A Taiwan-based NAS maker Synology has recently disclosed that remote code execution (RCE) and denial-of-services (DOS) OpenSSL vulnerabilities affect some of its products. “Different vulnerabilities permit remote attackers to conduct denial-of-services attack or run arbitrary code through an affected version of Synology DiskStation Manager (DSM), Synology Router Manager (SRM), VPN Plus Server or VPN Servers,” the organization explains in a security advisory posted in the previous days.
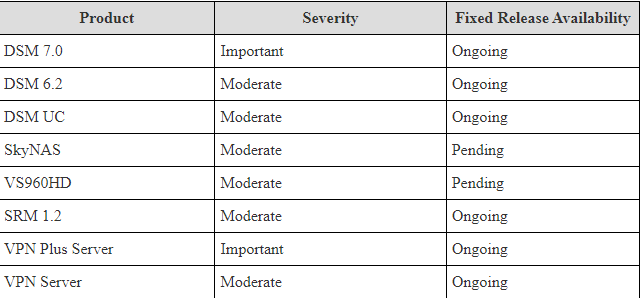
The complete list of devices harmed by the security bug tracked as CVE-2021-3711 and CVE-2021-3712 includes DSM 7.0, DSM UC, SkyNAS, VS96oHD, VPN server, SRM 1.2, VPN Plus Server, and so on.
What are the Patches Arriving Within Next 90 Days?
The initial error is harmed by a heap-based buffer overflow in the SM2 cryptographic algorithm which commonly leads to clash but can also be harmed by threat actors for arbitrary code execution.
Another bug is a read buffer overrun while working ASN.1 strings that can be exploited to crash vulnerable applications in DoS attacks or gain access to private memory data such as private keys or other sensitive pieces of information.
Although the OpenSSL development team has posted OpenSSL to address the multiple bugs on August 24, Synology states that the updates for affected products are either “inprocess” or “pending.”
Where Synology does not facilitate a fixed period for these incoming releases, the organization told our experts earlier this month that it commonly patches harmed software within 90 days after posting advisories.
The DiskStation Manager Vulnerabilities also under Research
The NAS maker is working on security updates for numerous of DiskStation Manager. (DSM) vulnerabilities with no assigned CVE IDs and affecting DSM 7.0, DSM 6.2, DSM UC, SkyNAS, and VS96oHD. “Different vulnerabilities permits remote authenticated users to run arbitraty commands, or remote threat actors to write arbitrary files through a susceptible version of DiskStation Manager (DSM),” Synology said when they publicly revealed these security bugs on the 17th of August.
“Our teams are still actively investigating this potential vulnerability and CVEs will be assigned when more information can be disclosed,” the company told our experts last week when asked to share their CVE ID information on these DSM bugs. Synology also added that attackers haven’t yet exploited the vulnerabilities disclosed in last week’s advisory in the wild.
Earlier this month, the company alerted the customers that the StealthWorker botnet is now targeting their network-attached storage (NAS) devices in brute-force attacks that lead to ransomware infections.