Attackers who are executing low profile attacks are now using a more updated version of the malware and ceasing the operations for long periods while catching the attention and re-updating their skills to overlaps the radar detection technologies.
A group named FIN8 is now activated and also motivated the other attackers to start executing the banking frauds with the help of a powerful version of backdoor that has upgraded capabilities that also deal with screen capturing, credential theft, proxy tunneling, and other files execution.
How This All Originated?
The group was first identified by FireEye in 2016 and this is well known for retail, entertainment, hospitality, and another type of spear-phishing attacks that used the updated tools like PUNCHTRACK and BADHATCH while stealing the payment card data from the point-of-sale (POS) system.
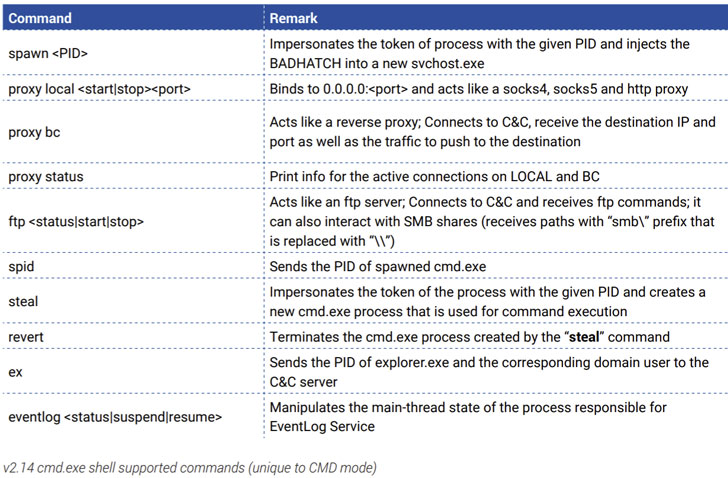
The captured group is also taking long breaks while updating their protocols and enhance the rate of success. The security researcher also said that the BADHATCH malware is more updated and it is a powerful backdoor that occupies several evasion and other defense techniques. This newly updated backdoor also tries to bypass the security monitor with the help of TLS encryption to conceal PowerShell commands.
The backdoor named BADHATCH was founded in 2019 and used as a running attacker that delivers commands that come from the server, while adding the malware to the system or injecting the malicious content to DLLs are also in process. The backdoor is also capable while gathering the system information and exfiltrating data to the server.
However, from April 2020 three different versions of backdoor started from v2.12 to 2.14 are founded. The experts said that the BADHATCH is the latest version of this backdoor that exfiltrate the legitimate services known as sslp.io. It is athwart detection process that occurs during the deployment process and downloads the PowerShell script which executed the code the holds the BADHATCH DLL.
Whereas the PowerShell script is also responsible for executing the persistence that takes care of all the privileges escalation that helps to ensure all the commands post and the script execution that runs on the SYSTEM user.
After that, another version of the evasion technique is also adopted by FIN8 the deals with passing off the communications and command-and-control (C2) server that also trapped the HTTP requests.
Summering Up
Multiple experts also think that this new type of backdoor attack is replacing the old and slow attacks that happened last year. This time the hackers are more focused on insurance, retail, chemical industries, and technologies and targeted the people who are located in United States, South Africa, Italy, Canada, Puerto Rice, and Panama.
Unlike other attacks that were done by cyber attackers, the FIN8 group is constantly updating its tools and methods to avoid unwanted detection. The group is also trying to separate the POS network from the one-time users and also filter out the other emails that contain malicious attachments for further attacks.



