Even though Microsoft scale its patches for the so-called vulnerability i.e. PrintNightmare for Windows 10 version 1607, Windows Server 2016, Windows Server 2012, it has come to light that the fix for the remote code execution accomplishment in the Windows Print Spooler service can be prevented in few scenarios, efficiently defeating the security protections and allowing an attacker to run malicious code on affected systems.
On Tuesday, the Windows creator concerned about an emergency out-of-band update to address CVE-2021-34527 (CVSS score: 8.8) after the error was accidentally discovered by investigators from Hong Kong-based cybersecurity firm Sangfor late last month, at which point it appeared that the issue was different from another error—tracked as CVE-2021-1675 –that was patched by Microsoft on 8th of June.
What were the Other Security Vulnerabilities were discovered?
Head of the security researcher at Check Point told our experts that “Few days back, two security vulnerabilities were discovered in Microsoft Window’s existing printing mechanism.” These vulnerabilities allow a malicious attacker to gain full control of all the Windows environments that allow printing.
“These are mostly working stations but, at scenarios, this relates to entire servers that are an essential part of every well-know organizational networks. Microsoft considered these vulnerabilities as sensitive, but when they were posted that they were able to fix only one of them, leaving the door open for accomplishment of the another vulnerability,” Balmas added.
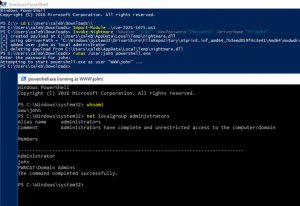
PrintNightmare stems from the errors in the Windows Print Spooler service, which handles the printing procedure inside local networks. The main issue with the threat is that non-administrator users could load their printer drivers. This has now been amended.
What are the Updates Microsoft release for Non-administrator user?
Microsoft added, “After installing this update and layer Windows updates, users who are not administrators can only able to install signed print drivers to a print server.” Analyzing the advancements made to stop the risks associated with the error. “Administrator crucial information will be needed to install unsigned printer drivers on a printer server going forward.”
Publish the update’s release, CERT/CC vulnerability analyst Will Dormann exhorted that the patch “only comes up to address the Remote Code Execution (RCE via SMB and RPC) variants of the PrintNightmare, and not the Local Privilege Escalation (LPE) variant,” thereby permitting attackers to harm the latter to access SYSTEM privileges on vulnerable systems.
Presently, further testing of the update has discovered that exploits targeting the bugs could avoid the remediations absolutely to achieve both the local privilege escalation and remote code execution. To gain this, however, the Windows Policy called “Point and Print Restrictions” must be enabled (Computer Configuration\ Policies\ Administrative Templates\ Printers: Point and Print Restrictions), using which malicious printer devices could be probably installed.
On Wednesday Dormann said “Note that the Microsoft update for CVE-2021-34527 does not efficiently avoid exploitation of system where the Point and Print NoWarningNoElevationOnInstall is set to 1.” Microsoft, for its part, explains in its adversary that “Point and Print is not directly related to this vulnerability, but the technology weakens the local security posture in a way that exploitation will be possible.”
Where Microsoft has approved the nuclear option of stopping and disabling the Print Spooler service, an alternative workaround is to allow security hints for Point and Print and limit printer driver installation privileges to administrators alone by configuring the “RestricDriveInstallationToAdministrators” archives value to avoid regular users from installing printer drivers on a print server. Please message me once right after booking the appointment



