A Ransomware gang has added PrintNightmare exploits to their arsenal and is targeting Windows servers to set up Magniber ransomware payloads. PrintNightmare is a class of security vulnerabilities (tracked as CVE-2021-1675, CVE-2021-34527, and CVE-2021-36) impacting the Windows Print Spooler service, Windows Print Drivers, and the Windows Point and Print feature.
The organization has also posted a security advisory on Wednesday facilitating a workaround for CVE-2021-36958 (a zero-day bug allowing privilege escalation, with no patch available). Threat actors can use these security bugs in local privilege escalation (LPE) or distribute Trojan as Windows domain admin through remote code execution (RCE) with SYSTEM privileges.
How is Ransomware Actively Exploit using PrintNightmare?
As our security researchers founded last month, the Magniber ransomware group is now utilizing PrintNightmare exploits for these exact purposes in attacks against South Korean victims. On the 13th of July, CrowdStrike successfully analyzed and bypass trials at exploiting the PrintNightmare vulnerability, securing customers before any encoded take place, “said Liviu Arsene, Crowdstrike’s Director of Threat Research and Reporting.
After negotiating servers unpatched against PrintNightmare, Magniber drops an obfuscated DLL loader, which gets first inserted into a process and later unpacked to execute local file traversal and encode files on the negotiated device.
In February 2021, Crowdstrike monitor Magniber was being transmitted through Magnitude EK onto South Korean devices launching Internet Explorer unpatched against the CVE-2020-0968 vulnerability.
Magniber ransomware has been actively exploited since October 2017, when it was being deployed through malvertising using the Magnitude Exploit Kit (EK) as the successor of Cerber ransomware. While it startlingly focused on South Korean victims, the Magniber group soon expanded its operations across the world, switching targets to other countries, including China, Taiwan, Hong Kong, Singapore, Malaysia, and more.
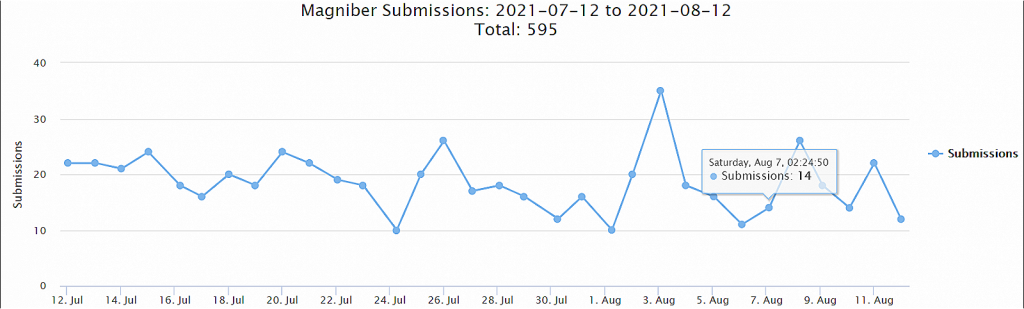
Magniber has been suspiciously active during the last 30 days, with almost 600 submissions on the ID Ransomware platform.
All Attacker Gang Expected to Implement PrintNightmare to their Operations
At the time we only have clue that the Magniber ransomware group is utilizing the PrintNightmware exploits in the wild to target all the probable victims. However, other threat actors (including ransomware groups) will likely join in only if they haven’t already, seeing that there are other reports of in-the-wild PrintNightmare exploitation that have surfaced since the vulnerability was reported and proof-of-concept exploits were leaked.
“CrowdStrike majors that the PrintNightmare vulnerability merged with the setup of ransomware will likely continue to be exploited by other threat actors,” Arsene concluded.
To defend against attacks that might target any user’s network, you are highly suggested to implement any available patches as soon as possible and implement workarounds facilitate by Microsoft to remove the attack aspects if a security update is not yet available.
On July 13, CISA issued an emergency directive ordering federal agencies to mitigate the actively exploited PrintNightmare vulnerability on their networks. The cybersecurity agency also published a PrintNightmare alert on July 1st, encouraging security professionals to disable the Windows Print Spooler service on all systems not used for printing.