Investigators recently published information about a suite of 13 vulnerabilities in the Nucleus real-time operating system (RTOS) from Siemens that powers devices utilized in the medical, industrial, automotive, and aerospace sectors. Named NUCLUE:13, the set of bugs affects the Nucleus TCP/IP stack and could be appropriated to obtain remote code execution on vulnerable devices, create a denial-of-service condition, or obtain information that could result in damaging consequences.
The security researchers are the last part of a larger initiative named Project Memoria, which brought together industry peers, universities, and research institutes to examine the security of multiple TCP/IP stacks. Another research that aligns with Project Memoria’s goal is Ripple20 from security research group JSOF, which uncovered 19 bugs in the proprietary TCP/IP stack from the Treck.
What are the Three Code Executions Flaws?
A dozen of the NUCLEUS:13 bugs received the medium and high severity ratings, the one standing out being CVE-2021-31886, a sensitive bug affecting the FTP server element that could permit the attackers to take control of the vulnerable devices.
In a report posted today, the security researchers also note that the issue is due to the FTP server’s improper validation of the length of the “USER” command. This results in a stack-based buffer overflow that could result in DoS and remote code execution (RCE) conditions.
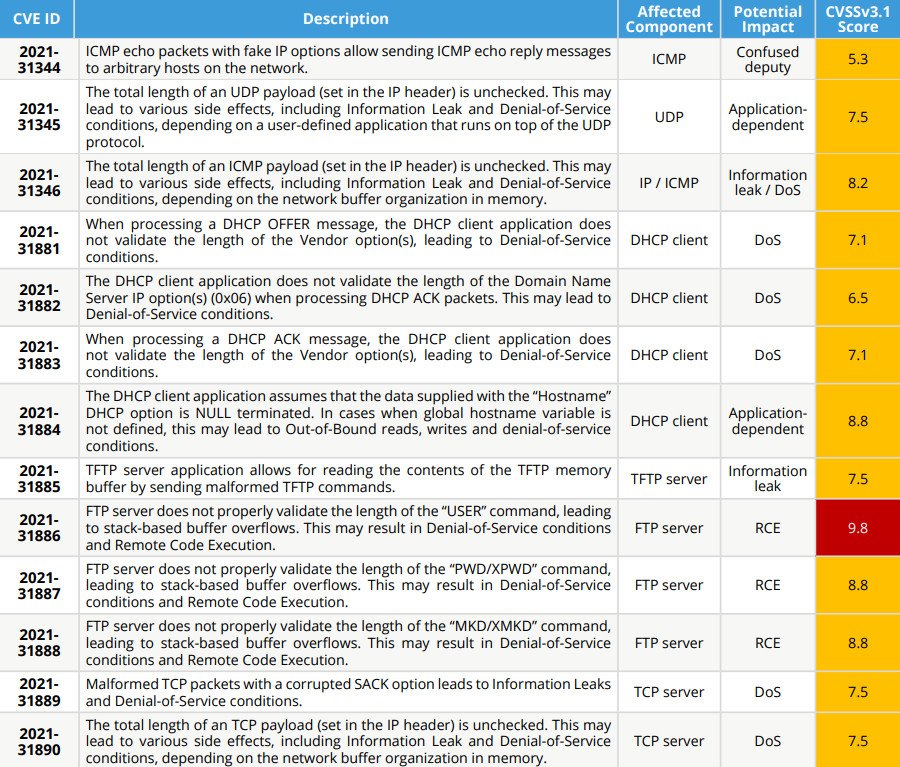
As given in the image above, the two high-severity vulnerabilities (CVE-2021-31887 and CVE-2021-3188) have a probability is the RCE impact, and both affect the FTP server elements. Based on the company’s visibility, over 5,000 devices are running a vulnerable version of the Nucleus RTOS, most of them in the healthcare sector.
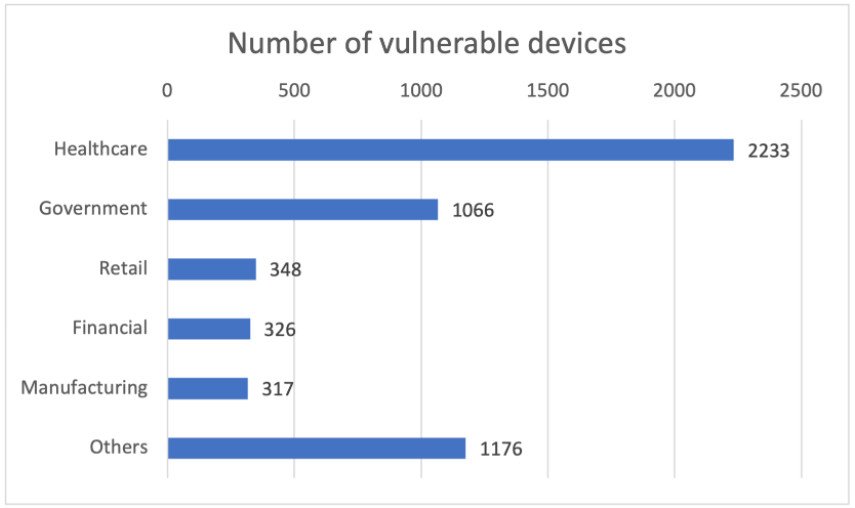
To show how critical NUCLEUS:13 is, security researchers describe two hacking scenarios. One targeted a hospital’s building automation to crash a controller that automatically switched on a fan and lights when someone tries to enter the patient’s room.
In the second scenario, the target was a presence sensor part of the railway infrastructure, which detects when a train arrives at the station and controls how long it stops. By crashing the controller with any of the DoS bugs in the NUCLEUS:13 suite, an attacker could cause the train to run past the station and potentially collide with another train or objects on the track.
How to Mitigate NUCLEUS:13 issues?
Siemens has released updates that fix the NUCLEUS:13 vulnerabilities in Nucleus ReadyStart versions 3 (update to v2017.02.4 or later) and 4 (update to v4.1.1 or later version). An advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) today provides the following general mitigation action:
- Minimize network exposure for all control system devices and/or systems, and ensure that they are not accessible from the Internet.
- Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
- When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing VPNs may have vulnerabilities and should be updated to the most current version available. Also recognize VPN is only as secure as its connected devices.
- The open-source Project Memoria Detector tool can help vendors identify products affected by the NUCLEUS:13 set of vulnerabilities as well as issues uncovered by previous TCP/IP research from the company.
For organizations where patching is not possible at the moment due to the critical nature of the affected devices, Our security researchers provide the following mitigation strategy:
- Discover and inventory devices running Nucleus using Project Memoria Detector, which uses active fingerprinting to find systems running Nucleus
- Enforce segmentation controls and proper network hygiene; restrict external communication paths and isolate or contain vulnerable devices in zones as a mitigating control if they cannot be patched or until they can be patched
- Monitor progressive patches released by affected device vendors and devise a remediation plan for your vulnerable asset inventory, balancing business risk and business continuity requirements
- Monitor all network traffic for malicious packets that try to exploit known vulnerabilities or possible 0-days. Anomalous and malformed traffic should be blocked, or at least alert its presence to network operators



