On Tuesday security researchers discovered the new malware that was adopted by Agent Tesla RAT trojan that is ale to compromise the defense system and monitor the victim’s system.
This entire trojan was worked on social engineering attack as the Windows spyware is not only used to targets Microsoft AMSI. It is working to defeat the endpoint defense mechanism. The trojan also deploys in multi-stage execution and access the Tor and Telegram API to establish a C2C server.
Another cybersecurity firm identifies two versions of Agent Tesla which include version 2 and version 3 those are currently executing and the changes are identified as another sign of Agent Tesla’s constant upgrade. It is designed to develop a sandbox and static analysis which is more difficult.
The experts also determine the difference between these two versions are used to be focused while improving the success rate of the malware against the sandbox defense and malware scanners, those can provide more C2 options to the hacker.
A .NET based information stealer and keylogger has discovered that Agent Tesla is used to deploying the number of attacks that are starting from 2014, and with the upgraded features and incorporated over time that permits the attackers to monitor and stores the victim’s keystrokes, take screenshots, and exfiltrate credentials that include the variety of applications those use FTP, email clients, VPN clients, and web browsers.
How did that begin?
In May, as the pandemic was rapidly growing, multiple malware has detected that spread through COVID-19 themed scam campaigns and try to store the WiFi passwords with the other information that includes Outlook email credentials, extracted through the target systems.
After some time, in August 2020, another version of Agent Malware was spotted with an updated number of applications that used to targeted credential hack to 55, the results are rapidly increasing and then the information is transmitted to the attackers-controlled server through SMTP or FTP.
SMTP is used to transmit the data through the mail server that was accessed by the attacker in 2018, whereas another version was also spotted that used to leverage Tor proxy that includes HTTP communications and other messaging application like Telegram API that have the information to a private chat room.
Additional Outcomes
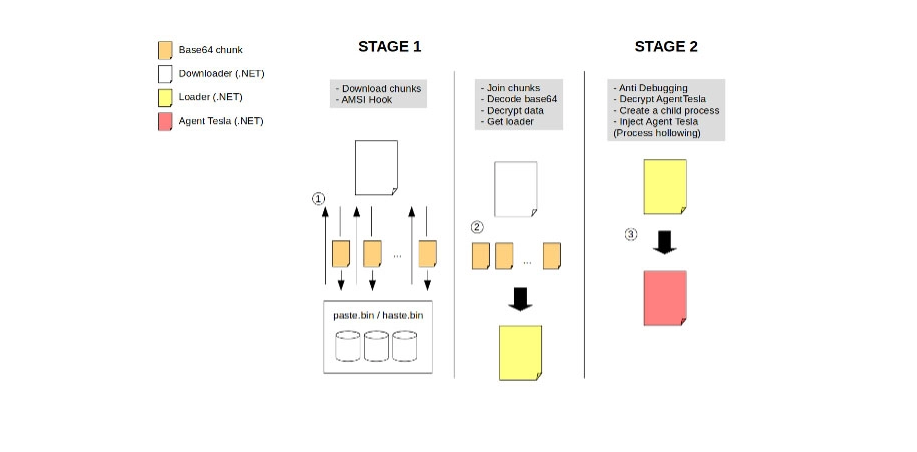
Agent Tesla is also responsible while editing the code in AMSI in a bid to skip the scans of malicious payloads that were fetched by the first-stage downloader and which are responsible for grabbing the base64-encoded code from Pastebin that works as the loader for Agent Tesla malware.
Whereas AMSI is an interface that permits the applications and services to integrate with existing antimalware products that’s are present on a Windows machine.
Apart from this to get the execution, the malware makes the copies of data to the folder that sets the attributed to Hidden and System while concealing it from the view of Windows Explorer.
Remaining Up
The most spreading delivery mechanism for Agent Tesla is known as malicious spam. However, the email accounts are also used to spread Agent Tesla and permits the attackers to compromise the legitimate accounts. Experts advise that all the emails don’t matter whether it is from an organization or individual, always verify the attachments twice before opening them.
This will prevent unauthorized attempts and enhances your privacy and security. Be aware of these malware attacks and conduct a regular awareness session for your workers.



