T-Mobile has assured that the threat actors hacked their servers in an active cyber attack but still researches whether customer information was hijacked. In previous days, news broke that a threat actor was trading the purported personal information for 100 million T-Mobile customers after they hijacked database servers operated by the mobile network.
The threat actor told our experts that the databases hijacked during the attack contain the information for approximately 100 million T-Mobile customers, including IMSI numbers, IMEI numbers, phone numbers, customer names, security PINs, Social security numbers, driver’s license numbers, and their date of birth.
This data was hijacked approximately two weeks ago and contains customer information going back as far as 2004. “All their IMEI history database going back to 2004 was hijacked,” the hacker told our experts. When we get in touch with T-Mobile yesterday, they said that they were aware of the claims and were ongoing investigating whether they were hijacked.
How T-Mobile Assures Servers Were Hijacked?
Through an email, T-Mobile ensures that some of its servers were hijacked in the reported attack and is constantly investigating if customer data was accessed.
“We have been working around the clock to research the claims being made that T-Mobile information may have been illegally accessed. We take the protection of our customers very seriously and we are conducting a considerable analysis alongside digital forensic experts to understand the validity of these claims, and we are coordinating with law enforcement.
We have determined that unauthorized access to some T-Mobile data occurred, however, we have not yet determined that there is any personal customer data involved. We are confident that the entry point used to gain access has been closed, and we are continuing our deep technical review of the situation across our systems to identify the nature of any data that was illegally accessed. This investigation will take some time but we are working with the highest degree of urgency. Until we have completed this assessment we cannot confirm the reported number of records affected or the validity of statements made by others.
We understand that customers will have questions and concerns, and resolving those is critically important to us. Once we have a more complete and verified understanding of what occurred, we will proactively communicate with our customers and other stakeholders.” – T-Mobile.
While T-Mobile is continuing its searches, screenshots of the hijacked database and servers accessed by the threat actor show that the threat actor downloaded the customer information during the Cyberattack. A Screenshot shared with our experts shows that the threat actors connecting to an Oracle database server over SSH on the company’s internal information center network.
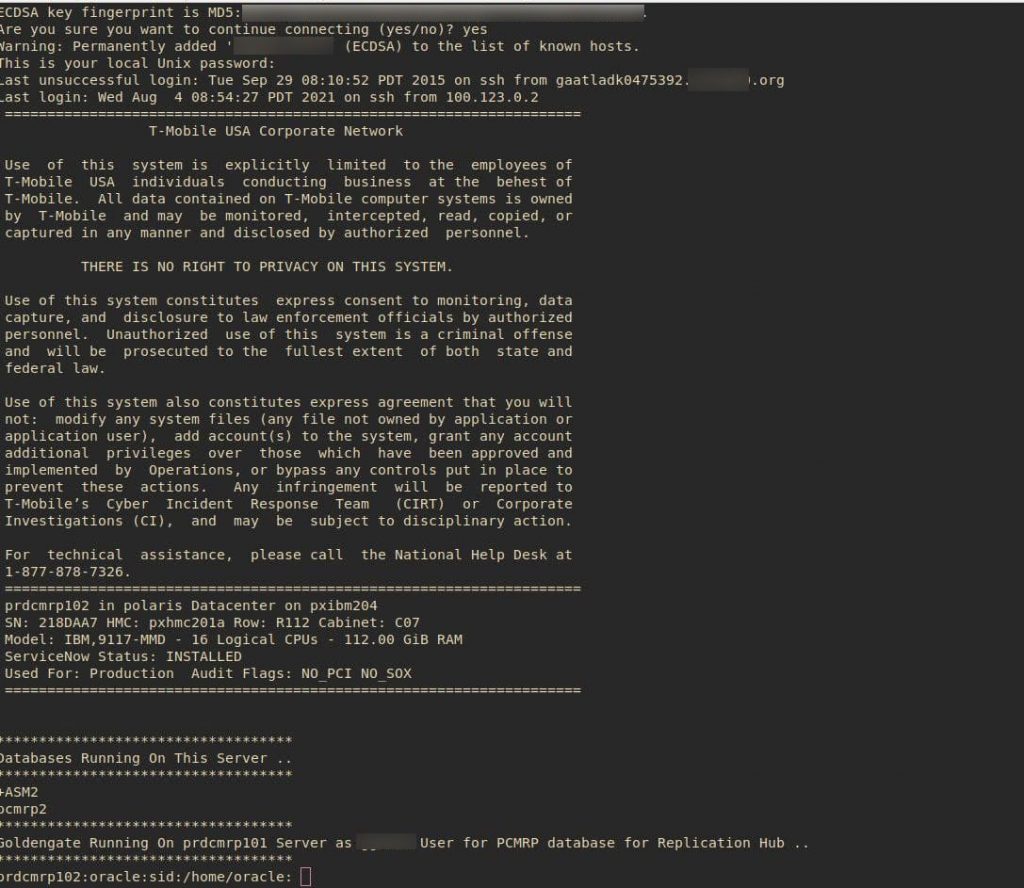
If it is revealed that the customer’s information was hijacked during the attack, which is expected, then this will significantly hijack as the threat actor will have enough data to try SIM swapping attacks.
Utilizing such attacks the threat actor can transmit a phone number to their own devices to receive credentials reset and multi-factor authentication requests that could permit them to hijack other accounts belonging to a customer.
This would be the sixth data breach suffered by T-Mobile in the past four years:
- In 2018, millions of T-Mobile customers’ information was accessed by hackers.
- In 2019, T-Mobile prepaid customers’ information was revealed.
- In March 2020, hackers gained access to T-Mobile employee’s email accounts.
- In December 2020, hackers gained access to expose the customer’s proprietary network information (CPNI).
- In February 2021, threat actors gained access to an internal T-Mobile application to target up to 400 customers in SIM swap attack attempts.
What will the T-Mobile Customer do?
As the threat actor told our experts that they have offers from other threat actors to purchase the information, T-Mobile customers should be operated under the acceptance that their information was revealed.
All T-Mobile customers should be on the lookout for suspicious emails or SMS texts pretending to be from T-Mobile.
If any received, do not tap on any links embedded in the message as threat actors could use them to grow up the passwords from unsuspecting T-Mobile customers.



