The security researcher and multiple law enforcement agencies have discovered another new side-channel that can be exploited and leak the information from victims’ web browsers and they can track the users by completely disabling the JavaScript.
The experts said that this side-channel attack doesn’t need JavaScript while executing this signifies that the script blockers cannot revoke it and the attack are also worked event you kick out all the parts of the web browsing experience. These types of attacks are very difficult to identify and prevent without doing proper and deep cleaning of an operating system.
What are these Side-Channel Attacks Contains?
These side-channel attacks are containing the strong architecturally agnostic which results in micro-architectural website attacks that are executed across the world and also include the Inter Core, AMD Ryzen, Apple M1 CPUs, and Samsung Exynos 2100. While the first side-channel attack is executed on the iPhone ARM chip-set.
After the investigation, the experts are also founded that the group of academics that are from Ben-Gurion University, located at the Negev and will be presented at the USENIX Security Symposium performed in August.
These Side-Channel attacks depend on the data like timing, sound, electromagnetic emissions, vibrations, power, and other things that put the effort while inferring the secret data on the system. Particularly these micro-architectural side-channel attacks have also shared the use of processor’s types of equipment across the execution code that protect the different domains and leak information like cryptographic keys.
However, the investigation also states that these previously demonstrated attacks are fully automated such as Rowhammer.js that also relays on the website using the malicious JavaScript that triggers the faults present on remote hardware which gains unrestricted access to the systems of website visitors.
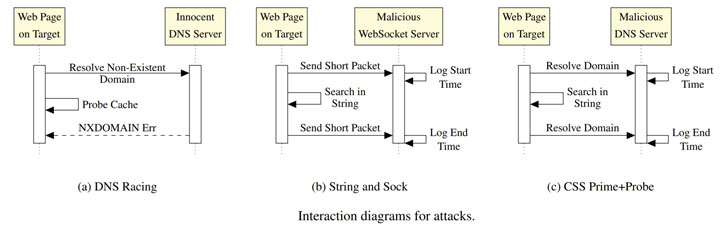
Whereas, these attacks are effectively plugged by the isolated domains that are assisted by the incorporated defense that offers protection against the timing attacks and other fingerprinting attacks that reduce the precision and measures the time functions that added the support to completed disabled JavaScript using addons like NoScript.
Since these latest research also leads that these attacks have week aims that overlap the browser-based mitigations and implement the side-channel attacks also known as CSS Prime + Probe that was made with HTML and CSS files which permits the attackers to attack hardened browsers like Google Chrome, Tor and Deterfox and disabled the JavaScript or have the limited resolution of API timer.
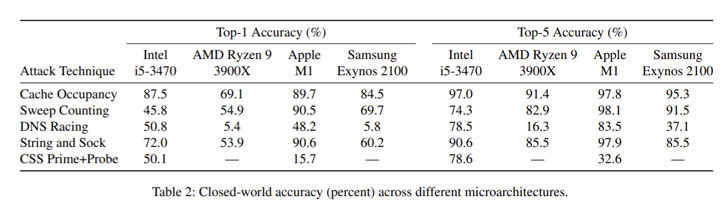
The experts also added that these approaches are having symptomatic that are failed to address the root cause of the attack that mainly used to share the micro-architectural resources that outlined most of the approaches which attempt the attackers to prevent the browser behavior and strikes the balances into the security and another usability.
Summering Up
While evaluating the effectiveness of these attacks the experts also used the side-channel with others and collect the traces of other caches that loads using the other websites which also include the Alexa Top 100 website and use the memory rams while training the deep and neural network model to specified the set of websites that were targeted through the attacks.
Another important factor of these attacks is that the web browser makes the use of other additional shared resources that use the cache memory and operating system DNS resolver tool, network interface, and the GPU that also occupies the cache partition and promised the users for temporal isolation.



