The Android malware known as BRATA has come along with new and dangerous functionality to its updated version, which consists of GPS tracking, the capacity to utilize various transmission channels, and a function that executes a factory reset on the device to remove all the traces of malicious activity.
BRATA was initially discovered back in 2019 as an Android RAT (remote access tool) that mainly targeted Brazilian users. In December 2021, a report by our experts highlights the emergence of the Trojan in Europe, where it was discovered targeting the users of e-banking users and hijacking their credentials with the involvement of threat actors acting as the bank customer support agents. Our security research constantly monitors BRATA for its new functionality, and a new report posted recently explained how the malware constantly expanding.
What are the Custom Versions for Distinctive Audiences?
The updated versions of the BRATA malware now targets e-banking users in Country like the UK, Poland, Spain, China, Italy, and Latin America. Every variant targets different banks with dedicated overlay sets, languages, and even in different applications to target specific audiences.

The authors use the same obfuscation tactics in all the versions, such as wrapping the APK file into an encrypted JAR or DEX package. This obfuscation successfully avoids antivirus detections, as explained in the below image:
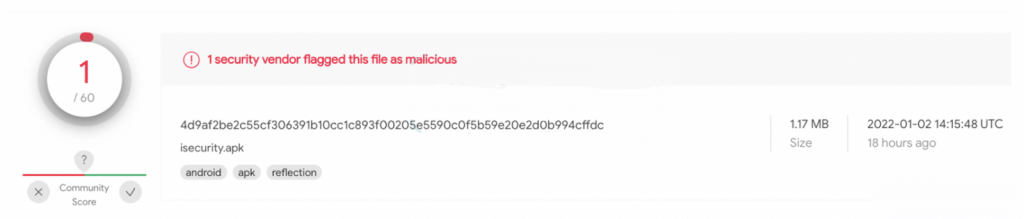
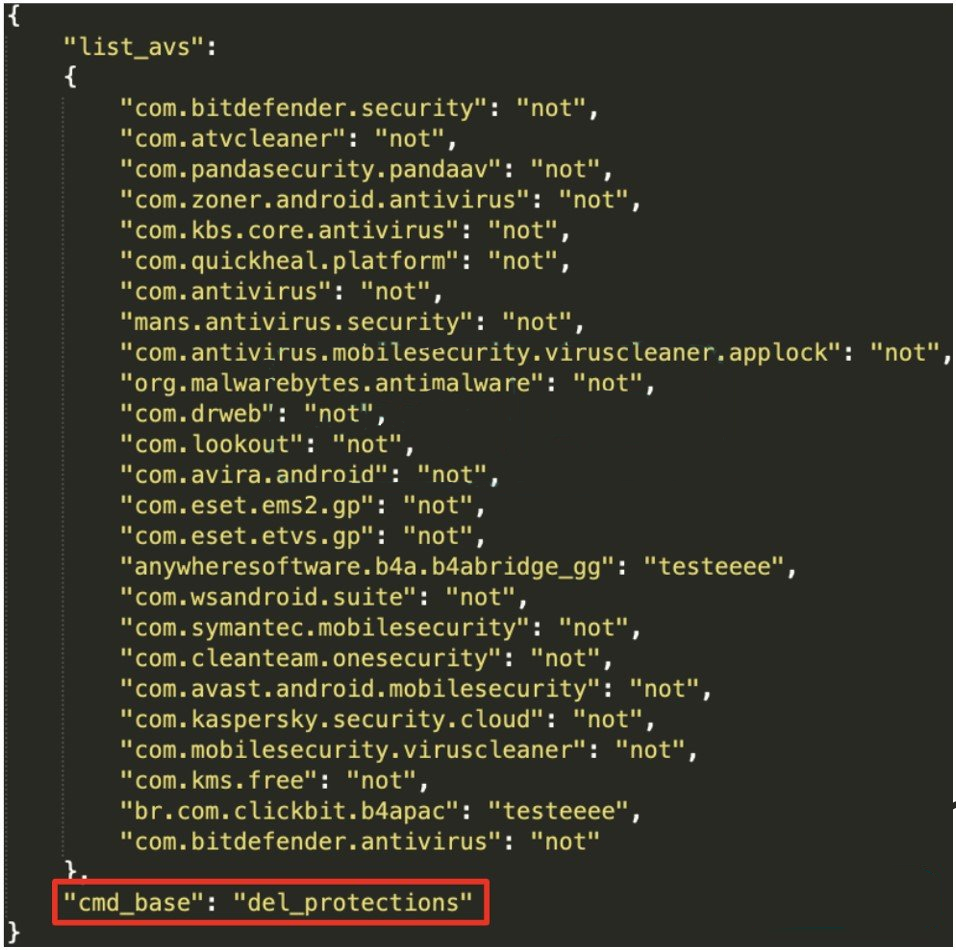
On that front, BRATA now actively seeks signs of AV presence on the device and attempts to delete the detected security tools before proceeding to the data exfiltration step.
What are the Advance Features?
