2020 is ended and it taught us many things; Cyber Attacks are increasing day by day and they are getting worse in the future. Therefore it is very important to every computer user, whether you are working for an organization or working for your purposes, you need to understand about one of the biggest Cyber Attack ie… The Ransomware Attack. What is it and how to prevent, and steps taken to protect your data from Ransomware and many other things.
In this Epidemic of Covid-19, multiple organizations opt for Work From Home to control the spread of Corona-virus, but there are many disadvantages to it. The company shares the data with their employees through the network, all the work like a client meeting, important data, company details are transferred over the network this may increase the risk of a Ransomware attack.
Therefore, after lots of research and analysis, we wrote this article and put the crucial information related to Ransomware attacks about the working of it and what is the cure, why this is the most sophisticated attack and many more things, read them wisely.
Let’s start it from the beginning “What is Ransomware ?”
What is Ransomware Attack?

Ransomware is the type of malware that attacks the victim’s data. The attacker tries to encrypt the victim’s data and then they demand some ransom or money for the key to decrypt the files.
The first ransomware attack was reported in 1989 conducted by Dr. Joseph Popp a biologist from Harvard University, they used to preserve the virus on a floppy disk and then he distributed that infected disk to the victim’s by post, as the victim’s access the floppy disk the virus activated and encrypted all the filenames on the victim’s system and then it demands $189 as a ransom, this entire attack is named as the AIDS trojan.

There are two types of ransomware attacks: Commodity attacks and Targeted Group attacks.
The commodity attacks aim to infect computers by sheer volume and also include the services for criminals whereas the targeted groups are focused on the particular vulnerability of organizations.
You are immediately notified if you are the victim of a ransomware attack because it encrypts your files and cut off access to your infected device. Then after some time, the criminals behind this attack will contact you with their demands and they also promised you to unlock and decrypt your device after you pay some ransom or money to them.
Now moving towards the next section to know the working of a ransomware attack.
Working of Ransomware Attacks
It is a 5 step process starting from Sending Virus and ending by exchanging Money. The attacker or the criminal sent the Infected Files to the user as the users were accessing the file then the attack gets notified about it and then the files start its work by encrypting the user data and then the criminal demand some money in exchange for decryption keys.
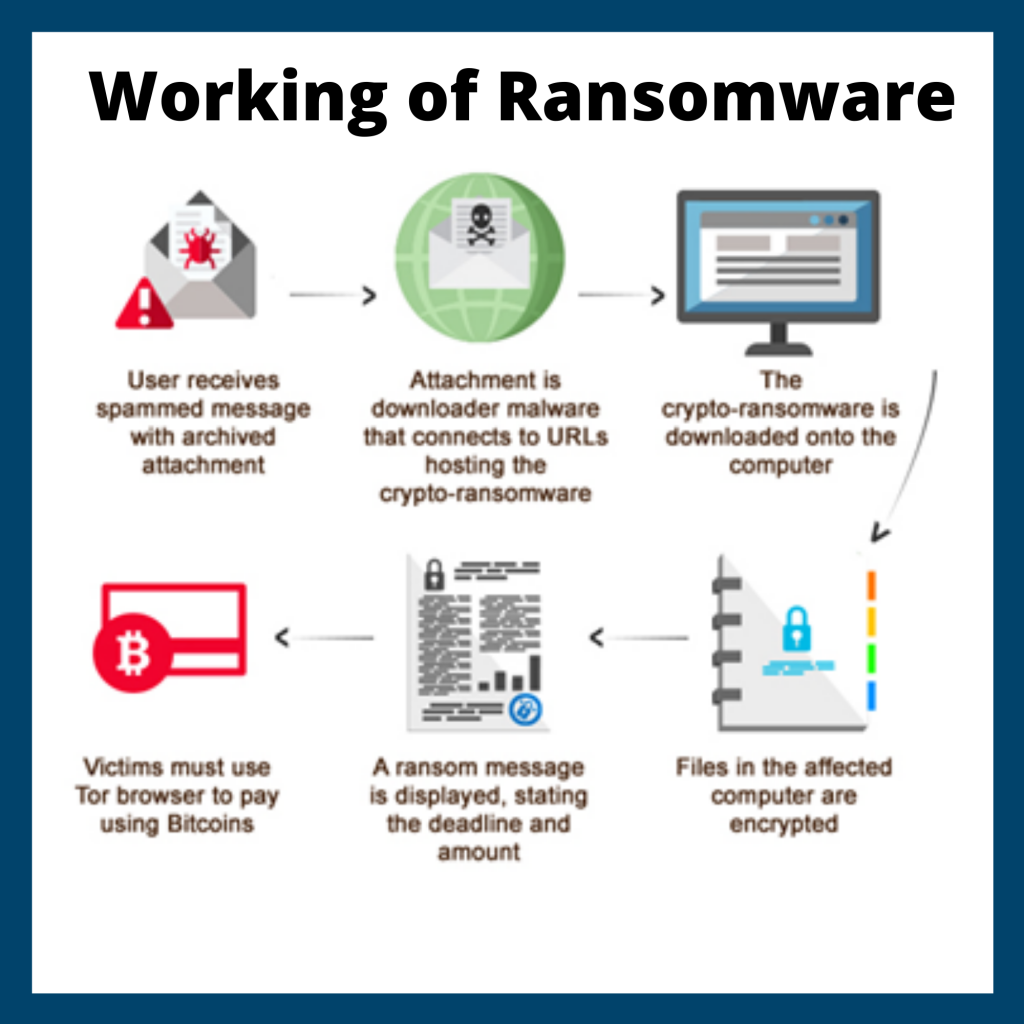
Unlike other malware, ransomware also downloads a malicious file or you have to click on a link, some ransomware attacks work to obey the traditional method. A ransomware attack is a multi-staged attack, depends according to the targeted network. The main motive of the ransomware attack is to encrypt the data as much as possible and demand ransom in the form of bitcoin.
