A new ransomware group called Memento takes the unusual approach of locking files inside credential-protected archives after their encryption method kept being detected by the security software. Last month, the group became active when they began exploiting a VMware vCenter Server web client bug for the first access to victims’ networks. The vCenter vulnerability is tracked as ‘CVE-2021-21971’ and is an unauthenticated, remote code execution flaw with the 9.8 critical (severity) rating.
This bug permits anyone with remote access to TCP/IP port 443 on an exposed vCenter server to run the commands on the underlying OS with admin rights. A patch for this bug came out in February, but as indicated by Memento’s operation, various organizations have not patched their installs.
This vulnerability has been under exploitation by Memento since April, while in May, a different actor was spotted exploiting it to install XMR miners via PowerShell commands.
Exploiting vCenter to deploy ransomware
Memento launched their ransomware operation last month when they began vCenter to extract administrative credentials from the target server, establish persistence through scheduled tasks, and then use RDP over SSH to spread laterally within the network.
After the reconnaissance stage, the actors used WinRAR to create an archive of the stolen files and exfiltrate it.
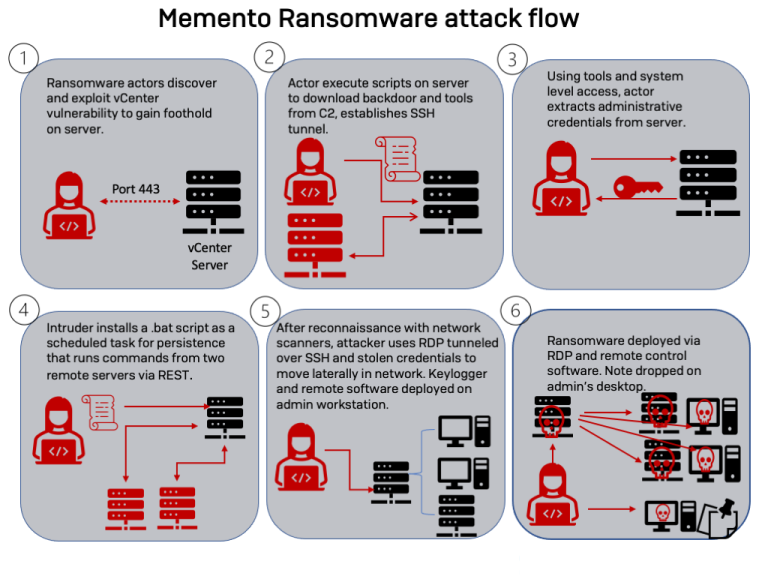
Finally, they used Jetico’s BCWipe data wiping utility to delete any traces left behind and then used a Python-based ransomware strain for the AES encryption. However, Memento’s original attempts at encrypted files as the systems had anti-ransomware protection, causing the encryption step to be detected and stopped before any damage was done.
What is a Workaround?
To overcome the detection of commodity ransomware by the security software, Memento came up with an interesting tactic – skip encryption altogether and move files into password-protected archives.
To do this, the group now moves files into WinRAR archives, sets a strong password for access protection, encrypts that key, and finally deletes the original files. “Instead of encrypting files, the “crypt” code now put the files in unencrypted form into archive files, using the copy of WinRAR, saving each file in its own archive with a .vaultz file extension,” explains Sophos analyst Sean Gallagher.
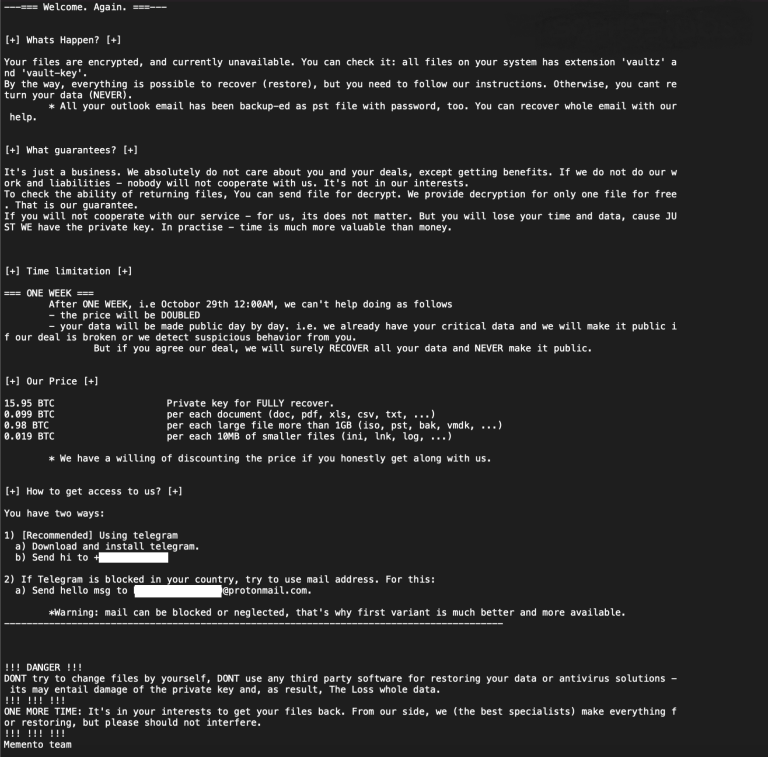
In the cases that Sophos investigated, these extortion attempts haven’t led to a ransom payment, as victims used their backups to restore the files. However, Memento is a new group that has just found an atypical approach that works, so they’ll likely try it against other organizations.
As such, if you’re using VMware vCenter Server and/or Cloud Foundation, make sure to update your tools to the latest available version to resolve known vulnerabilities.