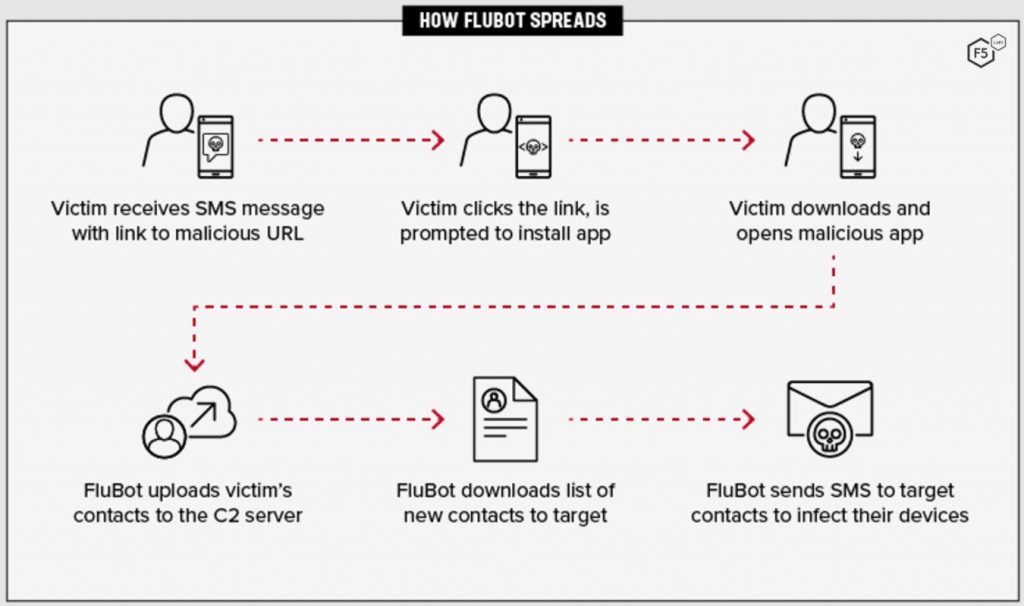
The extensively appropriated FluBot malware extends to emerge, with new campaigns allocating the malware as Flash Player and the developers adding new features. FluBot is an Android banking trojan that hijacks credentials by displaying overlay login forms against many banks across the world.
The SMS Phishing (smishing) allurement for its distribution consists of fake security updates, fake Adobe Flash, Players, voicemail memos, and acts like parcel delivery notice. At once the device, FluBot can hijack online banking passwords, send advance smishing messages to all their contacts, it commonly spreads like wildfire.
Why Imitating as Flash Player?
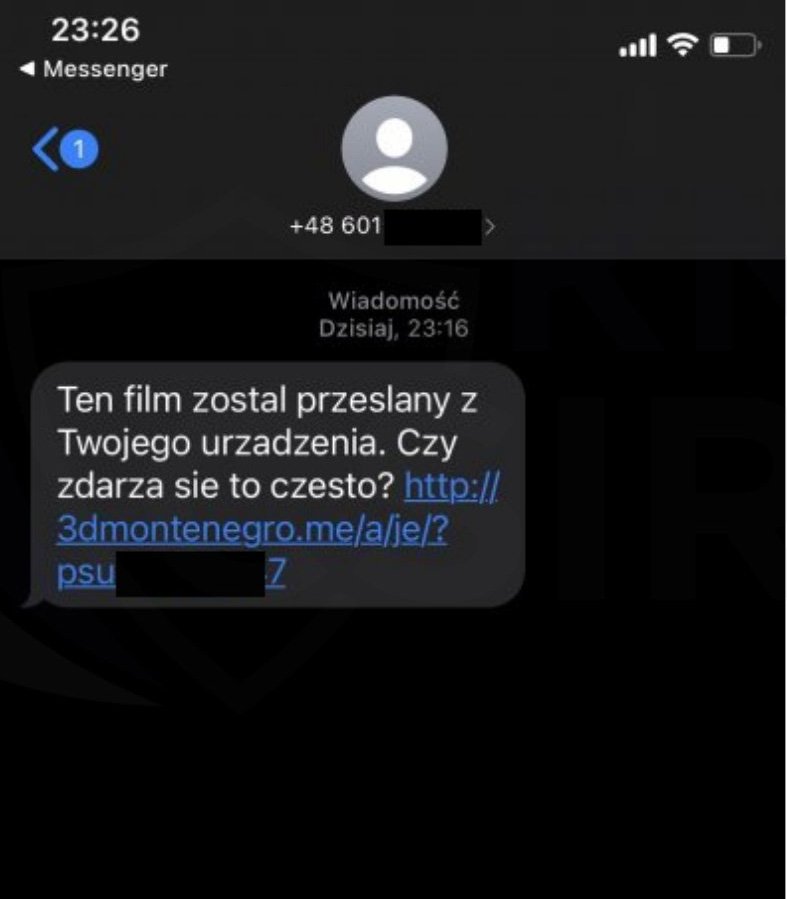
MalwareHunterTeam told Xiarch that new FluBot operations are distributed utilizing SMS texts asking the receiver if they aimed to upload a video from the device. An example of this operation’s SMS text targeting Polish receiver was transmitted was shared by CSIRT KNF, as given below:
