To trigger the infection chain directly it’s a rule for phishing operations that distribute weaponries Microsoft Office documents to precise victims to enable macros, new researches show that attackers are using non-malicious documents to disable security warnings before run macro codes to harm victim’s systems.
Whereas in yet another detailed information of malware authors constant to emerge their tactics to bypass detections, researchers from McAfee Labs shuffle upon a traditional technique that “downloads and runs malicious DLLs (ZLoader) without any malicious code present in the first spammed attachment macro.”
What is ZLoader?
According to the Cybersecurity Firm, ZLoader infections propagated using this mechanism have been generally reported in the U.S., Canada, Spain, Japan, and Malaysia. The Trojan – a descendant of the notorious ZeuS banking malware – is popular for destructively using macro-enabled Office documents as a basic attack vector to hijack sensitive data and personally discoverable information from users of targeted financial institutions.
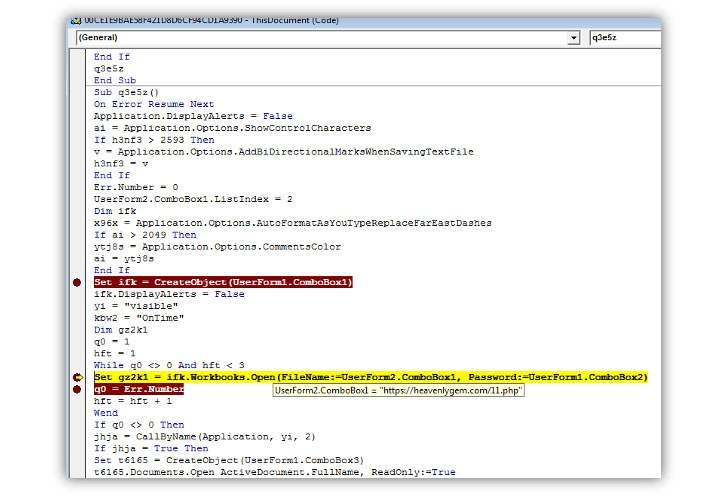
In research the interference, the investigators discover that the infection chain started with a phishing email that contains a Microsoft Word document attachment that, when launched, downloaded a password-protected Microsoft Excel file from a remote server. So it’s worth noting that the micros required to be enabled in the Word document to prompt the download by its own.
How the Attack Chain Works?
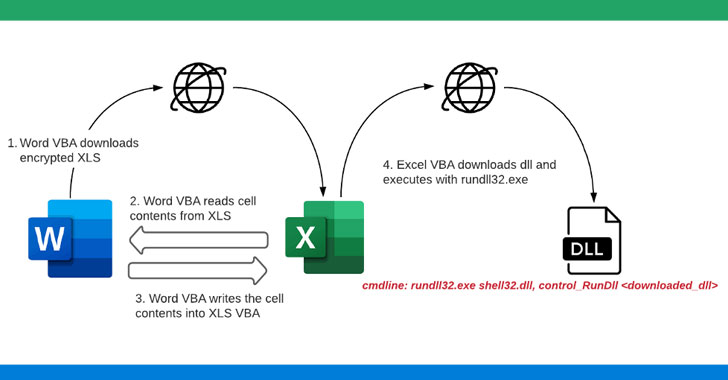
The researcher said that “After downloading the XLS file, the word VBA go through the cell contents from XLS and generates a new macro for the same XLS file and writes the cell contents to XLS VBA macros as functions.” Once the macros are written and ready, the Word document sets the policy in the documentary to ‘Disable Excel Macro Warning’ and targets the malicious macro function from the Excel sheet. The Excel file is now downloading the ZLoader payload. The ZLoader payloads are then run using rundll32.exe.
Providing the “significant security risk” posed by macros, the features are commonly disabled by default, but the measure of count has had an inappropriate side effect of threat actors designing convincing social engineering appeals to manipulate the user into enabling them. By turning off the security warning presented to the user, the attacks are conspicuous because of the steps it takes to circumvent detection and stay under the sonar.
“Malicious documents have been an access points for most of the malware families and these adversaries have been expanding their infection tactics and complexity, not just restricting to direct downloads of payloads from VBA, but making agents dynamically to download payloads,” An investigator said. “Management of such agents in the infection chain is not only limited to Word or Excel, but many more threats might use other living off the land tools to download its payloads. ”



