a high patch compliance level. So, it does also bring some of the concerns into focus.
The second concern here is that companies should not get sidetracked by the comment about external access. Achieving so means they are not paying enough attention to the harm that attacks inside the network cause. It is a wake call that all organizations need to think about it.