When the receivers tap on the included link, they are brought to a page offering a fake Flash Player APK that installs the FluBot malware on the Android device.
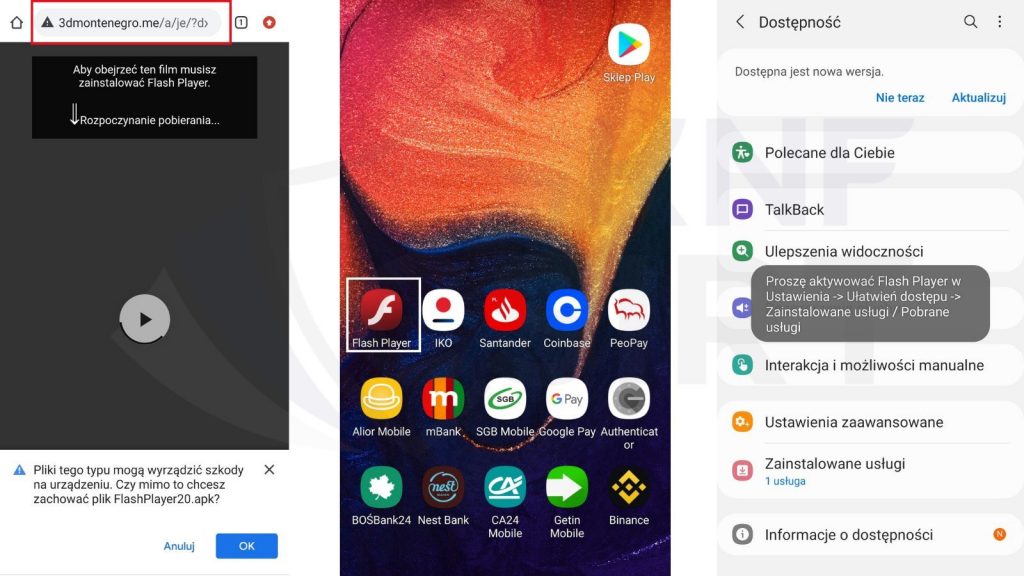
Android users should always avoid installing apps from APKs hosted at remote sites to protect themselves from malware. This practice is especially true for well-known brands, like Adobe, whose apps should only be installed from trusted locations.
What are the Advance features in Update FluBot Versions?
The most recent major release is version 5.0, which came out in early December 2021, while version 5.2 saw the light only a few days ago. With this release, the DGA (domain generation algorithm) system received much attention from the malware authors, as it’s vital in enabling the actors to operate unobstructed.
