Even as a great data breach affecting Air India arrive in the light the previous month, India’s flag carrier airline founds to have experienced separate cyber harm that lasted for the time duration of at least two months and 26 days, new investigations have discovered, which attribute the incident with moderate confidence to Chinese nation-state attackers called APT41.
Group-IB dubbed the association “Colunm TK” based on the names of command-and-control (C2) server domains that were utilized for further transmission with the negotiated systems.
The Singapore-headquartered cybersecurity company states that “The probable consequence of this attack for the entire airline industry and carriers that might yet found traces of Colounm TK in their network is important.”
Whereas Group-IB gives a hint that this may have been a supply chain attack that targets SITA, The Swiss aviation information Technology Company told our researchers that they are two distinctive security incidents.
The airlines also confirmed that SITA on 11 June 2021 that the cyber attack on Air India is not the same or in any way linked to the attack on SITA PSS, SITA stated our researchers.
Also known by other appellation such as Winnti Umbrella, Axiom, and Barium, APT41 is a creative Chinese-speaking nation-state advance persistent attacker known for its association centered on information theft and intelligence against healthcare, high-tech, and telecommunication industry to establish and managing strategic access for stealing intellectual property and committing financially harmed cybercrimes.
“Their cyber crime guidance are most probable to be the apparent among the video game industry targeting, which also consist up of the management of virtual currencies, and pursue deployment of ransomware,” FireEye state it. “APT41 operations against upper level education, travel services and news/media organizations giving some explanation that the group also locates individuals and conduct inspection.”
What happened in the Previous Air Attack?
Air India also revealed on 21 May that a data breach impacting 4.5 million of its customers over a period expanding up to 10 years in the wake of a supply chain attack directed at its Passenger Service Systems (PSS) provider SITA in early February.
The breach consists up of personal information registered between 26 August 2011 to Feb 3, 2021, consisting up the details such as names, date of birth, contact Information, Passport data, ticket data, Star Alliance, and Air India frequent flyer information as well as the credit card information.
FireEye’s Mandiant, which is assisting SITA with the incident revert efforts, has since discovered that the attack was highly sophisticated and that the techniques, tactics, and procedures (TTPs) and negotiate indicator point to a single entity.
What is the New Attack against Air India?

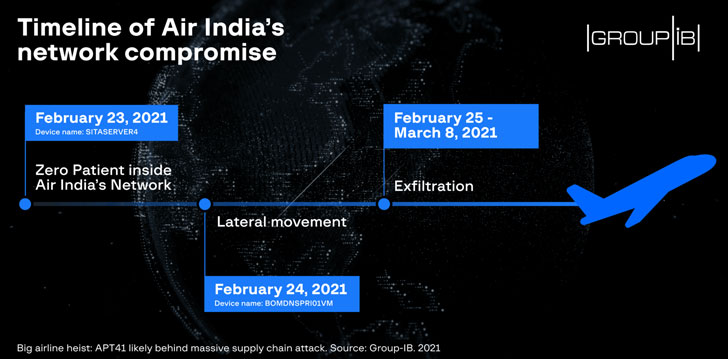
Group-IB’s discovery has now disclosed that at least since the last of Feb, an infected device inside Air India’s network (named “SITASERVER4”) transmitted with a server hosting Cobalt Strike payloads belongs back to Dec 11, 2020.
In this basic negotiation, the threat actor is said to have established persistence and created passwords to pivot alongside the wider network with the intent of collecting information inside the local network.
No more than 20 devices were harmed during lateral movement, an organization added. “The threat actors depart NTLM hashes and plain-text credentials from local workstations via hashdump and mimikatz. The threat actors tired to increases local authorizations with the help of BadPotato malware.”
In all, the attackers extracted 23.33 MB of data from five devices named SITASERVER4, AILCCULHSV001, AILDELCCPOSCE01, AILDELCCPDB01, and the last WEBSERVER3, with the adversary taking around 24 hours and 5 minutes to spread Cobalt Strike beacons to other systems in the airline’s network.
While the starting entry point remains unknown, the truth that “the initial device that started transmitting with the adversary-controlled C&C server was a SITA server and the truth that SITA alert the Air India about its security attack provide reasonable ground to trust that the negotiation of Air India’s network was the outcome of a sophisticated supply chain attack, which might have started with SITA.”
Network to Barium is found based on overlaps between the C2 servers discovered in the adversary infrastructure with those used in previous attacks and techniques employed by the attacker to park their domain.