The first public case of the Log4j Log4jShell vulnerability utilized to download and install ransomware has been discovered by investigators. Last Friday, a public exploit was released for a sensitive zero-day vulnerability known as ‘Log4Shell’ in the Apache Log4j Java-based logging platform. Log4j is a development framework that permits developers to add error and event logging into their Java applications.
The vulnerability permits threat actors to create special JNDI strings that, when read by Log4j, cause the platform to connect to and run code at the included URL. These permit the threat actors to easily discover vulnerable devices or run the code supplied by a remote side or through Base64 encoded strings.
While this vulnerability was fixed in Log4j 2.15.0 and even tightened moreover in Log4j 2.16.0, it is being widely exploited by attackers to install numerous malware, which includes coin miners, botnets, and even Cobalt Strike beacons.
First Log4j Exploit Installing Ransomware
Previously, they discover the first ransomware family being installed directly through Log4Shell exploits. The exploit downloads a Java class from hxxp://3.145.115[.]94/Main.class that is loaded and run by the Log4j application.
Once loaded, it would download a .NET binary from the same server to install new ransomware VirusTotal also known as ‘Khonsari.’ This same name is also utilized as the extension for the encrypted files and in the ransom note, shown below:
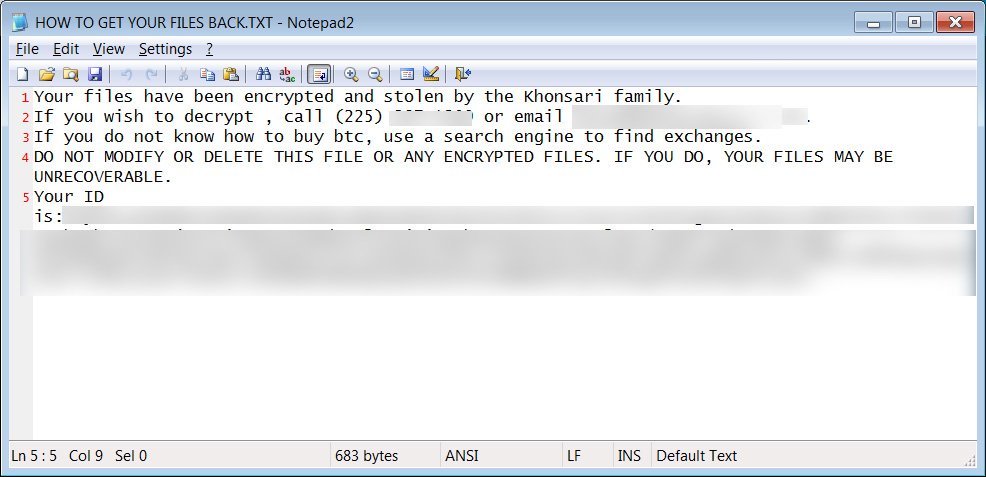
In previous attacks, researchers noticed that these attackers utilized the same server to distribute the Orcus Remote Access Trojan.
Similiar to the Wiper
Ransomware expert Michael Gillespie told our experts that Khonsari uses valid encryption and is secure, meaning that it is not possible to recover files for free. However, the ransom note has one oddity – it does not appear to include a way to contact the threat actor to pay a ransom.
Emsisoft analyst Brett Callow pointed out to Xiarch that the ransomware is named after and uses contact information for a Louisiana antique shop owner rather than the threat actor. Therefore, it is unclear if that person is the actual victim of the ransomware attack or listed as a decoy.
Regardless of the reason, as it does not contain legitimate contact information for the threat actors, we believe this is a wiper rather than ransomware. While this may be the first known instance of the Log4j exploit directly installing ransomware (wiper?), Microsoft has already seen the exploits used to deploy Cobalt Strike beacons.
Therefore, it is likely that more advanced ransomware operations are already using the exploits as part of their attacks.