An email-based Windows malware that is working behind several botnet-driven attacks and also leads multiple ransomware attacks destroyed itself from all the infected devices by European Law Enforcement Operation.
Multiple law enforcement authorities located in Germany, United States, United Kingdom, France, Netherlands, Canada, Ukraine, and Lithuania were also included in this international action.
However, the development executed three months after this malware conduct a well-coordinated disruption named Operation Ladybird that is capable to seize and control the servers that are used while executing and running the malware into the network. The investigation displays that more than 700 servers are linked with this botnet’s attack that is operating and neutered from inside and revoking further exploitation.
Meanwhile, the Dutch police also captured two central servers that are situated in the country and were deploying the software update while managing the threat executed by the Emotet. The experts also added that all the infected systems will automatically retrieving the update and after some time the Emotet was removed and the infection will be quarantined.
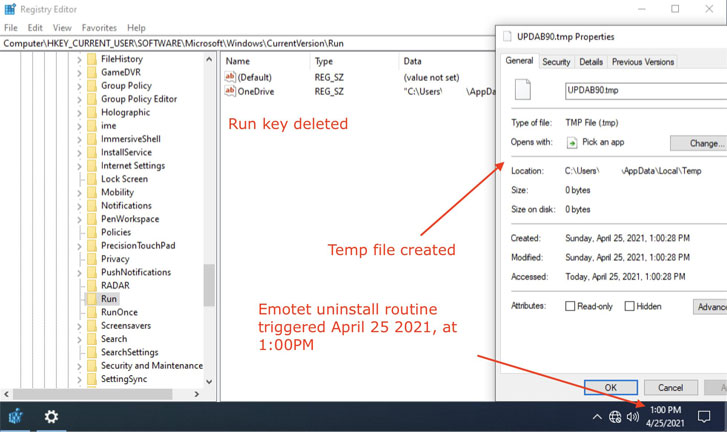
How this Action Executed?
This entire action deals with pushing 32-bit payload identified as EmotetLoader.dll, and it will be transferred over the same channel that the Emotet malware used while compromising the devices. Since the cleanup routine which removes the malware from the affected systems started on 25th April 2021 and the operation worked while removing the malware completely from the devices, it will capable to delete or modify the Registry Key and also terminates the process.
Whereas, on 25th April multiple agencies also confirmed that the Emotet is successfully removed from the infected devices by using the specially-crafted time bomb that was coded and started the uninstallation from the devices and the experts are also saying that all the servers of Emotet are offline and it was seen that the final blow of the botnet may bounce bank in future so they have to remove it completely or it will open the other way for the attackers.
This is the second biggest law enforcement action that was taken by multiple organizations while removing the malware from the compromised machines and the affected systems.
Summering Up
Although the Emotet attackers also took a long break while enhancing the activities and improving the malware, this signifies that there is a high possibility that the attackers may use this opportunity and upgrade the malware accordingly. They could also use the Emotet source code that was left on the devices uses for creating smaller or independent botnets.
United States government is also taking all the legitimate steps that used to remove the web shell backdoors that were dropped by the attacks in Microsoft Exchange server those are located in several parts of the country and that are breached by using the ProxyLogon attack.
The FBI also said that the process of notifying the organizations from which their web shells are removed will affect the attackers who access the system without the administrator’s knowledge.