Apart from SolarWinds attack, a new supply chain attack is now used to targeting gamers online by manipulating the update mechanism of a free Android emulator NoxPlayer that comes for both PC and Mac OS.
NoxPlayer was developed by BigNox, a Hong Kong-based organization used as an Android emulator that assist gamers to play games on PC using the gamepad, script recording, keyboard, and other multiple instances. NoxPlayer is used by more than 150 million users across 150 countries.
Another operation NightScout that was identified by Slovak cybersecurity firm ESET, that used to target the surveillance campaign that deals with three different malware families through malicious updates to selected no of victims situated in Hong Kong, Sri Lanka, and Taiwan.
Read the upcoming section to know how the experts identified this attack and the working of this attack.
Running of NoxPlayer Spyware
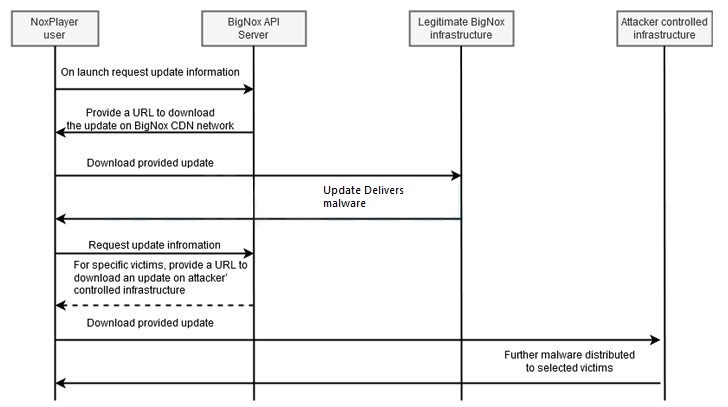
In September 2020, the attack was first spotted while it compromising and executing other malicious activity was reported on 25th January 2020 by ESET.
As per the compromise the software delivered, the experts think that it may show the intent of intelligence and it has the collection of the targets that was from the gaming background.
While the working of this attack depended on the update mechanism. The attackers used the update mechanism of NoxPlayer and then they delivered the trojanized version of the virus to the users. As the updates are completed the delivered spyware had three different payloads that include Gh0st Rat that spy on victims, another one is used to capture keystrokes and the third one is designed to collect the confidential user data.
Pro Tip: Always remember to run a security check after updating any application or software. Do not update the software manually until the organization sends a notification related to that.
The researcher also identified that the additional malware binaries such as Poisnlvy RAT which is downloaded by BigNox (parent company of NoxPlayer) used to establish the remote server by the attackers.
The malware poisonlvy RAT was spotted only in the initial updates and it can be downloaded from the attacker to get the controlled infrastructure. It gets released in 2005, and used in high-profile malware campaigns, mostly are spotted in 2011 used while compromising RSA SecurID data.
Also Read: How Cyber Experts Working Together to Takedown World Most Complicated Malware?
Summering Up
The attacker used malware in this attack are similar to the Myanmar Presidential Office Website attack that happened in 2018, and the data breach on Hong Kong university conducted last year. The experts also said the hacker behind this campaign of BigNox’s, also compromised the API infrastructure.
While make sure you are not affected by this attack simply re-install from clean media and those who are not affected by this yet are advised that do not to download any update by BigNox until or unless the organization sends the notification that they have fixed the threat. Those who are got trapped by this attack are advised to uninstall the software while maintaining their security.



