Today, another ransomware attack was disclosed by CD Project named as HelloKitty led to another ransomware attack by CD Projekt Red. This ransomware attack targeted encrypted devices connected through the network and steal confidential files from the system.
Yesterday CD project founded that they became infected by the cyberattack that compromised their internal information from the victim’s system.
CD project said that an unidentified attack get access to our internal network and collect the data that was associated with the CD PROJEKT group and after that, the hackers left the note that signifies the ransomware information and released the content to the public.
Whereas some devices that are connected through our network are encrypted and we have a backup of the data leaked. We are taken all the steps while securing our infrastructure and start restoring the data.
According to the cyber expert, this ransomware operation had been running since November 2020 and it gets infected multiple organizations that include the Brazilian power company last year.
What is HelloKitty?
It is malware that is not fully activated, there is no detailed information about it but we have the access to a sample as the victims informed about this attack. HelloKitty is named after the mutex called as HelloKittyMutex and used as the malware is executed to the system.

As this malware is executed, it will repeatedly run the code and start taskkill.exe that was used to close all the security process that was running on the system and it also terminates all the email servers, database servers, backup software, and accounting software. The command which is executed in the victim’s system is;
“C:\Windows\System32\taskkill.exe” /f /im postg*
and this malware also tries to shut all the windows related services that used the command;
“C:\Windows\System32\net.exe” stop MSSQLServerADHelper100
As per the calculations, this malware infected over 1400 processes and Windows services.
Once it shuts down, multiple processes and services are started and they will begin the file encryption on the victim’s system. As it targeted the file extension will be .crypted as described below;
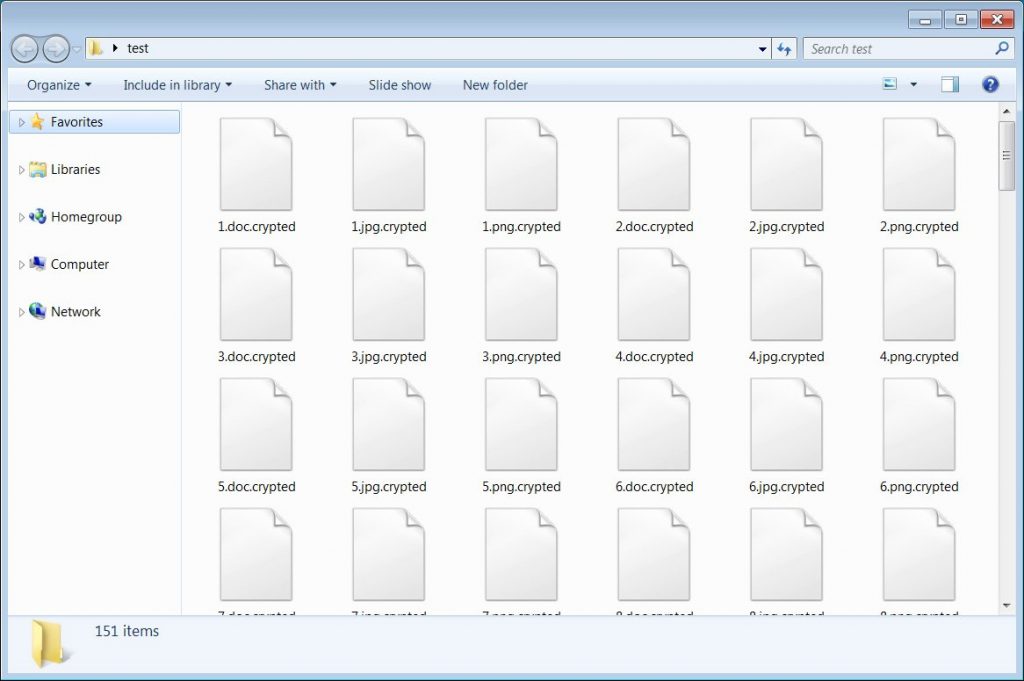
In case the malware targets the secured file then it will occupy the Windows Restart Manager API to terminate the processes and Windows services that are used to secure that file.
HelloKitty is customized and having a different ransom note, this note may change according to the targeted user.