Here in the upcoming section read about the different forms of ransomware work;
Forms of Ransomware Attacks
Social Engineering: The simplest form of a ransomware attack. The attacker used social engineering tricks and make sure that you can download their ransomware virus from the URL.
Malvertising: Another form of a ransomware attack in which the attacker embedded the malware into fake online ads known as Malvertising. Once you click the advertisement you’ll hack.
Exploit Kits: Multiple hackers create an Exploit code that is designed to execute using the vulnerability present in the application, networks, or in any devices. This form of attack will infect network-connected devices.
Phishing: The attacker will send you an email that contains a URL or an attachment link. Once you download or open that file or link, you’ll start the ransomware.
Once your device is under a ransomware attack, then any attempts to view or open your encrypted files will not use. The system always shows an error that your files are invalid or corrupted and cannot be load. Now moving towards the next section on types of Ransomware attacks.
Types of Ransomware Attacks
There are multiple types of ransomware attacks available but we are here going to discuss the common ransomware attacks ramped up over a few years.
- Locky: The most common type of ransomware attack. It spread through the spam email message that looks like the invoice. Once executed, it asks the user to enable macros to read it, and then it will start encrypting into the user system.
- CryLocker: This is the personalized attack that uses personal data of the user such as the user’s name, birthday, locations, system details, social media details, and many more to make and locks the user system.
- Cerber: The deadly ransomware virus that compatible with 12 different languages. It creates a ransomware-as-a-service platform and makes a huge profit. It is a new threat that developed last year.
- Cryptolocker: Encrypt user files with the help of the extension, first reported in 2013. The hacker demands the ransom and threatened o delete the confidential data.
- Jigsaw: Serious type of ransomware that encrypts data files and then deletes them until or unless the ransom is paid. It works for a period of 72-hours, once these hours are completed it will delete the entire files from your system.
- WannaCry: The most widely used ransomware attack the infected near about 125000 organization established in over 150 countries.
Apart from this, Petya, NotPetya, GoldenEye, CryptoWall, Crysis, TeslaCrypt, TorrentLocker, Zcryptor, etc., are also some other types of ransomware attacks.
Data is the most important thing for every user and ransomware is your enemy so read the upcoming section to know about the tips to prevent a ransomware attack.
Tips to Prevent Ransomware Attacks
How to prevent ransomware attacks or recommendations to prevent ransomware attacks starting from unverified links to spam emails. Check them out one by one.
- Never Connect Doubtful Links: Don’t click on spam emails connections, always review the emails before downloading any data from the attached link. Once the ransomware is inserted into your computer, it will start encrypting the files and then demand ransom to recover your data.
- Employ Anti-Virus and Email Filtering Software: Constantly review the updates of antivirus correspondingly confirm that you used email filtering to safeguard from ransomware attacks.
- Don’t Unlock Untrusted Email Attachment: If you receive an attachment and you are not sure about the sender then do not open it without confirming with the person or scan the attachment with an antivirus. Never open attachments that ask you to macros to view them. The attachment looks genuine but they contain malware that controls your system.
- Download from Trusted Sites: Always download everything from trusted sites. Read the license agreement and demonstrate that site uses HTTPS instead of HTTP. Always open verified sites for example Android users should download the data from Play Store and iPhone users can use iTunes.
- Never Share Your Confidential Data: Avoid sharing your private information to anyone over call, text, email that comes from an untrusted source. Attackers use your information in a phishing email to target you. Many attackers may steal your data information and infect your system with the help of your information.
- Backup your Data: Continuously back up your crucial data to an external hard drive. The most necessary thing to prevent ransomware attacks is always to keep a backup of your data on local or cloud storage accordingly. Once the data is backed then remove the drive from the system.
- Employ Strong Passwords: Do not use a weak password like 12345678, always use a strong or encrypted password like 185@abc to control unauthorized access.
- Inspect the Attached Devices: Never use any removal device if you are not aware of them. Many attackers infect the removal devices and left them in public places.
- Encourage User Awareness: Consistently aware of your employees about how to spot this threat. Guide them about the precluding methods and always advise them to take a backup of their data.
- Maintain System Updates: Immediately install the update delivered by your OS to patch the vulnerability present. Always update your installed applications to bypass the random invasion.
Now in the upcoming know how to respond when you face any ransomware attack.
How to Respond to Ransomware Attacks?
If you are a victim of a ransomware attack, then follow these steps described below to manage the effects of an active ransomware attack.
Isolation: The first and most important step is to disconnect the infected device from the network-connected this will reduce the spreading of ransomware to other systems connected through the same network.
Never Pay Ransom: Do not pay any type of money as ransom demanded by cybercriminals because paying ransom will not guarantee of return your data. Paying the ransom is also encourage the attacks.
Read the upcoming section about how to remove ransomware from your system.
Steps to Remove Ransomware from Your PC
- Disconnect Your Computer from the Internet: The first step to stopping ransomware attacks disconnect the internet connectivity to stop the spreading of the ransomware to other devices.
- Run Scan: Use internet security software to scan your computer. This scan will identify the threats present and remove the detected files.
- Use Decryption Tool: Use the ransomware decryptor tool to decrypt your data so that you can access it again if needed.
- Restore Backup Files: If you have taken the backup of your data externally or on cloud storage then restore a clean backup of your files. This will help you to recover your data.
Summering Up
Ransomware removal guide contains lots of steps, most of them need to just update your computer habits or perform the task in manner. The tips described in this article will protect you from ransomware attacks or almost all the other malware attacks. Always update your system software to avoid unauthorized access. Stay safe and think before the click.



