The attackers are rapidly using Excel 4.0 while initiating the stage vector and mitigate the malware that deals with Quakbot and Zloader. According to the research, these things are identified after the analysis of 160,000 Excel 4.0 documents in between the period of November 2020 to March 2021. In the analysis, more than 90% are classified and found as malicious or dangerous.
According to the experts, the biggest risk for infected organizations and users is that they will face multiple problems while detecting the unauthorized Excel 4.0 document, most of the documents are signed or verified.
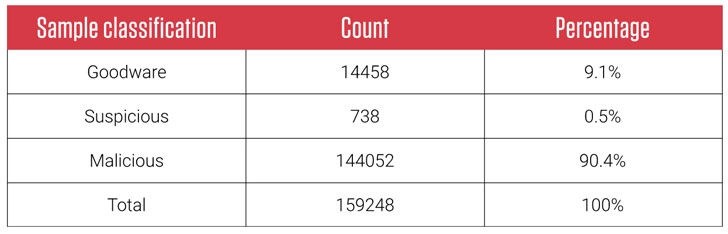
However, the Excel 4.0 macros stores the data in .xlm file format which is the precursor of Visual Basic and it had a legitimate capability that is incorporated in MS Excel for backward compatibility issues. The organization also warns the users that enabling the macros will very dangerous while executing.
Meanwhile, the evolving malware Quakbot was founded in 2007, having the capability of a banking trojan while used to steals the banking data and other financial information and also having the worm-like propagation features. This malware was transmitted using the Office documents and the other version of this malware is also capable to deliver the payloads, store log user keystrokes, or create a backdoor that compromised the devices.

Whereas, in the investigation, the experts analyzed that the malware is not tricked by enabling the macros. It is also tricked by embedded files that hold the XLM macros which are further installed and executed the second stage payload that was controlled from the remote server. Another sample that deals with Base64-encoded payload in one excel sheets, which also tries to download the other files from the malicious URL.
Summering Up
The researcher also added that this backward capability is very important for the applications and from a security perspective it is the best way if these are decrypted at some point at a time. Although those who are holding 30 years of old macros should be weighed against the security risk that is very old and outdated.



