Federal Bureau of Investigation issues an alert that reveals the weak spot of Mamba ransomware find-out in the encryption process that helps the infected organization to recover their data without paying anything to the attackers.
While issuing the alert FBI also warns the organization that Mamba ransomware is trapped both the public and private organization it also infected the local government organization, legal services, technology service, transportation, commercial, industrial, construction business, and manufacturing units.
How Mamba Ransomware Works?
Mamba ransomware or known as HDDCryptor relies on the open-source software named as DiskCryptor that encrypts the victim’s computer’s data in the background and opens with the key that the hackers had.
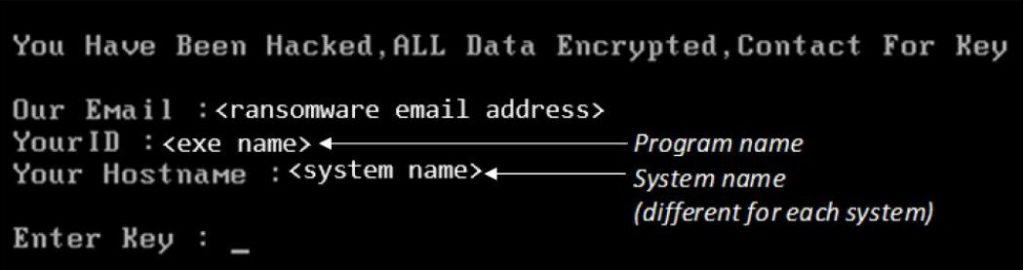
However, the FBI also explains that while executing the DiskCryptor malware the system gets restarted because it needs some necessary drivers, the entire process will take approx two minutes while installing the entire malware.
After that, the software stored the encryption key at the shutdown time and stored this key on the file named myConf.txt located in DiskCryptor’s configuration.
Once the encryption process is completed the system restarted and now the ransom note is visible for the user, hence there is no protection around the encryption key which is stored in the plain text. According to the investigation, the FBI says that this two-hour gap is an opportunity for the infected organizations to recover their data from the Mamba ransomware.
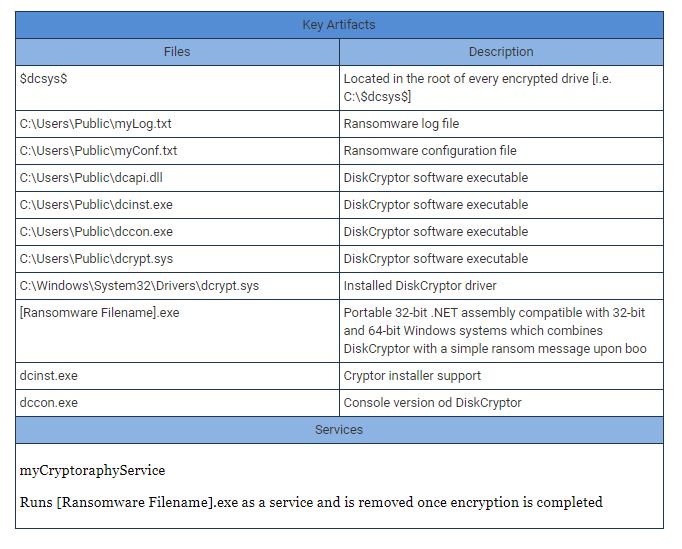
On the other hand, the FBI also provides the following details of some artifacts that may help the organization to detect the Mamba ransomware attack.
Summering Up
The FBI also added that “In case any DiskCryptor files are detected, the attempt should be made while determining that if the myConf.txt is still accessible and then the password can easily be recovered from the system, without paying the ransom. This entire process is valid for two-hour of infection or for the second time the system restarted.
Mamba ransomware is started increasing its victims with the updated variant that was discovered in 2019. According to the report of Cover, the Mamba ransomware is in the list of top-five and this is now shifted on the fourth no in 2020.
This malware is also capable to overwrite the disk’s master boot record (MBR) and prevent access to file encryption on the drive. This makes it more difficult to track as the files are not examined using automated services.



