Game developer and author Crytek has confirmed that the Egregor ransomware gang hijacked its network in October 2020, encoding systems and hijacking files containing customers’ personal information later hijacked on the group’s dark web leak sites.
The organizers acknowledge the attack in breach notifications letter sent to impacted victims earlier this month and transmitted by one of the victims with our experts today.
“We want to inform you that Crytek was the victim of a ransomware attack by some unknown cyber-criminals,” Crytek said in a letter mailed to one of their customers impacted in the incident.
“During that attack certain information had been encoded and hijacked from our network. We took urgent action to avoid the encryption of our systems, further secure our environment, and initiate and external researches into the incident.”
Crytek confirmed that Egregor operators later leaked documents hijacked during the incident on their data leak site. “Based on our researchers, the data in some case included individuals’ first and last name, job title, company name, email, business address, phone number and country,” Crytek revealed.
How Data Hijack Impact Downplayed?
The game developer tried to reassure affected customers by saying “the website itself was so hard to identify, so that in our estimation, only few people will have taken note of it.” Crytek added downloading the leaked information would have also taken too long, which would have also likely represented a significant difficulty that stopped people from trying to grab it.
Crytek also believes that those who tried downloading the hijacked information were discouraged by the “huge risk” of negotiating their systems with malware embedded in the leaked documents.
While these points would make sense for users with little to no experience in using computers, most of the users who would want to know how to get their hands on this type of information would likely use downloader’s and launch the leaked files in a virtual machine.
Moreover, threat actors mostly download files leaked on ransomware data leaks to sell or share with other cybercriminals. Considering this Crytek’s attempts to downplay the seriousness of data hijack resulting from the October 2020 ransomware attack does not hold water.

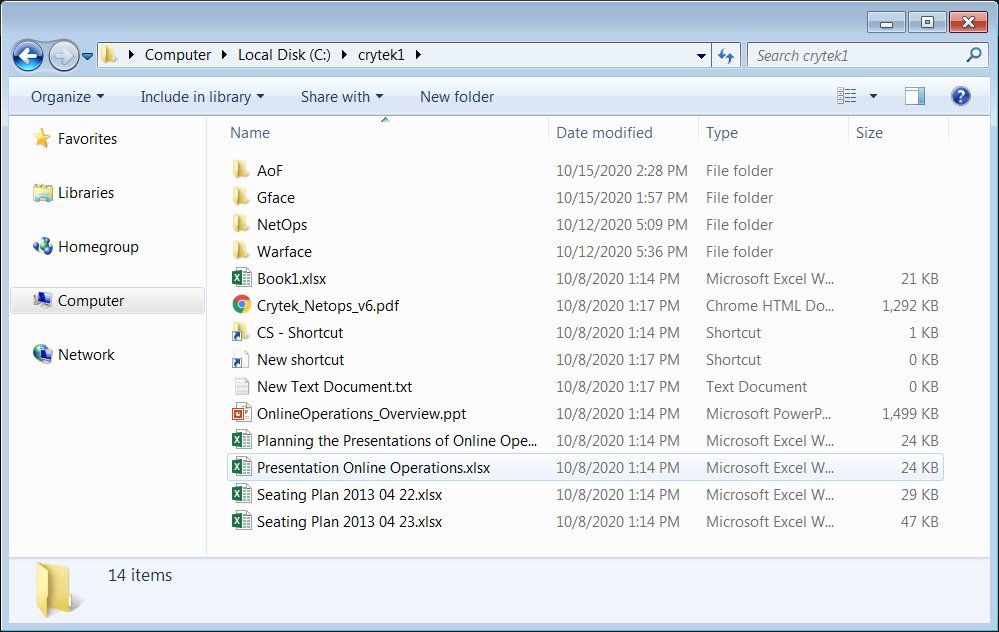
The hijacked data leaked by Egregor on their data leak site included:
- File related to WarFace
- Crytek’s canceled Arena of Fate MOBA game
- Documents with data on their network operations
Other popular organizations across the world attacked by Egregor in the past include Barnes and Noble, Kmart, Cencosud, Randstad, and Vancouver’s TransLink metro system.
Egregor Partners Arrested in Ukraine
In February 2021, some members of the Egregor ransomware operation were arrested in Ukraine following a joint operation between French and Ukrainian law enforcement. Law enforcement officers made the arrests after French authorities could trace ransom payments to individuals located in Ukraine.
The arrested individuals are believed to be Egregor affiliates whose job was to hack into corporate networks and set up the ransomware. At times, Our experts were told by threat actors that Maze’s affiliates switched to Egregor’s RaaS, permitting the new RaaS to open with experienced and skilled hackers.
Egregor operates as a ransomware-as-a-service (RaaS) where the ransomware developers partner with affiliates who conduct the attacks, splitting the ransom payments.
As a part of this arrangement, the core team earns between 20-30% of all paid the ransom, while affiliates pocketed the other 70-80%. A Cybersecurity firm Kivu said in a February report that Egregor has 10-12 core members and 20-25 semi-exclusively vetted members, and it amassed more than 200 victims since its September launch.



