A new ransomware group named as BlackMatter is acquiring access to various corporate channels while promising to include the best functionality from the prominent and now-defunct REvil and DarkSide operations.
Last week, both Recorded Future and security researchers pancak3 transmitted that a new threat actor named ‘BlackMatter’ had posted to hacking forums where they want to buy access to corporate networks.
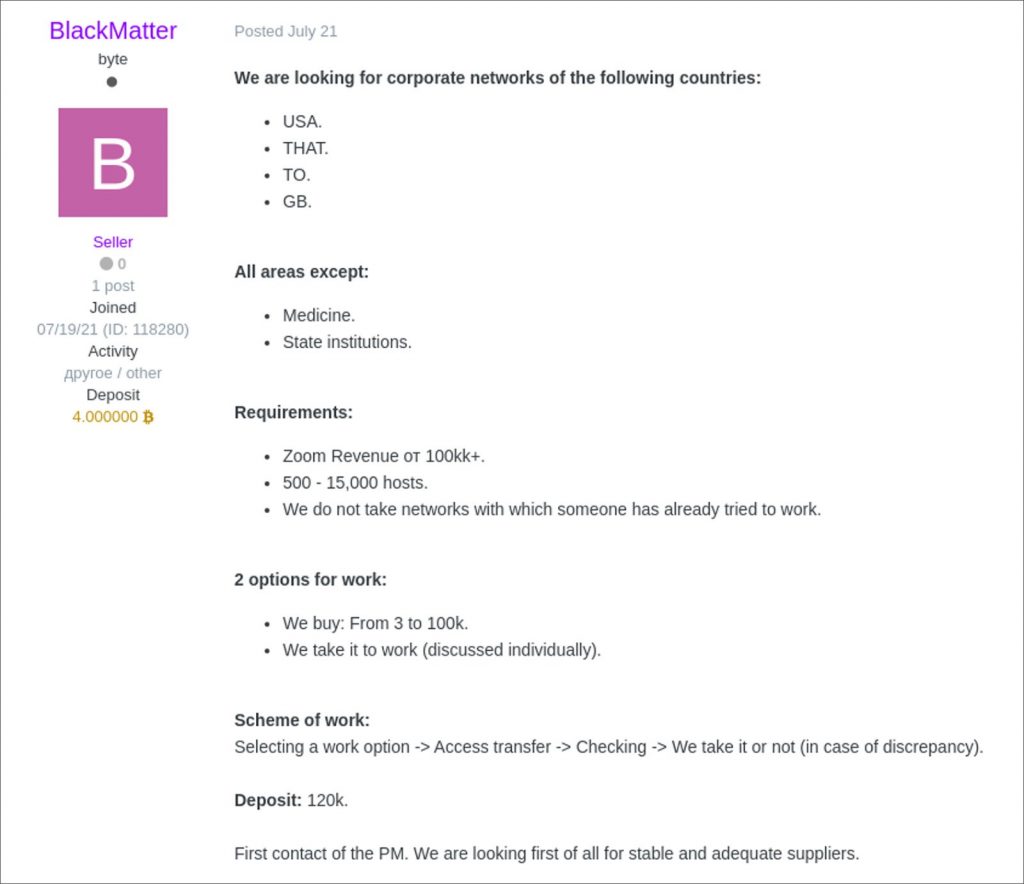
In that post, the threat actor stated that they want to purchase access to the networks in the USA, Canada, Australia, and Great Britain, except for networks associated with medical and government aspects.
Moreover, they shared that they can spend $3,000 to $100,000 per network that follows the given criteria:
- Revenue of $100 million or more.
- The network should contain 500-15,000 devices.
- It should be an advanced network that other threat actors have not already targeted.
To show that they are serious, the threat actors deposited four bitcoins ($120,000) in the Exile hacking forum’s cryptocurrency wallet to pretend that they mean business and we’re serious players.
As forums promoting ransomware are now banned on the XSS and Exploit forums, the threat actors did not show how they would use the network access.
How BlackMatter Ransomware Gang Arrives?
On that day, researchers found that a new Tor data leak site for a ‘BlackMatter’ ransomware operation comes up on the dark web last week.
The name displays that the BlackMatter threat actors are the public-facing representative for the ransomware operation under the same name.
