An upgraded phishing campaign is founded that used to target high-profile ranking company executives that worked for real estate, finance, technology, and in the government sector intending to collect confidential information.
The entire campaign was based on social engineering attack that deals with sending emails to the victims and those emails contain fake Office 365 password expire notifications, the email message also contains the link to use the same password that, when clicked, and redirects the users to the phishing page and steal the credentials.

According to the researcher Trend Micro the hackers target high profile executives who are not aware of these attacks and easily got phished and click these malicious links. The attackers target C-level employees, by this the value of collecting the data is increased and the collected data is used for other attacks.
These employee’s email addresses are obtained from the social site LinkedIn, and the hackers sent the notifications, or they purchased the email addresses from the websites that offer CEO/CFO email and social media profile data.
This campaign was started in July 2019 and currently working in its fourth stage(V4) with the upgraded features that we’re able to detect the bot scanning and crawling attempts and provide another content when a bot is detected and secure the main site.
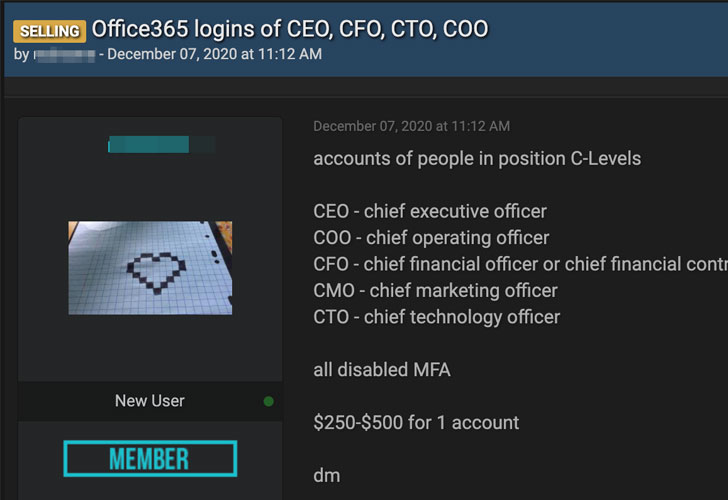
The hackers involved in this campaign are founded to peddle the account credentials of CEOs and CFOs, high-profile executives, and other financial executives, they are also selling the phishing kit on social media pages.
According to the investigation, this malicious link was created to handle users on underground forums that were spotted selling a harvester tool and stolen data account credentials from $250 to $500.
Verdicts
The expert finds out more than 7 compromised sites that were used to hosting V4 phishing kit, these sites are operated by different hackers across the world and scrouge the phishing campaign against the CEOs, board members, presidents, and founder of the companies situated a UK, US, Canada, Netherlands, Hungary, and Israel.
Multiple organizations are aware of these attacks and worried. Organizations that include public-facing websites and platforms are at the risk. They aware their employees that not disclose any data to any public sites that initiate this attack.
Hackers used social engineering techniques to scrouge these attacks easily and get the information from the executives.


![Read more about the article [Fixed] Critical Bug Found Out in NAS Backup Disaster Recovery Application](https://xiarch.com/blog/wp-content/uploads/2021/07/qnap-fixed-nas-backdoor-image-300x158.jpg)
