The ACSC (Australian Cyber Security Center) alerts of an increase of LockBit 2.0 ransomware attacks against Australian associations initiating from July 2021. “ACSC has founded an increase in reporting of LockBit 2.0 ransomware cases in Australia,” Australia’s cybersecurity agency said in a security alert issued on Thursday.
As per the agency, LockBit victims also reported threats of having information hijacking during the attacks leaked online, a well-known and most popular technique among ransomware groups to intimidate their targets into paying the ransoms.
Enhancing Number of Attacks since July
“The majority of affected users to the ACSC have been reported after July 2021, showing a sharp and significant increase in domestic victims in negotiation to other tracked ransomware aspects,” the ACSC stated.
“They also observed LockBit affiliates setting up ransomware on corporate systems in a variety of sectors consisting professionals services, construction, manufacturing, retail and food.” The association also posted a ransomware profile with more information on the LockBit group, including first access indicators, mitigation measures, and targeted sectors.
It also founded that these treat actors are hardened and could target companies from any industry sector. Therefore, not being consisted in the list of already targeted sectors does not importantly indicate LockBit’s target won’t switch to other associations.
The ACSC gives mitigations focused on LockBit TTPs (Tactics, Techniques, and Procedures), which consist of:
- Allowing Multifactor Authentication (MFA) on all accounts to block the use of hijacked passwords.
- Encoding critical information at rest blocks the exfiltration of critical information.
- Separating corporate networks and reducing admin rights to block lateral movement and privilege escalation attempts.
- Handling daily backups to restrict a successful attack’s impact.
- Repairing internet-facing Fortinet devices against CVE-2018-13379, a security flaw heavily exploited by LockBit to hijack networks.
Companies impacted by these escalating ransomware attacks or who require assistance are suggested to reach out using ACSC’s 1300 CYBER1 hotline.
From LockBit to LockBit 2.0
The LockBit ransomware group initiated operating in September 2019 as a ransomware-as-a-service (RaaS), recruiting threat actors to hijack networks and encode devices.
Since it starts, LockBit has been very active, with group representatives promoting the RaaS and giving support to various Russian-language hacking organizations.
LockBit revealed the LockBit 2.0 RaaS in June 2021 on their data leak site after ransomware topics were banned on cybercrime forums.
While the warn issued by the Australian cybersecurity agency would imply that LockBit has hit never before seen levels of activity, the ransomware gang is just ramping up their engines again following a slowdown in attacks since January 2021, as shown by the number of ID Ransomware submissions.
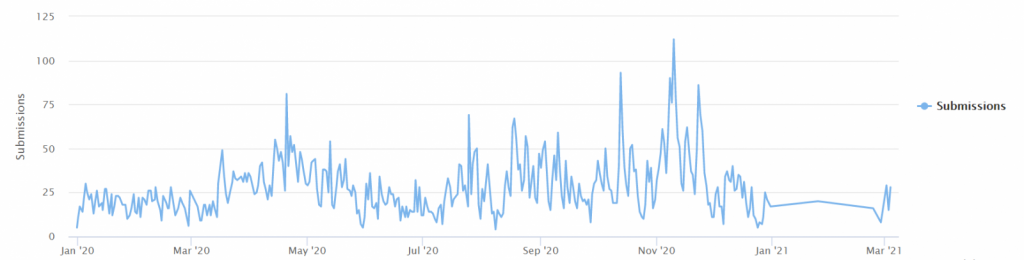
This relaunch came together with redesigned Tor sites and advanced features, consisting of the automatic encoding of devices across Windows domains using Active Directory group policies.
With LockBit 2.0, the group is also trying to remove the middlemen by recruiting insiders who would give them access to corporate networks via Remote Desktop Protocol (RDP) and Virtual Private Network (VPN).
In recent news, the ACSC and the FBI also alerted in May of ongoing and increasing Avaddon ransomware attacks targeting associations from an extensive array of sectors worldwide.