The new features spotted by our security researchers in the latest BRATA update include keylogging functionality, which complements the existing screen capturing function. Although its exact purpose remains a mystery to the researcher, all the new variants also have GPS tracking.
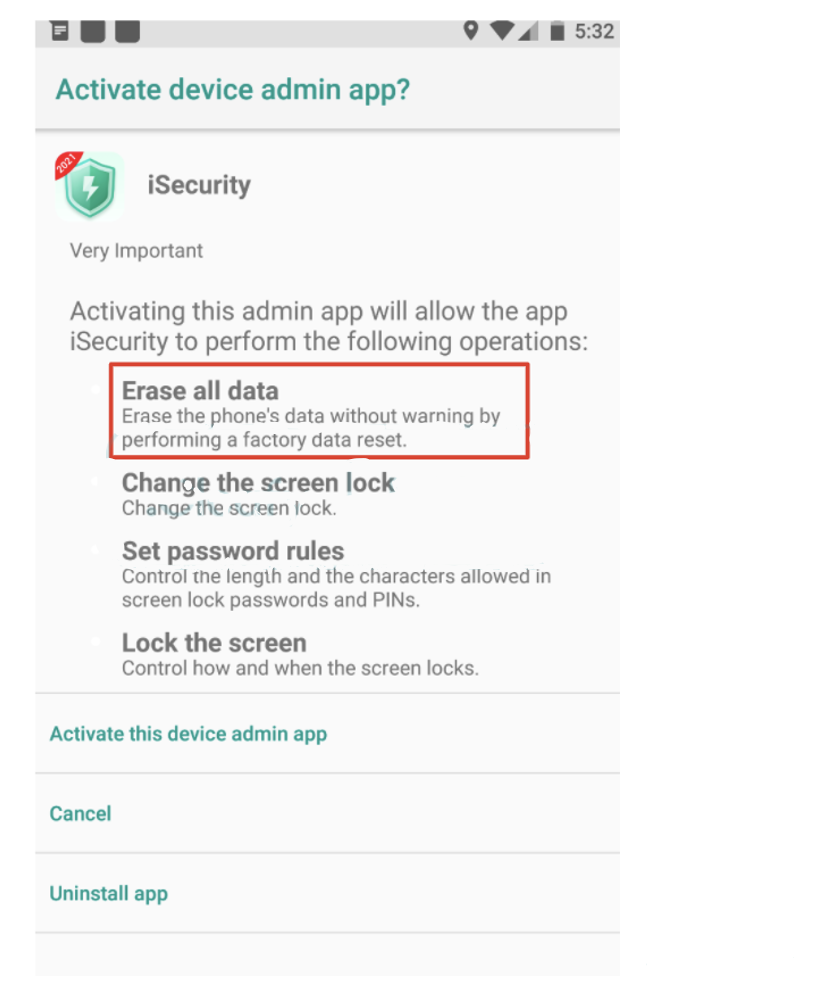
The spookiest of the new malicious features is executing of factory reset, which the actors perform in the following situations:
- The compromise has been completed successfully, and the fraudulent transaction is over (i.e. credentials have been exfiltrated).
- The application has detected that it runs on a virtual environment, most probably for analysis.
BRATA uses factory resets as a kill switch for self-protection, but since they wipe the device, they also introduce the possibility of sudden and irreversible loss of data for the victim.
Finally, BRATA has added new communications channels for exchanging data with the C2 server and now supports HTTP and WebSockets.
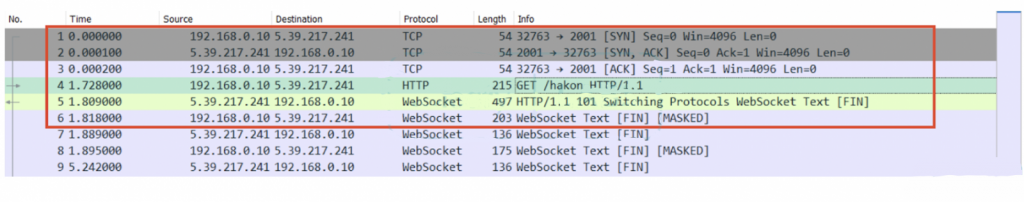
The option of WebSockets gives the actors a direct and low-latency channel that is ideal for real-time communication and live manual exploitation. Moreover, because WebSockets doesn’t need to send headers with each connection, the volume of suspicious network traffic is reduced, and by extension, the chances of being detected are minimized.
What are the ways to stay safe?
BRATA is only one of many Android banking trojans and stealthy RATs circulating in the wild, targeting people’s banking credentials. The best way to avoid being infected by Android malware is to install apps from the Google Play Store, avoid APKs from shady websites, and always scan them with an AV tool before opening.
During installation, pay close attention to the requested permissions and avoid granting any that appear unnecessary for the app’s core functionality.
At last, monitor battery consumption and network traffic volumes to discover any incomprehensible spikes that may be attributed to the malicious process running in the background.



