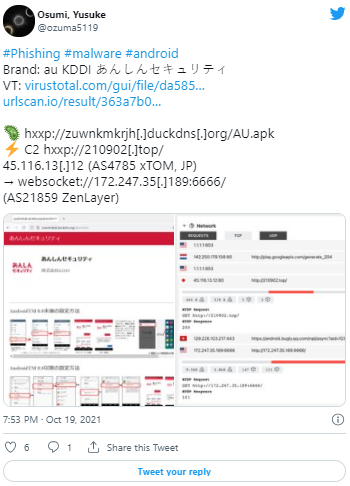
A new variant of the Android info-stealer called FakeCop has been addressed by Japanese Security investigators, who alert that the distribution of the malicious APK is picking up pace. First spotted by a Japanese Security researcher last week, the malware is being assigned in phishing operations imitating in phishing operations impersonating KDDI.
Moreover, the malware is only analyzed by 22 out of 62 AV engines on VirusTotal, showing a united effort by the threat actor to remain hidden.
Concealed as a Well-known Security Tool
In a new report by a cybersecurity firm, investigators have dubbed the malware ‘FakeCop’ and state it is dissembled as ‘Anshin Security,’ a Well-known antivirus product in Japan. After examining the malware, the investigators state that the new spyware variant has the following capabilities:
- Collect SMSs, contacts, accounts information, and apps list
- Modify or delete SMSs in the device database
- Collect device hardware information (IMEI)
- Send SMSs without the user’s knowledge
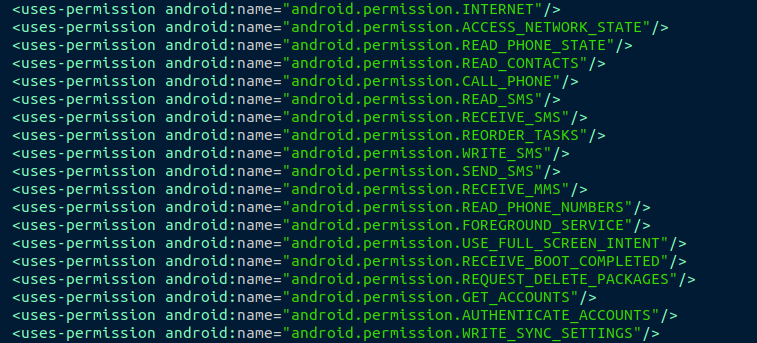
The spyware asks the user to allow various sensitive permissions to execute this functionality, as given below:
While users are met with such requests by AV software, they are more likely to grant them because security software commonly requires higher privileges to scan and remove the analyzed threats.
Attempts to avoid Detections
The malware authors are also utilizing a customer packer to hide the actual behavior of their applications while also circumventing static detection. The malicious code in Bitwise XOR is encrypted and preserved inside a file in the belongings folder, and it can only be unpacked if invoked by a specific application subclass.
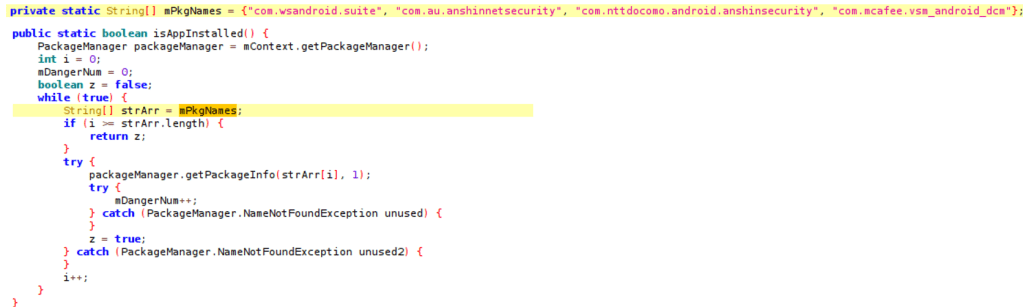
Moreover, Fakecop actively scans the device applications list, and if any antivirus applications are discovered, it pushes a notification to the user asking them to uninstall the hardcoded AV solutions that malware will prompt users to remove include Anshin Security, McAfee security, and the Docomo Anshin scan.
As for how FakeCop reaches the victims, Cybele’s OSINT research revealed two channels of distribution, one via SMS with malicious links and one relying on phishing emails.
The ‘duckdns.org’ free dynamic DNS used as the delivery mechanism has been previously used for distributing Medusa and Flubot, so it’s possible that the current campaign ties to the same operators.
As a general rule, avoid clicking on URL links that arrive via unsolicited SMS and email, and refrain from installing APK files from outside the Google Play Store. Additionally, periodically check and confirm that Google Play Protect is active on your device, and always scrutinize permission requests when installing a new app.



