We all heard about this recent SolarWinds Sunburst Backdoor attack but maybe we are not aware of what’s happening inside this attack? How hackers can access the world’s safest organization’s data? How did this attack wake up sleeping, people? Did we find any cure or solution to prevent this? Who spots this attack first? How long has this been going on?
These types of questions may strike your mind! Don’t worry in this detailed write-up we will be going to give the solution to every question one by one related to this SolarWinds Sunburst backdoor attack.
So, let’s start it from the beginning!

Introduction
FireEye on December 13th discovered this global supply chain attack in the update of SolarWinds Orion Platform. The primary motive of this attack is to get access to numerous public and private organizations across the world. The attack was highly sophisticated.
After that many organizations including the FBI, FireEye, Reuters, The Washington Post, and many governments as well as private organizations reported that several United States government, as well as private organizations, was the victims of this breach.
FireEye and Microsoft both published reports describing the working of this attack. Many organizations were believed that this Sunburst Backdoor attack was initiated by Russian Hackers to monitoring the email traffic of the United States.
Along with that, the United States calls a quick National Security Council meeting at the white house on Saturday, The spokeperson John Ullyot from NSC added that they are taking all the necessary and recommended steps to identify all the possible issues related to this attack.
On the other hand, the Russian foreign ministry posted on Facebook to dropout this allegation the Russian minister added that it is another unfounded attempt by the United States media to blaming for the Cyber Security Attacks against the United States of America.

FireEye tracked the SolarWinds Sunburst attacker as UNC2452, whereas other organizations attribute this intrusion to APT29.
SolarWinds also issues a security advisory on 14th December to protect their uses from this attack. But many organizations may believe that this attack was well planned and the attackers were executing this attack from March 2020.
What is SunBurst Backdoor?
The SolarWinds Orion Core business layer is signed by the SolarWinds component that contains the backdoor which is enough capable to establish communication via HyperText Transfer Protocol to third-party servers. The trozanized version of Orion Core is called SunBurst Backdoor.
Working of SunBurst Backdoor Attack?
Moving towards the next question about the working of this attack and how the actors can get hack into government organizations of the United States what is the role of SolarWinds and many more. While talking about the working of this Cyber SunBurst Backdoor attack or to know how the SolarWinds is attached through this entire mess.
The attacker used DLL termed as Dynamic Link Library it is a Microsoft implementation of the shared library concept, the main work of DLL is to authorize the developer to upgrade the functionality of applications without recompiled them with the help of shared code and data.
The DLL file that was compromised during this attack is named SolarWinds.Orion.Core.BusinessLayer.dll the file was digitally signed by SolarWinds along with the valid certification therefore any operating system wouldn’t raise any alarms while executing this file.
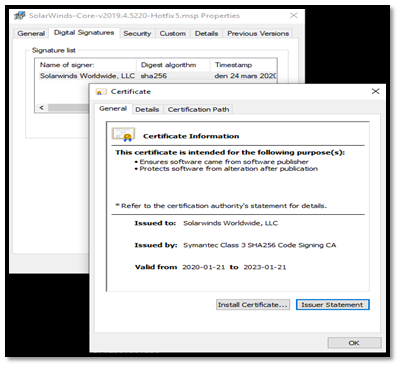
Once it gets installed into the system the file that was created with .dll extension call a remote network using different domains xyzabccloud.com to compromise the data.
By this process, the attackers may get administrative access using the account credentials and they also compromise the SAML tokens. If they are possible to do that then the hackers have gained the access to other accounts and they also managed to update the certificates used by SAML tokens and hacked the Azure AD privileges with compromised details and they get long-term access to the data of an organization. They are enough capable to access the user’s files, emails, and other data.