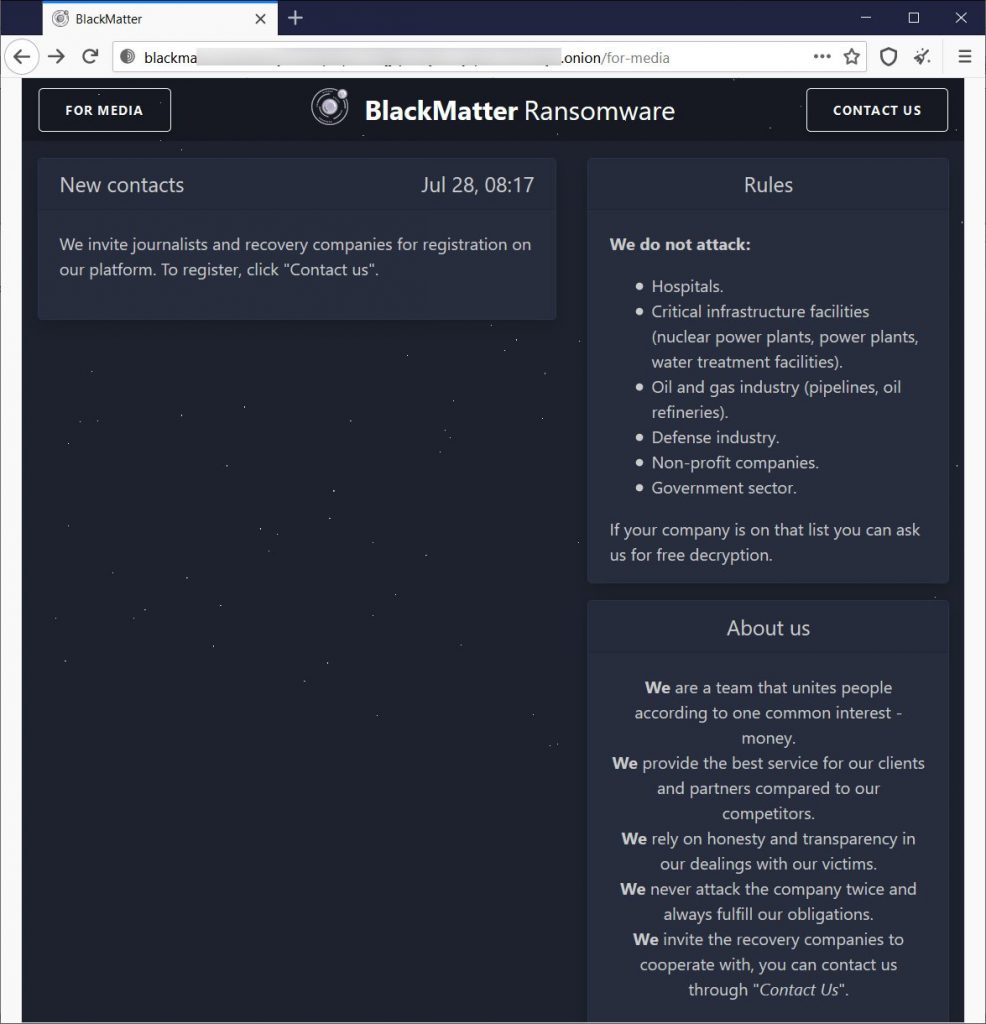
Additionally to posting the data about themselves their operation, BlackMatter states that they will not target any entities in the following industries:
- Hospitals
- Critical Infrastructure facilities (nuclear power plants, power plants, water treatment facilities).
- Oil and gas industry (pipelines, oil refineries)
- Defense industry
- Non-profit Companies
- Government Sectors
Our experts say the gang’s ransomware executables come in different formats so that they can encode various operating systems and device architecture.
“The ransomware is given for several different OS version and frameworks and is transmittable in a variety of formats, which consist of a Windows variant with SafeMode support (EXE / Reflective DLL / PowerShell) and a Linux variant with NAS support: Synology, FreeNAS (TrueNAS), OpenMediaVault.”
“According to BlackMatter, the Windows ransomware variant was now tested successfully on Windows Server 2003+ x86/x64 and Windows 7+ x64 / x86. The Linux ransomware variant was successfully tested on ESXI 5+, Ubuntu, Debian, and CentOs. Supported file systems for Linux consisting VMFS, VFFS, NFS, VSAN.”
At a time, there are no abused users listed on the site. Although, the ransomware group stated that “all blogs are covered for now. For a very short time,” this means that they are currently targeting the users.
Our experts have been able to confirm that there are active attacks in progress and that at least one victim should pay $4 million to the threat actor this week.
Based on the above chart, this is an old-time ransomware operation and most likely a rebrand of one of the larger and now-defunct groups that are recently closed down.
How they are rising from the Ashes of the DarkSide?
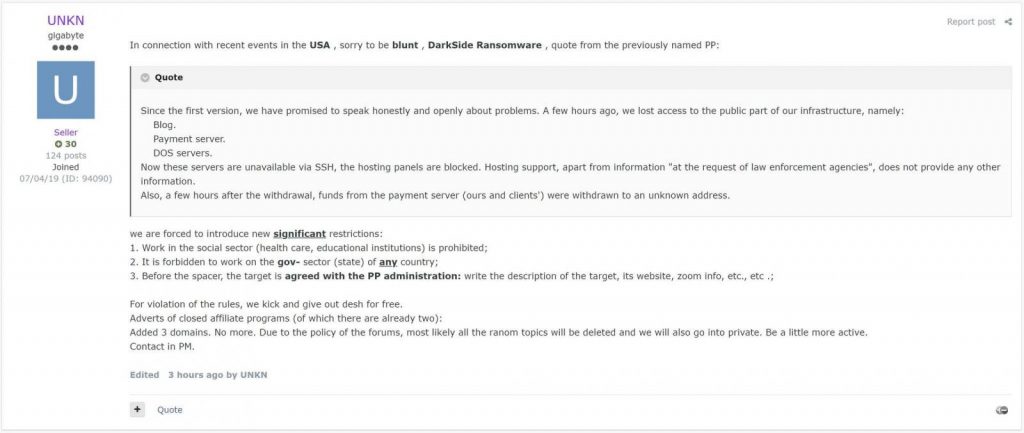
It is discovered by our security researchers as well as the similarities in websites and partners may show that BlackMatter has enlisted or was created by threat actors that were prior with the DarkSide and the REvil ransomware operation.
As ransomware groups were mostly renamed to avoid law enforcement, when we first reported on DarkSide in August 2020, some security investigators and law enforcement believed REvil was rebranding as the new DarkSide operation.
However, both of the groups constantly operating side-by-side for almost a year until DarkSide attacked Colonial Pipeline.
After two months, it was REvil’s turn to close after conducting a massive attack on managed service providers across the world through zero-day Kaseya VSA vulnerability.
Both of the pages are of similar color theme, similar language, a similar way of elaborating to them, and also included a list of targets they would not attack.



