On 25th January 2021, Google uncovered an ongoing campaign that was carried out by the attackers from North Korea, now targeting the security researchers to get their confidential information.
The Thread Analysis Group shared on Twitter, Telegram, LinkedIn, Discord, and other social media platforms to communicate with researchers and enhancing their trust.
This entire attack was well planned and was developed to steal the information, to leak the confidential information, or allow them to take this attack on another level.
According to the researcher the hackers created 5 fake LinkedIn accounts and 10 fake Twitter accounts that were used while engaging with the researchers and sharing the videos related to the exploit and also for retweeting the other attacker-controlled accounts.
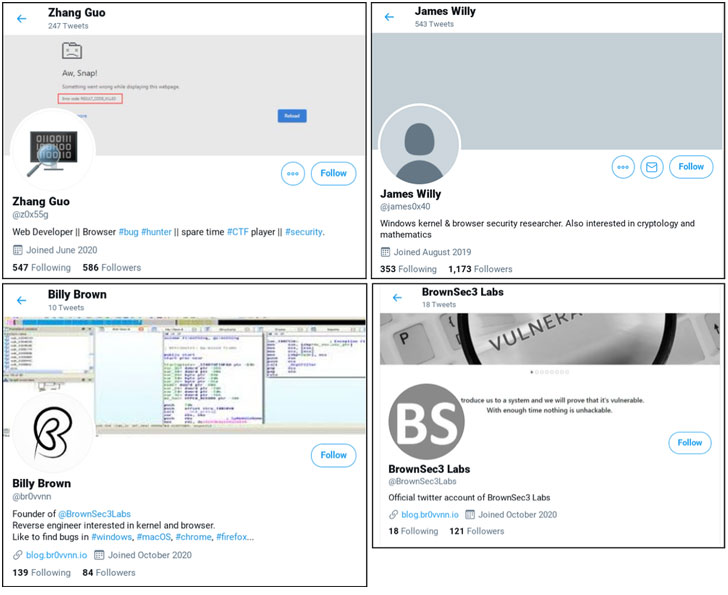
The hackers used a Twitter account to share a YouTube video and the compromised account claimed that the exploit founded under the Windows Defender named CVE-2021-1647 was patched, but in reality, the exploit is fake.
The group of hackers also said that they were used a novel social engineering method to compromise the security researchers by asking them if they are interested in working with them while finding the up comings vulnerabilities together and then the hackers start targeting them with the help of Visual Studio Project.
This project contains the source code while executing the vulnerabilities and install a custom malware that established communication with a remote command-and-control server to run the arbitrary commands on the infected system.
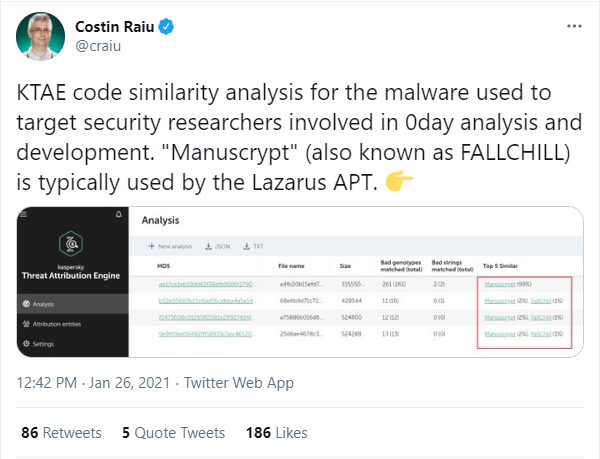
The researcher also said that the malware delivered through the project shared code having similarities with another virus Manuscrpyt, previously known as Windows backdoor created by Lazarus Group.
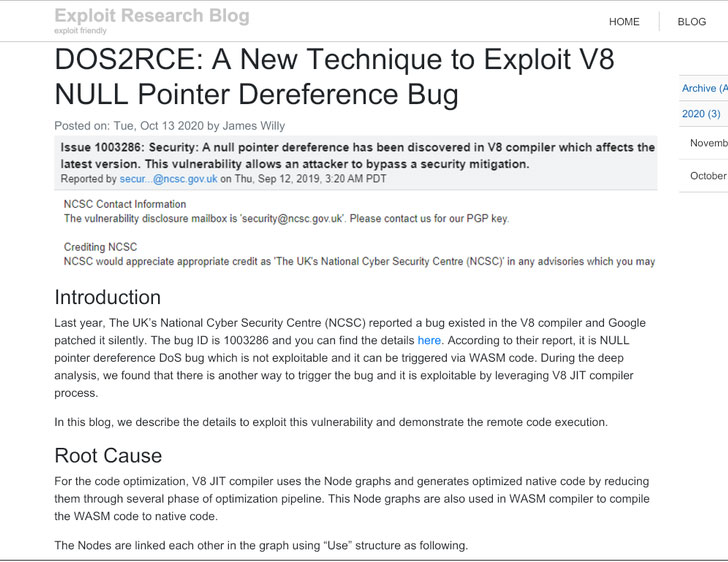
Whereas TAG also said that in several cases where researchers infected after visiting the blog and also by visiting on malicious services that were installed on the machine.
The victim’s system is an up-to-date and fully patched version of Windows 10 and chrome web browser. It is also founded that the attackers are exploiting zero-day vulnerabilities in Windows 10 and Chrome while deploying the malware.
Conclusion
We recommend that you use separate physical or virtual machines for web browsing and interacting with others in the research community. Also, alert while receiving the files from third-parties applications, don’t click on any unwanted links if you don’t want to become the victims of these issues.



