A new variant of NAT attack was founded that is used to compromise and expose the devices connected over the network. This new attack occupies CVE-2020-16043 and CVE-2021-23961 that were previously used to bypass the routers and firewalls and expose unmanaged devices connected over the same network.
According to cyber expert Samy Kamkar, these attacks are used JavaScript-based technique that relays on the user and forces them to visit the malicious website and them the hackers establish a remote connection by TCP/UDP services on victim’s devices, even those who use firewall and NAT.
On November 11, partial mitigation was founded on thwart attack that used ti compromise Chrome 87, Firefox 84 and Safari web browser by preventing the connection on the port 5061 and 5060, the researcher also revealed that this attack was done by NAT Slipstreaming 2.0 and target unmanaged devices and allow the hackers to expose the devices connected directly or indirectly to the network.
These vulnerable devices that easily exposed and became the victims of this attack include organizations’ printers, controllers, IP cameras, and other devices that could easily be exploitable as the NAT firewall is executed once they are connected to the network.
Multiple researchers also said that this update NAT slipstreaming attack may damage the devices and result in the nuisances to caused a sophisticated ransomware attack.
Whereas all the IT companies that include Google, Microsoft, Apple, Mozilla, Safari, Edge, Firefox, and other web browsers released an update patch to address this attack.
Working of NAT Slipstreaming
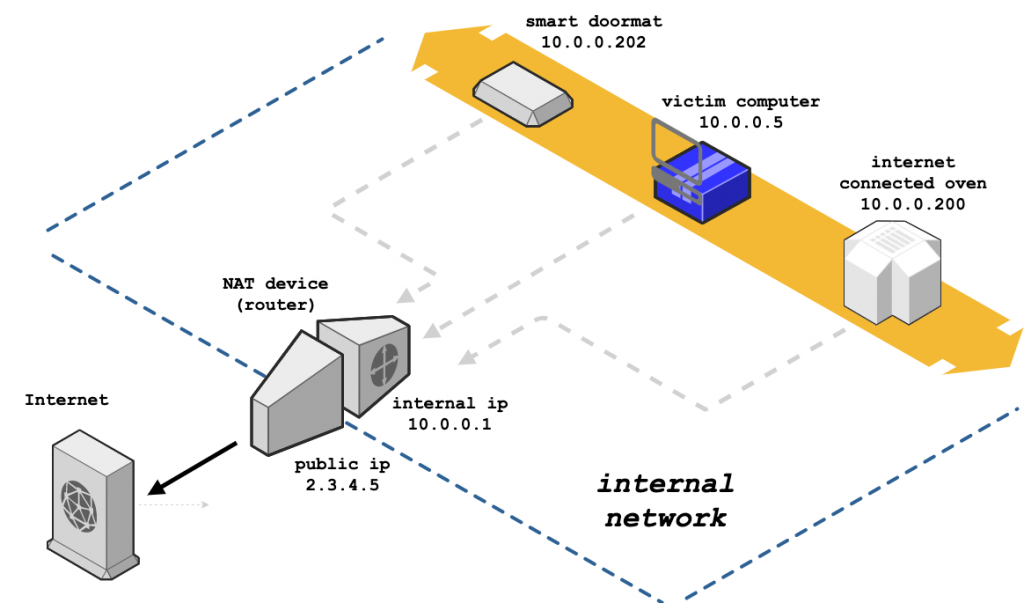
This NAT slipstreaming simply authorize the hacker to overlaps the NAT/ Firewall and give remote access using TCP/UPD services that are bound in the victim’s system. It is work on malicious JavaScript code that was running on the victim’s device, as the browser extracts the IP address and takes the benefit of TCP/IP packet segment to establish update TCP/UDP beacons and simultaneously steal a Session Initiation Protocol that contains the IP address with HTTP POST request through TCP port 5060.
The researcher explains that this is obtained carefully by setting the MSS value that controlled TCP connection from the victim’s browsers, therefore the TCP segment in the middle of HTTP will give the whole control to the attacker.
Conclusion
NAT Slipstreaming 2.0 is similar to another attack that used the same method but overlay the H.323 VoIP protocol in place of SIP while sending multiple requests to the attackers and server. This allows the hacker to iterate through the IP addresses and ports and open each of them on the internet.
It is very important to learn that security was not the primary principle while creating the NATs, apart from this these are mainly by-product that potentially exhausts IPv4 addresses. The legacy requirement that includes ALGs is the most dominant theme while creating the NATs today. The primary reason for overlapping attacks is used to be founded again and again.



