Security researchers detected an updated novel attack that permits the hackers to trick victims of MasterCard and using it as the Visa card.
In September 2020, the researcher published a report that delivered a PIN bypass attack and permits the hackers to steal Visa EMV-enabled credit card and making a high-value purchase without the cards PIN and the attackers fool the organizations by doing the unauthorized offline transitions.
The research also added that this is not just about mere card brand mix-up, it has its critical consequences. For example, the attackers use the combination to bypass the PIN of stolen cards.
These master card hacks implemented the defense mechanisms works at the network level to lead such attacks. These discoveries will lead to the 30th USE-NIX Security Symposium in August.
What is Card Brand Mixup Attack?
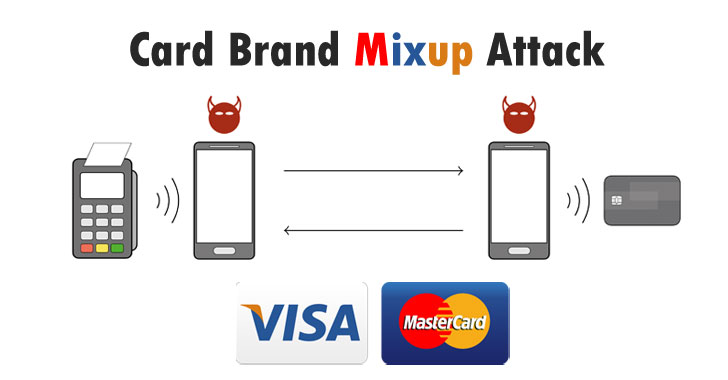
Likewise, in the previous attack that involves the Visa card, this update attack also exploits serious vulnerabilities and widely used as EMV contact-less protocol that is used to target the MasterCard itself.
If we talk about EMV Kernel, it is a set of functions that delivered all the information required while processing the logic and data. This entire attack takes the advantage of the fact that these AIDs are not authorized while making the payment and it is also possible that they deceive the terminal by manipulating the kernel and its extension. The bank that assists the payments on the behalf of the merchant will accept the contactless payments with the help of PAN and AID authorization that is used for different cards.
These hackers perform the Visa transaction through the terminal and MasterCard transaction through the card. However, the necessitates meets the number of queries and the hackers have the access to the user’s cards that being used while modifying the terminal’s commands and the response of the card before the cross verification. Whereas it is not required to root the device or use any other vulnerabilities present in the Android device as the proof-of-concept.
The research also noted that the other vulnerabilities present in EVM contact-less method, that assist the criminals by gathering all the information needed through the Visa protocol from the ones who don’t have the Visa card.
Countermeasures
While securing your card and transaction you should use the PoC android application. The ETH researched also said that the attacker can bypass the PIN used for verifying the transaction with the help of MasterCard or Debit card that deals with two Maestro debit and Master credit cards issued by different banks and whose transaction limit is exceeding $400.
The organizations added multiple countermeasures that deal with using the financial institutions that consist of AID authorization data and permits the cards to check the user’s AID and verify PAN.
The payment network also checks the other consequences of data points present while doing the authorization and easily caught these types of attacks by declining the fake transactions right away.



