The activity of the QBot (also known as Quakbot) banking trojan is spiking again, and analysts from multiple security research firms attribute this to the rise of Squirrelwaffle. Squirrelwaffle emerged last month as one of the most likely candidates to fill the void left by the take-down of Emotet, and unfortunately, these predictions are quickly being confirmed.
What are the Advance waves of attacks?
Security researchers at Xiarch have observed a new distribution campaign for QBot relying on Visual Basic Macros (VBA) macros in Microsoft Word documents sent as attachments in phishing emails.
Earlier Qbot operations utilized Excel Macros, which are still present in some situations, even if they are more deficient now.
The victim currently has to manually open the document and “Enable Content” on their Microsoft Office suite to let the macro code execution, dropping a QBot payload on the system.
The rest of the process chain hasn’t changed much compared to previous versions, still downloading a DLL file as the core payload and setting the same scheduled task for persistence as before.
Qbot is also known to partner with ransomware operations to provide them with initial access to a network. QBot has previously collaborated with ransomware gangs to deploy REvil, Egregor, ProLock, PwndLocker, and MegaCortex strains.
We shouldn’t forget that even if these compromises never evolve to file-encryption events, QBot can do significant damage on its own.
The additional modules downloaded by the QBot malware can grab browser cookies, passwords, emails, drop Cobalt Strike, enable lateral movement, and turn the infected machine into a proxy for C2 traffic.
How they Seated the Cache?
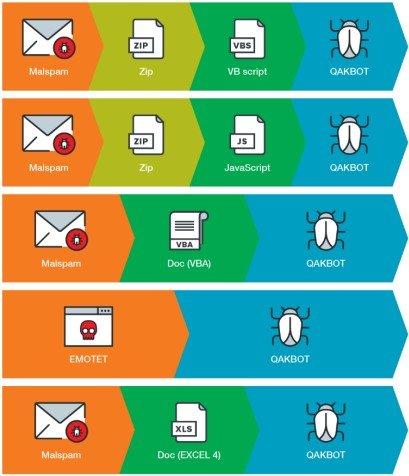
Sentinel Labs published a report on the rise of the SquirrelWaffle malware loader, linking it directly to QBot, which is dropped as second stage malware. Researchers at Minerva Labs have also drawn a similar conclusion, seeing the following delivery scheme:
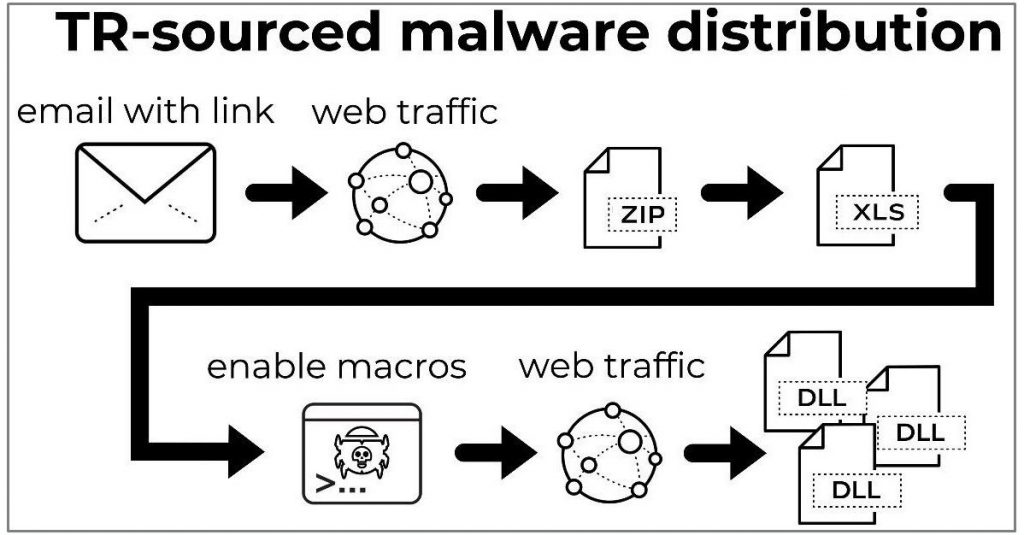
SquirrelWaffle also uses VBA macros to execute a PowerShell command that retrieves its payload and launches it. Unlike Emotet, who used a wide range of phishing lures, the SquirrelWaffle is not doing a great job creating convincing spam mails, keeping the infections in check.
The creation of more convincing phishing emails could be outsourced or quickly resolved by contacting an expert in that part of phishing operations, leading to a more significant number of SquirrelWaffle infections.