Impact of SunBurst Backdoor Attack
This supply chain attack caused a major impact on targeted organizations because the installed backdoor is acting as a breach head into the organization network by configuring the TEARDROP and BEACON malware into the network.
The highly confidential information has been leaked from government organizations, cyber industries, and other targeted organizations. More information related to this attack will be disclosed in the upcoming months.
The Hackers can also make money from the leaked information they can also trade stocks if they know about the organizations that give loans or what is the financial information of the organizations.
The cyber experts also believed that the update released by SolarWinds, which served many governments as well as military, intelligence organizations may get affected by this breach.
Prevention and Measures
All the major IT organization such as Microsoft, FireEye, or SolarWinds released their prevention steps to control the spread of SunBurst Backdoor. The organizations released the prevention measures accordingly.
SolarWinds released another update and recommend all their customers to immediately upgrade the new version of Orion Core release 2020.2.1 HF 1, which is available at SolarWinds portal.
In case your organization is not infected by this SolarWinds attack yet than following these preventions given by Microsoft Officials may protect your organizations from this attack.
- Block all known C2 endpoints using your network infrastructure.
- Download and run updated antivirus or any EDR products to detect the compromised .dll files into SolarWinds libraries.
- Disable SolarWinds from your system until or unless you were confident that you haven’t download the infected file.
- Make sure that your service accounts and service principles used high entropy secrets and your certification are stored securely.
- Remove or disable the unused applications and services
For your best security, we also share the SolarWinds Security Advisory for more clarifications and better understanding.

Actions Taken By Government
The United States government is focused to find the attackers the officials say that ” You need to allow yourself to contain the hack as you much as you can investigate” whereas the FireEye officials say that “This is a domino effect and a coordinated attack and they don’t think that they have we’ve seen the end of it.”
The US government confirmed that they were hacked during this SunBurst attack and it also compromised many security organizations like FireEye and over (18000 SolarWinds customers worldwide). The US government officials also confirmed that the US Telecom, US Military, US Pentagon, NASA, NSA, NOAA, FBI get affected.
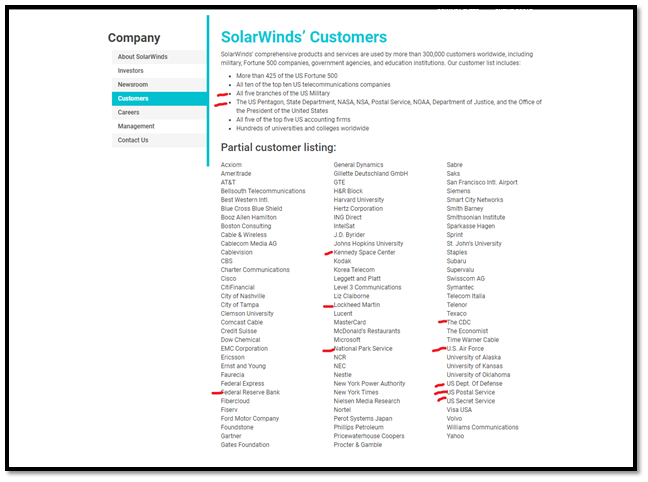
The main reason why hackers targeted SolarWinds is that the organization named SolarWinds provided its services to the entire major governmental as well as top private organizations. We also share the image of SolarWinds customers for your reference.
The Next United States president Biden-Harris also shared a press release related to this SunBurst Backdoor. In this statement, the president says that ” We are working with different organizations and we are investigating thoroughly and I have instructed my entire team to learn as much you can from this breach.” The US president also says that they are going to invest more money in upcoming months to make their country’s security effective.

Unfortunately, these cyberattacks don’t depend on the number of victims it’s relays on quality victims and they succeed in their attack. The SunBurst backdoor attackers are capable to get their high-quality targets i.e… US Government. Some Cyber experts also say that in this attack we don’t know, or may never know about the quality of data and information stolen. The investigations for SunBurst backdoor take months long and its effect could take years.
The list of targeted organizations is already long and it’s getting longer day by day. The investigating organizations may need more time to conclude the list of targets. This attack is highly sophisticated, and the truth is no-one is sure about its impact yet. Also, there is no sign that hackers were going to disable the system or trying to carry out the information.
The US president also says that “There a lot’s of things that we don’t know but what we do know is the matter of concern”.



