Apple finally released an update for the security patch for macOS, watchOS, iOS, and Safari browsers to fixed the vulnerability that authorize the hackers to execute an arbitrary code on devices and run malicious web content.
This identified vulnerability is tracked as CVE-2021-1844, was discovered and reported to the organization by Clement Lecigne from Google Threat Analysis Group and Alison Huffman from Microsoft Vulnerability Research group.
Why Apple Delivers the Patch?
According to Apple, the vulnerabilities present in the memory corruption issue will execute the arbitrary code execution while processing another crafted web content. Therefore the organization is now addressing the issue and improved the validation.
The update is now available for the devices running iOS 14.4, iPadOS 14.4, macOS Big Sur, and other Apple Watch Series 3 and later one. The update also included the Safari for Macbooks that was executing in macOS Catalina and macOS Mojave.
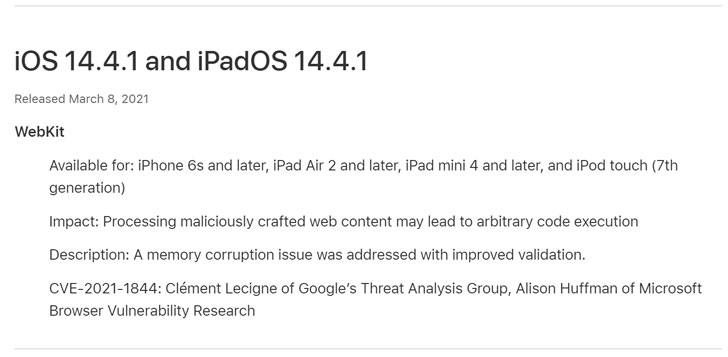
However, the development process fixed the other three zero-day vulnerabilities named CVE-2021-1782, CVE-2021-1870, and CVE-2021-1871 which are fixed in January update. Whereas if we talk about the weakness which authorizes the hackers to bypass the privileges and got access for remote code execution.
The entire issue was later exploited by the team unc0ver jailbreak tool that unlocks every iPhone model running on 14.3 OS.
Summering Up
Multiple experts who find the other activated zero-day bug in the Chrome browser were identified by Google. The experts also added that similar to the Chrome security flaw, there is no proof yet the vulnerabilities is managed or modified by the hackers.
Several users of Apple devices or the users who are running the infected version of Chrome are advised to update their security patch as soon as possible and reduce the risk of these attacks.