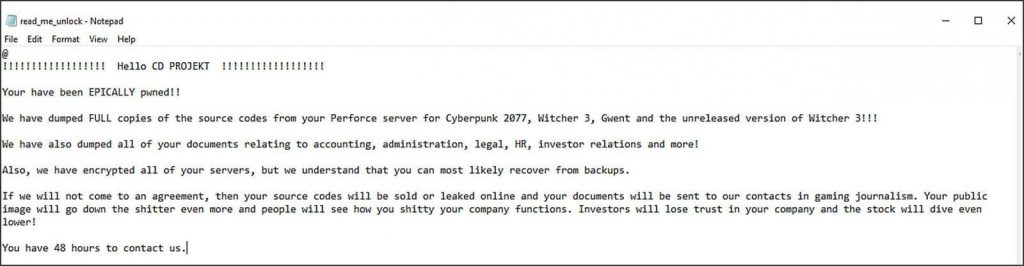
According to the experts, this malware was named “read_me_unlock.txt” which is also used while compromising the CD Projekt data.
Also Read : Another Ransomware Attack that uses DDOS and Forces the Users to Pay the Ransom!
The ultimate feature of this ransomware is customization, once the files are encrypted it left a ransom note according to the data that leaked and the note also depends on the organization that infected. This entire note indicates that the attackers are compromised their system and steal the data as it gets completed the hackers also deliver the ransomware.
Summering Up
This ransomware note is enclosed in Tor dark web URL, as the victims visited that and negotiate with the hackers. Whereas this TOR URL is different for every user that got infected. As the victim opens the URL it shows the chatbox while talking to the threat actors.
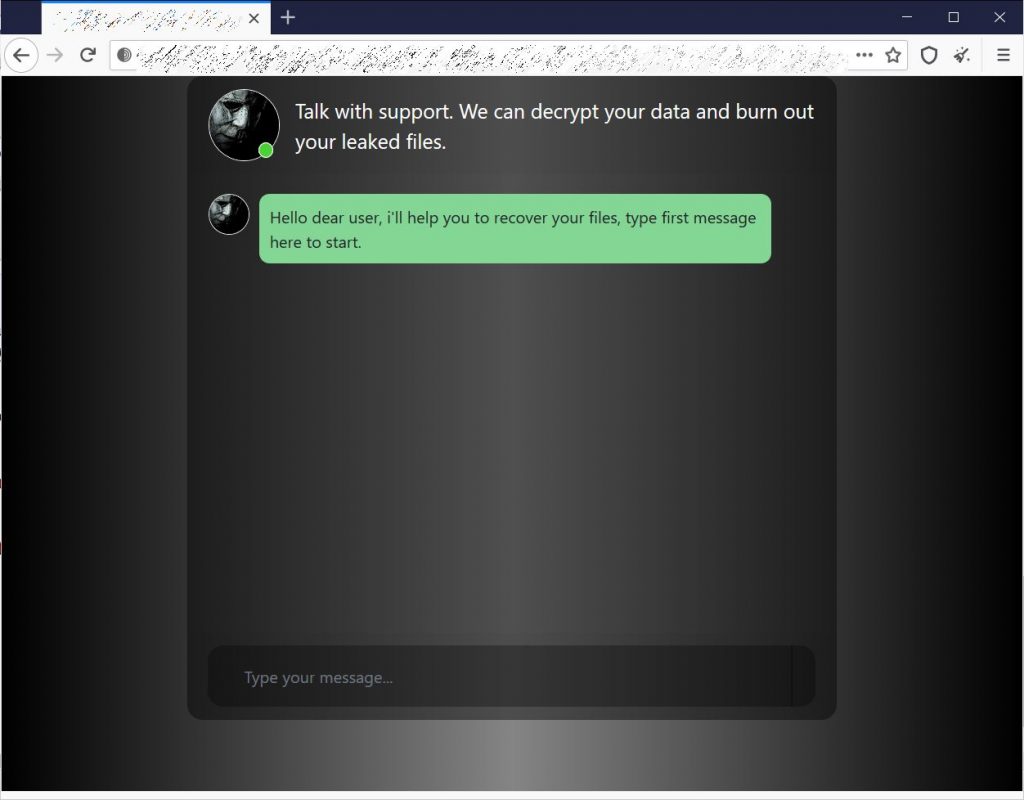
It is still not unknown that how the victims paid the ransom to the attacker and how much they demand. No known weakness is founded that permits the attacker while compromising the victims.



