From the current searches, it has been found a new exploit that allows arbitrary information to be uploaded from the devices that don’t have internet connectivity by simply notify “Find My Bluetooth” to nearby Apple devices.
Positive Security researcher Fabian Braunlein said in a technical write-up disclosed last week that “It is possible to upload inconsistent information from the devices which are not connected from internet by sending Find My [Bluetooth Low Energy] notification to nearby Apple devices that then upload the data.”
“Being inherent to the privacy and security-focused design of the Find My Offline Finding system, it seems unlikely that this misuse can be prevented completely.”
The study builds a conclusion by TU Darmstadt published in March 2021, which reveals two specific designs and implementation errors in Apple’s crowdsourced Bluetooth location tracking system that could responsible for location correlation attack and unauthorized access to a user’s location history of the previous seven days.
How this All Started?
The investigation is build-up by the release of a framework known as OpenHaystack that is created to let any user create an “AirTag,” which enables an individual to locate personal Bluetooth devices via Apple’s massive Find My network.
But from the reverse engineering of Apple’s Find My offline finding system also left the door open to the probability that the set of rules could be imitated to upload the inconsistent data to the internet by transmitting the data by Bluetooth beacons that would get elected up by Apple devices in enclosing physical proximity, and then subsequent relay the decode data to Apple’s servers, from where a macOS application can decode, retrieve, and display the uploaded information.
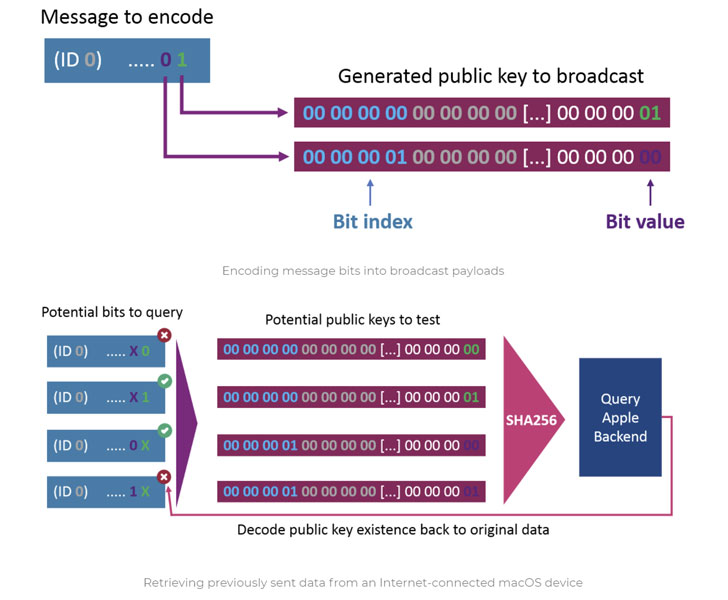
The rotating key scheme is one of the core aspects of Find My device contains pair of public and private keys that are changed every 15 minutes, with the public key sent within the Bluetooth Low Energy advertisement packets.
More on Apple devices such as MacBooks, iPhones, and iPads receive the notification, they fetch their location, then decode the location using the aforementioned public key before dispatching the encrypted location report to iCloud along with a hash of the public key. In the concluding step, the holder of the lost device can use a second Apple device signed in with the same apple id of that lost device to access the exact location.
The encryption protections mean that even Apple does not know which public keys belong to which lost device or AirTag, and also doesn’t have any information of which location reports are considered for a specific user – thus the above Apple ID required. Sir Bradley said, “The security completely fall in the encryption of the location reports: The only way to decrypt the location is the private key, which is unusual to brute force and only stored on the paired Owner Device.”
The whole idea is to escape the gap by encrypting a message into the notify payloads and then retrieve them on the other end by data fetcher elements based on OpenHaystack that decode and fetch the data broadcast from the sender end known as a microcontroller.
Braunstein explained “The data is encrypted in the public keys that are transmitted by the microcontroller. All the nearby Apple devices will get those transmissions and forward the information to an Apple backend as part of their location resporting. Those results can later be fetch by any other Mac device to decrypt the sent data.”
It’s difficult for Apple to standby against an attack of such type due to the built-in end-to-end encoded nature of the Find My network.
Summering Up
To antithetical any possible misuse, the analyst suggests hardening the system in two ways which are validating the BLE advertisement and implement some rate limits on-location broadcast retrievals by caching the hashes and ensures that only “16 new ids are inquired per 15 minutes and Apple ID. It’s credit noting that there is a maximum of 16 AirTags per Apple ID.
“In high-security networks world, it seems to be noteworthy technique for combining lasers and scanners to overcome the air gap, the visitor’s of Apple devices might also become feasible intermediaries to eliminate data from some air gapped systems or Faraday caged rooms,” Braunstein said.



