ATT&CK for Mobile is an adversary guide against the security threats that was started with the aim of highlighting the threats and exploiting different security architectures in mobile devices. This service was started in 2017 and now they are rapidly growing with new ATT&CK updates, as they are releasing the strong content with the help of contributions that were received from many peoples among different communities.
In this post, we are formally introduced to ATT&CK for Mobile service and their future plans. We also highlight how ATT&CK for Mobile is used to address the malicious things spotted in the Android application and check all the special app accesses.
Android Authorities and App Path
Multiple devices run several applications that contain various vulnerabilities and malicious application behaviors. These can exploit several vulnerabilities and given these risk that includes sandboxes applications and separating them from another device. The application used must have take permission before executing any crucial operations.
ATT&CK for Mobile shows how Android applications permissions are manipulated by hackers, and also highlight the methods of defending them. Apart from them the matrix also gives the details related to abuse and displays the defense about what application calls the special app accesses, which further requested and managed differently than the regular android permissions.
Whereas special application access requires a more complicated defense approached.
Recognize about Android Permissions, Abuses, and Mitigations
The android device needs application permissions before accessing confidential information or executing the operations. All the applications have to declare their permission on their AndroidManifest.xlm file that used user permissions entry.
Adversaries are divided according to malicious applications that request the user and make the permissions, or they may execute the vulnerabilities present while holding permission.
Multiple organizations are using various solutions that are used to access the mobile application and analyze their behaviors that also deals with a complete scan of the application used while declaring the file of higher risk permissions like audio recording. If any vulnerabilities are found during the scan then the enterprises could block the application.
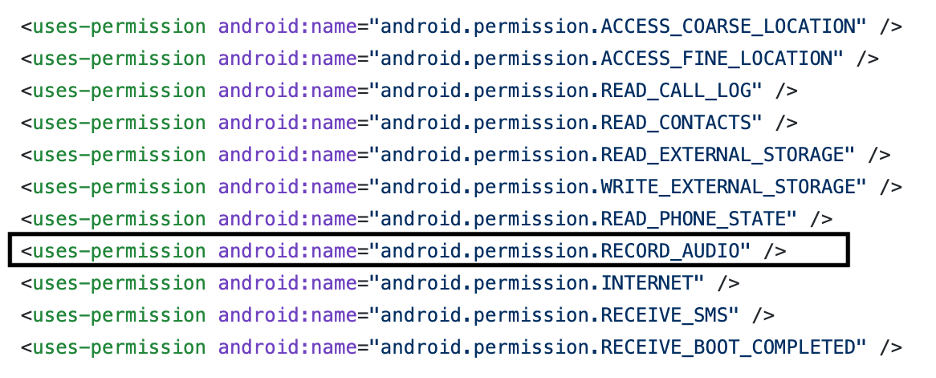
Whereas there are multiple benefits of using the Enterprise Mobility Management (EMM) system that is also known as Unified Endpoint Management (UEM) or Mobile Device Management (MDM) that is able to push the runtime permission on to the device to prevent an application from accessing the specific permissions.
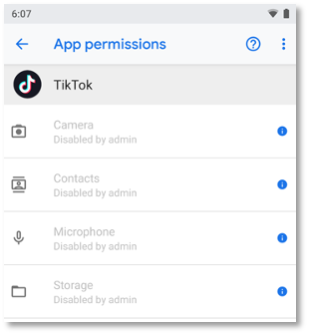
Accomplishing Special App Accesses
ATT&CK for Mobile techniques are now using the updated defense data, to encounter what is an Android device refers to as special app accesses. Each of the special app access application is managed separately and have a unique way to requesting the file and detecting their work. The default framework is not capable to control these types of applications.
According to Android Platform Security Model Paper, these special app accesses permissions can expose more or high risk than other applications.
Therefore ATT&CK for Mobile describes adversary use of special app accesses:
- Accessibility: Capable to assist more users with multiple disabilities in Android devices and applications, that also abused several applications to store confidential information from the device screens or inject malicious files to mimic users’ clicks.
- Read Notifications: Various applications read notifications that contain sensitive information that includes one time passwords and many more transmitted over the SMS.
- Draw Over Other Apps: Some malicious applications display prompts on top of other applications and saved to data such as account credentials and many more.
- Device Administrator: Multiple malicious applications are capable to perform administrative operations such as wiping device data and many more.
- Input Method: Several malicious applications register with the device as a keyboard and steal the user’s keystrokes.
Once the special app accesses are given to the application then they can only be managed by the Android device through settings. The path should be like this;
(Settings → Apps & Notifications → Advanced → Special App Accesses)
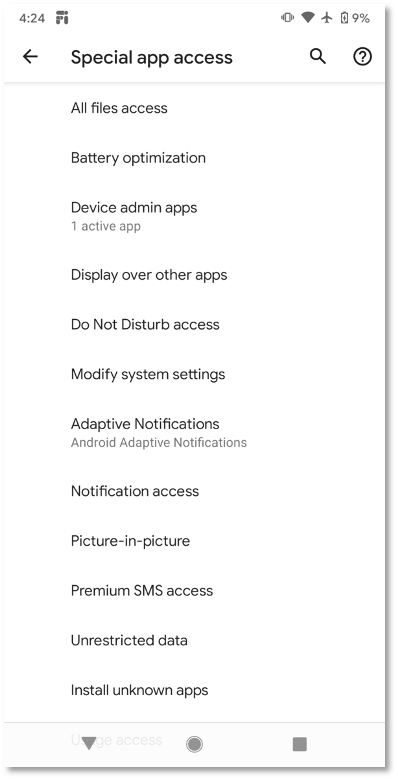
Other special app accesses that are not included in ATT&CK for Mobile are;
- Battery Optimization
- DND mode
- All file accesses
- Adaptive Notifications
- Install unknown apps
- Unrestricted data
- Usage accesses
- VR helper services
- Wi-Fi control
Summering Up
If the Android device is adjusted to be in a uniform approach then managing these special application accesses is not hard, they were simple to detect and prevent unwanted use of it. The special application accesses are taken outside of the regular request. In case the application is required declaration then the other applications are easier to detect. While expanding the mobile knowledge base and developing new techniques, the ATT&K for Mobile is always working to improve mobile security and how to prevent applications from this special application access.