Microsoft Windows 10 Zero-Day Exploit 2020 is now disclosed publicly. Google project zero team made these details public as Microsoft is failed to released the patch in 90 days. In June, Microsoft released a vulnerability fix for Windows OS. Every month, Microsoft released various updates to fix the vulnerabilities present in Windows OS. The latest fix has already released and it addresses the total 111 security vulnerabilities in which more than 16 are very critical and having no zero-days.
Some people may confuse with the term “Zero-Days”. What does it mean? How it is related to Microsoft itself and what is the impact of Zero-days on vulnerabilities of Microsoft?
To know about these things read the upcoming section!
What is Zero Day?

It is vulnerability or you can say it is a flaw in the wild that illustrates the presence of a vulnerability in the software or hardware which can be created complicated problems before anyone realizes something is wrong. In a Zero-Day attack, the hacker or the actor releases the malware before the developer is created a patch to fix these vulnerabilities.
Now read the upcoming section to know what is happens with Microsoft while they releasing the patch to fix this vulnerability.
What happens with Windows 10 Zero-Day Exploit 2020?
Microsoft developers constructed the update in which unwanted vulnerabilities were discovered. The hackers spot these vulnerabilities before the developer creates any patch or update to fix the issue. The hacker starts writing and implementing the code “splwow64.exe” while the vulnerability is still available.
Once the exploit is released by the hacker, it gets started infecting the system the hackers are capable to read, write, delete or change the data and the developer recognizes it after some time and creates the patch or solution to fix this. This whole process takes months, sometimes developers took years while analyzing the vulnerability.
Prevention Taken By Microsoft
According to the experts Microsoft received a confirmation report on 24th September. Now the company is planning to release a patch in November 2020, but due to some circumstances that occur during the testing stage, the company pushed the release date to 12th January 2021.
The experts say that “Restriction access to the services it the best method to prevent the attacks, before the patch is created. But this will impacts on the print functionality and maybe not suitable for all the users”
Google security researcher Maddie Stone discovered that patch (CVE- 2020- 0986) in June and Microsoft also released an update for that but it’s couldn’t work. The issue is still exploitable using different methods according to security analysis.
Stone also said that the hackers are still capable to implement the code in CVE-2020-0986 update to increase the permissions to the kernel level. Microsoft patch was improper because it can only change the pointers to offsets, there the function of parameters are still compromised using different methods as you see on Stone tweet attached below.
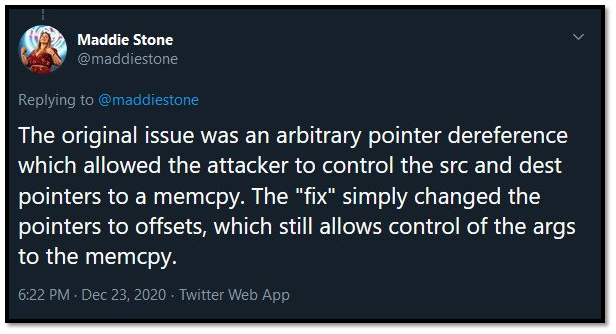
Maddie also explains how to trigger the vulnerability that Microsoft fixed and now identified as CVE-2020-17008;
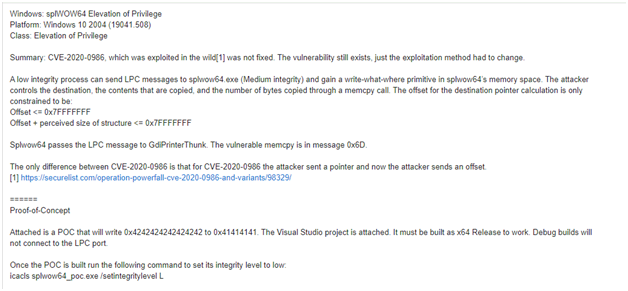
According to stone, Google Project Zero has a disclosure policy of 90 Days, along with an extension of 14 Days if needed to fix the patch. But Microsoft released the fix on 6th Jan 2021, which disobeys both the deadlines Google mentioned.