Hackers are rapidly using the Telegram messaging application as the command-and-control server that transmitted the malware into the organizations that may lead and steal the confidential user’s data from the targeted systems.
According to the security researcher, Telegram is not even installed or used but their system permits the attackers to transmit the malicious commands and executed the operations remotely as an instant messaging application. The researcher also identified that more than 130 attacks in the past 3 months are executed with the help of this multi-functional remote access trojan named Toxic Eye.
However, the attackers may use Telegram while facilitating the malicious activities which is not a new issue. If we talk about the information stealer dubbed malware named Masad Stealer was also founded while transmitting the information and cryptocurrency wallet data from the victim’s computer to Telegram with the help of exfiltration channel in September 2019. Although last year the Magecart group also used the same techniques that were further transmitted and hijacking the payment details of infected websites of the attackers.
How this All Begin?
The entire strategy was also executed in several ways and the Telegram is not the only application that was blocked by the organizations and other antivirus engines. The other messaging applications also grant the hackers while hiding their identity and giving them a link of the registration process that only needs a mobile number of the infected devices from the virtual location situation across the world.
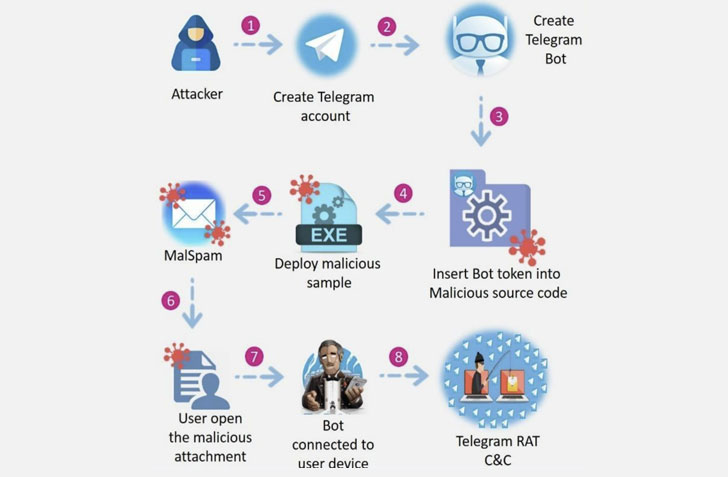
Meanwhile, the latest campaign was identified by the experts that spread from different phishing emails that were embedded in multiple malicious Windows executable files. Therefore, the Toxic eye malware occupies the Telegram while communicating and uploading the data and using the Telegram as a command-and-control server. The malware also capable to hijacks user data, delete files, terminated processes and transfers files, hijacks computer microphones, and also capable to record or store audio, video, or encrypted files while demanding ransomware.
Whereas, these types of chain attacks also commence while creating of Telegram bot by the hackers. They also embedded the RAT configuration file before compiling it into the non-executable file. After that, the .exe file is injected and embedded in a word document that opened, downloads, and runs the Telegram RAT.
Summering Up
The experts also said that we also founded the rapidly increasing trend where the malware and the authors use the Telegram platform as an out-of-the command-and-control system while the distribution of malware into the organizations. They added that the attacker is manipulating the Telegram messaging application and used it as performing the cyber attacks and overlaps the security methods.



