Academic investigators have discovered a way to make fake transactions using Apple Pay from a locked iPhone with a Visa card in the digital wallet with express mode enabled. The method is similar to a digital version of pickpocketing. It works over the air even in case the iPhone is in a flaw or someone’s pocket and there are no transactions limits.
What is Ticket-gate Payment Trick?
Considering attacks on unknown transactions, investigators at the University of Birmingham and the University of Surrey in the U.K. discover the iPhone devices confirm transactions under some conditions.
For a transaction to go through, iPhone users need to authenticate it by unlocking the phone using the Face ID, Touch ID, or a passcode. In some of the scenarios, though, such as paying for public transportation, unlocking the devices makes the payment process cumbersome for the users.
Apple Pay solved the problem with Express Transit, a feature that permits the payment to go through without unlocking the device.
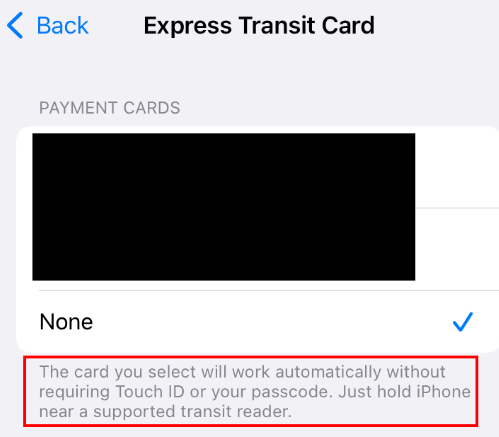
Express Transit works for some services, such as ticket gates, with card readers that send a non-standard arrangement by bytes the Apple Pay lock screen. In sequence with a Visa Card, “this feature can be leveraged to avoid the Apple Pay lock screen, and unjustifiably pay from a locked iPhone, using a Visa Card, to any EMV reader, for any amount, without user authorization.”
The investigators were able to imitate a ticket-barrier payment by utilizing a Proxmark device acting as a card reader communicating with the target iPhone and an Android phone with an NFC chip that transmitted with a payment terminal.
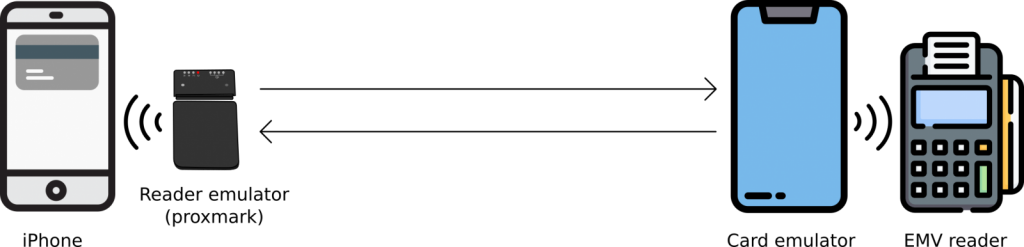
As shown in the image above, the method is an active man-in-the-middle replay and relay the attack where the Proxmark replays the “magic bytes” to the iPhone to trick it into trusting that it’s ticket-gate transactions so user authentication to authorize the transaction so the users authentication to authorize the transaction is not required.
The attack is much more complicated than this. The investigator explained that some of the flags need to be set by changing some bits to allow offline data authentication for online payments, used in readers that many have intermittent 01 connectivity.
Promoting the Limit
Digging deeper into the issue, the researcher discovered that they could modify the Card Transaction Qualifiers (CTQ) responsible for setting contactless transactions limits.
This modification is to trick the card reader that the authentication step on the mobile device has been completed successfully. During the experiment, the researchers were able to make a GBP 1,000 transaction from a locked iPhone. They tested the attack successfully on iPhone 7 and iPhone 12.
The Vulnerability is not fixed
The tests were successful only with iPhone and Visa cards. With Mastercard, a check is performed to make sure that a locked iPhone accepts transactions only from card readers with a transit merchant code.
Trying the method with Samsung Pay, the researchers found that transactions are always possible with locked Samsung devices. However, the value is always zero and transport providers charge for tickets based on data associated with these transactions.
The findings of this research have been sent to both Apple and Visa in October 2020 and May 2021, respectively, but neither fixed the problem. Instead, the two companies passed the burden of a fix to one another, so the vulnerability is still present and can be exploited with off-the-shelf hardware and software.
The details of the research are available in a paper titled “Practical EMV Relay Protection,” to be presented at the 2022 IEEE Symposium on Security and Privacy.



