It is very common knowledge that applications make themselves private to user’s data, like location settings and browsing habits. But what if you get to know that some of the applications were even granting themselves to access you crucial information, like your login details? Here are nine android apps that were caught stealing Facebook passwords from their users. These applications, which were freely available on Google Play Store, have recently reported having nearly 6 million downloads between them.
Google intervened to remove all these nine Android apps downloaded more than 5.8 million times from the company’s Play Store after the applications were caught privately stealing user’s Facebook login details.
How these Applications Hijack Facebook Credentials?
Doctor Web said that “The applications were absolutely functional, which was presumed to weaken the caution of potential victims. With that, to access all the app’s functions and supposedly, to disable in-app ads, user were asked to log into their Facebook accounts.” The advertisements inside some of these applications were naturally present, and this procedure was aimed to further restore Android device owners to precede the needed actions.
These malicious applications concealed their malicious aim by guising as photo-editing optimizers, astrology programs, and fitness, only to trap users into logging into their Facebook accounts and steal the entered details via a piece of JavaScript code received from an adversary-controlled server. Security firm Doctor Web has published a report that discovers these Trojan applications.
All these malicious applications which are mentioned above offered real features, causing the unsuspecting users to trust them. They even permitted users to unlock more features and disable in-app advertisements by logging into their Facebook details.
These applications exploited the extensive use of Google and Facebook login something that is offered by many applications and games – to hijack the credentials of unsuspecting users. “After receiving the sensitive details from one of the C&C server into the same WebView. The script directly used to steal the entered login details.”
Further, this JavaScript, using the methodologies provided through the JavaScript Interface annotation, provides the hijacked login credentials to the Trojan application, which then forwarded the data to the attacker C&C server. After that the victim logged into the account, the malware also stole cookies from the current authorization session. Those cookies were also sent to the threat actors.
The list of all those nine apps are Mentioned below:
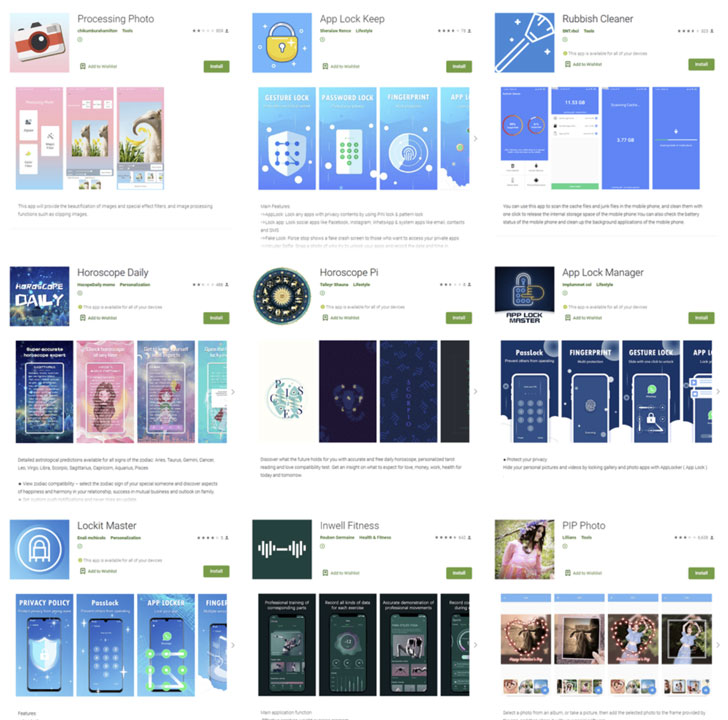
• PIP Photo (More than 5,000,000 installs)
• Processing Photo (More than 5000,000 installs)
• Rubbish Cleaner (More than 100,000 installs)
• Horoscope Daily (More than 100,000 installs)
• Inwell Fitness (More than 100,000 installs)
• App Lock Keep (More than 50,000 installs)
• Lockit Master (More than 5,000 installs)
• Horoscope Pi (More than 1,000 installs)
• App Lock Manager (More than 100 installs)
In the last link of the attack, the hijacked data was eliminating to the server using the malware application.
Whereas the specialized operation comes up to have its sight on Facebook accounts, Dr. Web researchers alerted that this attack could have been easily expanded to load the login page of any appropriate web platform with the intention of hijacking logins and passwords from a variety of services.
A search of Google Play shows that all application has been removed from Play. A Google spokesman said that the company has also banned the developers of all nine apps from the store, which means they will not be permitted to submit new applications. Anyone who has installed one of the above apps should properly examine their device and their Facebook accounts for any signs of the negotiation. Downloading a free Android antivirus app from a trusted security firm and scanning for additional malicious applications is not a bad idea, either.
The most recent announcement comes days after Google revealed new measures for the Play Store, consisting up of requiring developer accounts to turn on two-step verification (2SV), give an address, and verify their contact details as part of its ongoing efforts to action scams and fake developer accounts.
In case of anything, the growth is yet another reminder that users are better off serves by installing applications from known and trusted developers, not to mention go through the permissions request by the applications and always pay attention to other user’s reviews prior to installation.



