The new threat is found in malicious Office documents that contain VBA source code only and no compiled code is present. Nowadays cyber attackers are increasingly used VBA code stands for Visual Basic for Applications to penetrate with Microsoft word documents.
This technique was initially identified in February 2020 by Didier Stevens, which involves the use of Visual Basic source code inside the malicious Office documents. In this blog post, we will go to discuss “VBA Purging”. We will explain the entire work of it but before moving towards the VBA Purging, it is important to know about the components of MS-OVA.
Let’s start it…
What is MS-OVBA File Format?
It is a file structure that stores all the data of VBA in a proper hierarchy, which contains different types of streams. Whereas the VBA code used to stored in Office documents is subdivided into two parts;
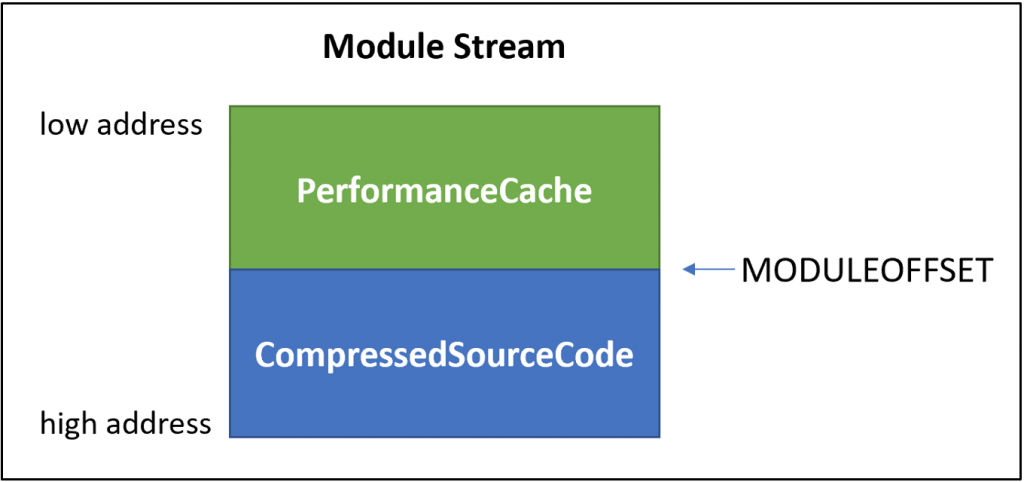
- PerformanceCache (P-Code)
- CompressedSourceCode
The PerformanceCache code is the section that stores the array of bytes the contain compiled VBA code. On the other hand, the CompressedSourceCode contains VBA source code which is compressed with Microsoft proprietary algorithms. Now, look at the VBA purging described in the next section.

What is VBA Purging?
It is a technique, in which a hacker steams VBA code into CFBF (Compound File Binary Format), each VBA module is stored in its stream that contains PerformanceCache (P-code) data, which is the version and implementation-dependent by CSC data (Compressed Source Code).
Office applications used the former code that compiled in the app having its architecture and version. On the other hand, the source code is decompressed, compiled, and executed.
In VBA purging the PerofrmaceCode data is removed and the MODULEOFFSET value is assigned to 0, to make sure that no runtime error has occurred when the applications didn’t find any compiled code present in module steam. MODULEOFFSET is defined as the boundary between PerformanceCache data and CompressedSourceCode data present in Module Stream.
In 2018 this technique is known as VBA stomping in which the VBA source code can be changed or removed accordingly and P-code is executed. In VBA stomping, the compressed VBA code is removed and it gets replaced by non-malicious CompressedSource Code which makes trouble for the attacker. They had to know about the particular version of Office running on the victim’s system.
After that we can also remove PerformanceCache data and leaves the VBA source code ready for execution this is called VBA purging. In a survey, it is observed that the detection rates of VBA purged is 67% less as compared to malicious documents created with the help of normal VBA code.
How to Test VBA Purging?
The company created a new tool to test VBA purging. It supports MS Word, Excel, and MS Publisher called OfficePurge. Using this tool many experts discovered numerous documents that created using VBA purging and it can quickly remove the compiled VBA code and reduce security product detections.
Let’s take an example to understand this technique in a better way.
For this test, we used the tool OfficePurge and a VBA payload from the toolkit Unicorn.
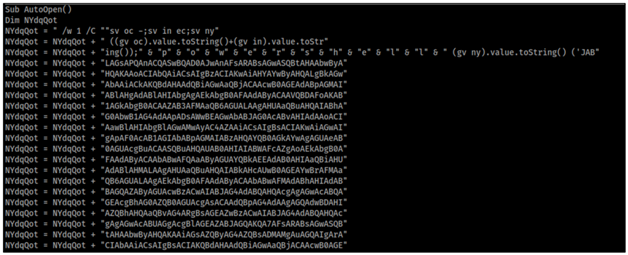
The strings give the output and show Unicon’s Base64 that is encoded in PowerShell payload which is usually detected by many security products.
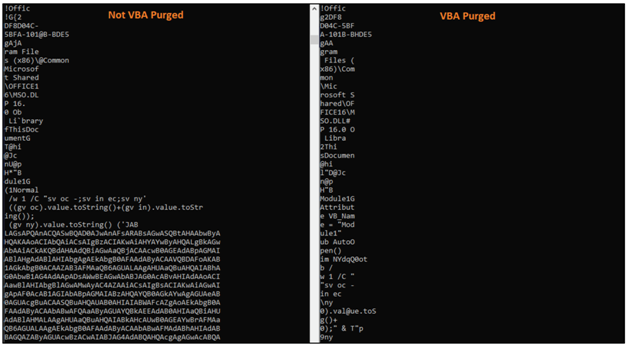
While the PerformanceCache is removed the VBA document doesn’t allow to show the full Base64 code.
On the other hand the CompressedSourceCode still capable to contain the Base64 encoded payload. Whereas the Microsoft custom compression algorithm splits the strings to make it harder for static analysis as shown below.
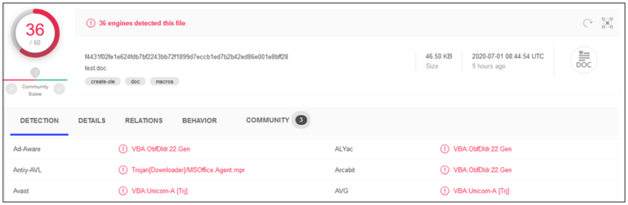
The documents were submitted to online sandboxes to test and detect the capabilities of multiple products. The tool detects the virus rate of the original document is 36/60 which is dropped by 67% once the VBA purged is (12/61). The tool categorized the purged documents as doc and non-purged documents into create-ole, doc, macros.
OfficePurge supports MS Office Word, Publisher and Excel documents created using the principle of CFBF file format.
Many Experts also says that as long as the organizations use Office documents, the hackers will try to get their crucial data. VBA purging is an example of that and it displays how the hackers are busy finding new ways to smuggle data.
While performing this test the software states the numerous malicious documents used by the attackers. As Didier Stevens states that, some public libraries like EPPlus also generate benign documents without the PerformanceCache data.
This solution has some limitations like it lacks to remove VBA stream data completely. Therefore you can choose the YARA rule or you can compare the compressed and compiled version of documents and watch unexpected variations.
Summering Up
VBA purging is used to removes PerforamanceCache data from Office documents with VBA source code without execution code. The attackers are now using different methods like VBA stomping and VBA purging to smuggle the user data. According to the experts, the attackers are continuously enhancing their capabilities. Therefore, they suggest disabling macros if not required or you can also block macros from Online Office for better protection.



