Taiwanese motherboard maker has been hit by the RansomEXX ransomware group, who threatens to publish 112GB of hijacked information is paid. Gigabyte is one of the well-known for its motherboards but also creates other computer elements and hardware, such as graphic cards, information center servers, laptops, and monitors.
The attack appeared late Tuesday night into Wednesday and forced the company to shut down its system in Taiwan. The incident also harmed multiple websites of the company, consisting of its support site and parts of the Taiwanese website.
Customers have also announced concerns accessing support documents or transmitting updated data about RMAs, which is likely due to the ransomware attack.
As per the Chinese news site United Daily News, Gigabyte ensures that they are going through a Cyberattack that harmed a small number of servers.
After analyzing the abnormal activity on their network, they had shut down their IT systems and alert law enforcement.
If you have first-hand information about this or other unreported cyberattacks, you can confidentially contact us on Signal at +16469613731 or on Wire at @lawrenceabrams-bc.
Gigabyte Go Through RansomEXX Ransomware Attack
While Gigabyte has not officially stated what ransomware operation executed the attack, our experts get to know it was conducted by the RansomEXX group. When the RansomEXX operation encoded a network, they will create ransom notes on every encoded device.
These ransom notes contain a link to a non-public page meant to only be accessible to the victim to analyze the decoded of one file to leave an email address to begin ransom compromised. Today, a source transmits our experts a link to a non-public RansomEXX leak page for Gigabytes Technologies, where the threat actors claim to have hijack 112GB of information during the attack.
In a ransom note also seen by our experts, the threat actors state, “Hello Gigabyte (gigabyte.com)!” and consist of the same link to the private leak page provide to us by our source.
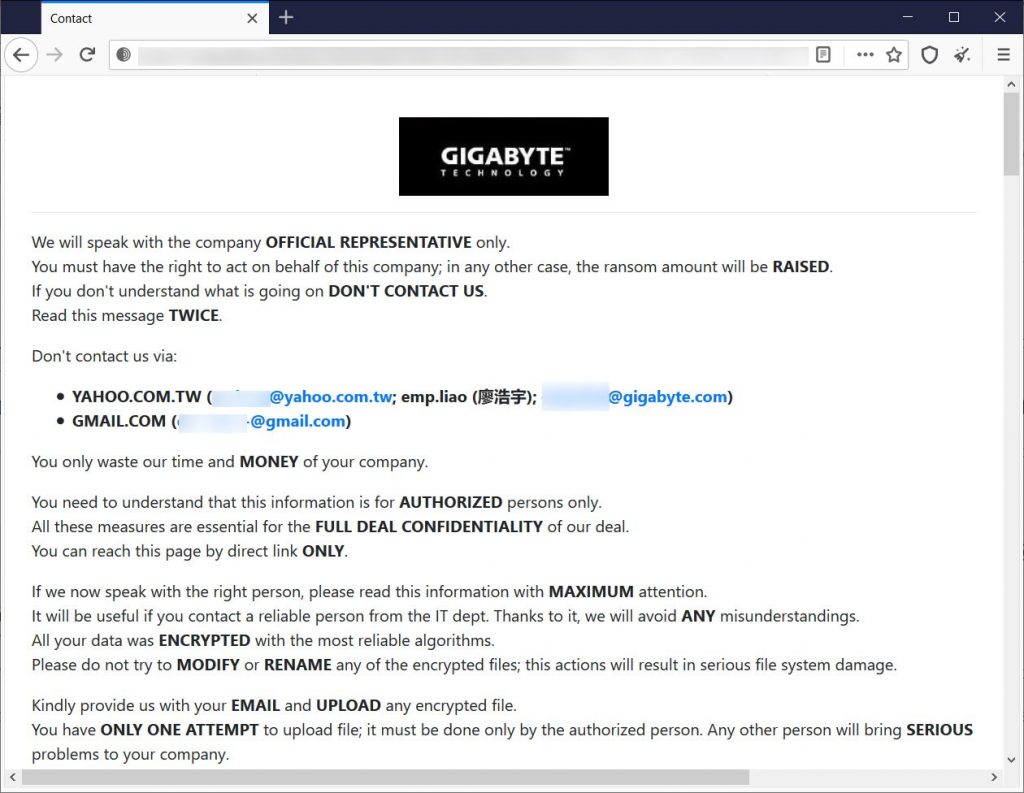
On this non-public leak page, the attackers claim to have hijacked 112 GB of information from an internal Gigabyte network as well as the Americans Megatrends Git Repository. On the private data leak page, the attackers also transmit screenshots of four documents under NDA hijack during the attack.
On the private data leak page, the attackers also transmit screenshots of four documents under NDA hijacked during the attack. While we will not be posting the leaked images, the necessary documents consist of an American Megatrends debug documents, an Intel “Potential Issues” document, an “Ice Lake D SKU stack update schedule,” and an AMD revision guide.
Is it Important to Known about RansomEXX?
The RansomEXX ransomware operation originally started under the name Defray in 2018 but was renamed RansomEXX in June 2020 when they become more active.
Once they gain access to the network, they will grow up more passwords as they slowly gain control of the Windows domain controller. During this lateral spread through the network, the ransomware group will hijack information from unencrypted devices utilized devices used as appropriate in ransom extortion.
RansomEXX does not target Windows devices but has also created a Linux encoder to encode virtual machines running VMware ESXi servers.