DGA generates many new C2 domains on the fly, making mitigation measures such as DNS blocklists ineffective. In its newest version, FluBot’s DGA uses 30 top-level domains instead of just three used previously and also features a command that enables attackers to change the seed remotely.
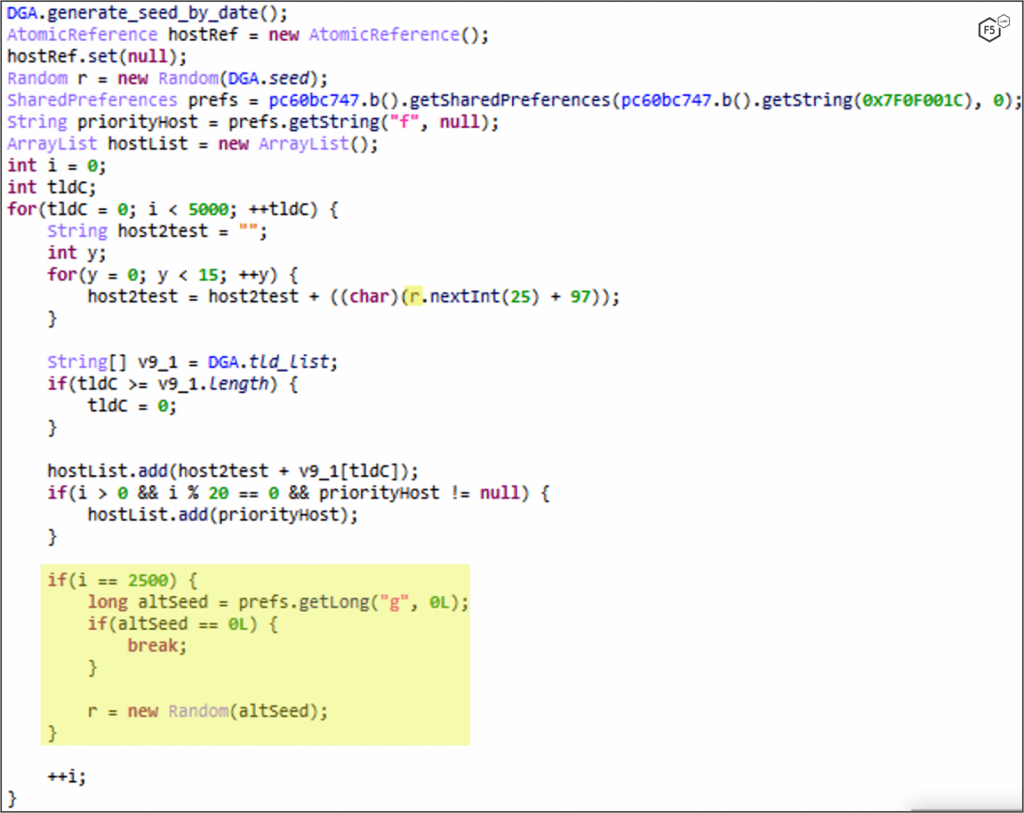
On the communication side, the new FluBot now connects to the C2 through DNS tunneling over HTTPS, whereas previously, it used direct HTTPS port 443. The commands added on the malware in versions 5.0, 5.1, and 5.2, are the following:
- Update DNS resolvers
- Update the DGA seed remotely
- Send longer SMS messages using multi-part division functions
Along with the above, the latest version of FluBot retains the capability to:
- Open URLs on demand
- Get the victim’s contact list
- Uninstall existing apps
- Disable Android Battery Optimization
- Abuse Android Accessibility Service for screen grabbing and keylogging
- Perform calls on demand
- Disable Play Protect
- Intercept and hide new SMS messages for stealing OTPs
- Upload SMS with victim information to C2
- Get the list of apps to load the corresponding overlay injects
In summary, FluBot hasn’t deprecated any commands used in previous versions and only enriched its capabilities with new ones.



